Synopsis:
- Introduction
- What is Thick client?
- Why Thick client Penetration Testing is important?
- What are the types of architecture?
- Corporate Pen-testing approaches for Thick client
- Conclusion
- How Brisinfosec can help you?
- Curious to read our case studies?
- Last but not the least
- You may be interested in
Introduction:
Various people use various applications for getting their various needs done. Amongst those applications that’re used, the most prominent one’s are thick-client applications.
It may seem sarcastic but it’s the truth. Still, there are some people who believe thick-clients are applications that’re being deployed with the best security features. Hence, they speculate that these applications don’t require any penetration testing. But, the truth is, it isn’t! Then, what exactly is thick-client? Well, this blog will give you a crystal-clear picture of it!
What is Thick client?
A Thick client is a software that works with or without internet. For example, Let’s consider Skype desktop application which utilizes the system resources to run (Thick client) whereas Skype web version utilizes the resources from the Skype server (Thin client). Thick client application generally consumes more memory. Also, when a thick client is connected to a network, it is considered to be a client where the server gives files and programs to process. Thick clients are often used as In-house applications and are largely independent.
Eg: Microsoft’s Word is available as executable, and also available in cloud.
Why Thick Client Penetration Testing is important?
As people in this digital world are extremely addictive towards android and web applications, security issues need to be prioritized, identified and remediated in order to ensure the CIA (Confidentiality, Integrity and Availability) triad. Moreover, these applications become matured in this security cycle.
Well, then what about thick-clients?
Still, some organizations are highly dependent on thick-client applications. Yet, there are no proper security standards for thick-client penetration testing. Hence, it has become more difficult for organizations to identify and eliminate the security flaws in it. A skilled reverse engineer or an attacker, if exploited a buffer overflow vulnerability in thick-client, can easily cause a data breach.
What are the types of Architecture?
Thick client generally has 2 types of architecture. They are
- Two-Tier Architecture
- Three-Tier Architecture
Two-tier architecture:
In two-tier application, the client directly communicates with the database/server through HTTP or HTTPS protocol. Though this type of architecture is easy to implement as it offers good performance, it’s also considered to be a little risky as there’s a high possibility for intruders to gain access to the database and exploit the other traditional vulnerabilities in the thick-client.
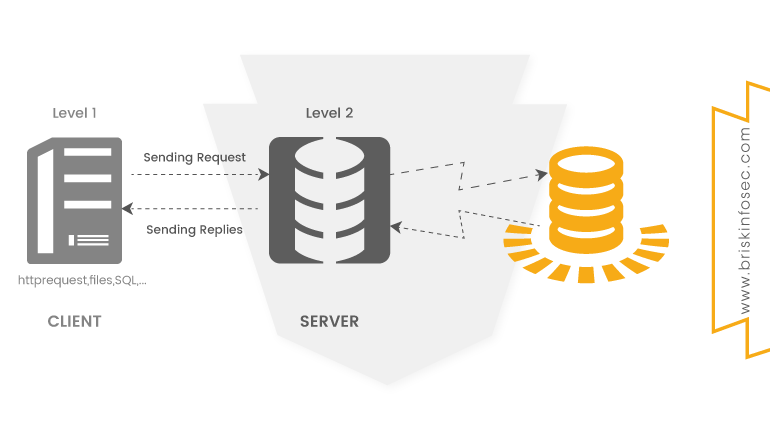
Three-tier Application:
This type of architecture is considered to be solid and secured when compared to the two-tier architecture. Here,
- The client data is first sent to the server.
- Then the query is sent to the database.
- Next, it gets processed if valid.
But, a contemporary firewall between the client and server can stall a user.
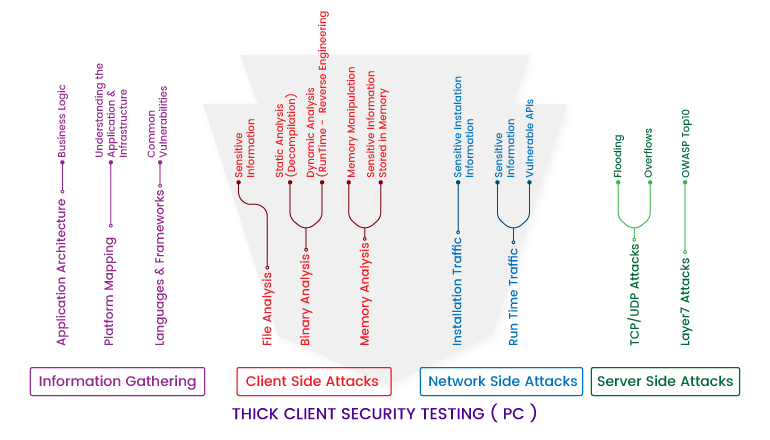
Corporate Pen-testing approaches for thick client:
Dynamic Analysis:
Dynamic testing is carried out when the application is running. Burp Suite Pro is used to intercept the backend traffic to perform web application vulnerabilities such as SQL injection, XXE and Java Deserialization attack, etc. It is less complex and does not require any bytecode, binaries or the source code (Dynamic Application Security Testing) and is easy to identify the lurking vulnerabilities at this phase.
Network Traffic Analysis:
The data transmission between the client and server is analyzed to identify, whether the traffic is encrypted or not. Some thick-client applications cannot be intercepted and these types of applications are called as Proxy un-aware Thick client applications.
Some tools to intercept Proxy un-aware thick client applications are:
- Mallory - This proxy tool comes handy to intercept TCP/UDP connections. It supports both HTTP and NON-HTTPS connection.
- Wireshark - This tool is used capture the network traffic. It’s also used to analyze the Non-encrypted connections.
- Java Snoop - It helps to attach to system processes like a bedugger. It also attempts to tamper with method calls, run custom code, or just watch what’s happening on the system.
Static Analysis:
This part mainly focuses on areas like reverse engineering, analyzing configuration files and memory level analysis to find out vulnerabilities such as Buffer overflow, License key bypassing, DDL Hijacking, Decrypting databases and etc. Tools like filemon and regmon help to identify the files that’ve been accessed recently.
Some of the commonly used tools for static analysis are:
- OllyDBG.
- IDA Pro.
- Ghidra.
- GDB.
- Radare2.
- Process monitor
- DLL hijack Auditor.
Some of the commonly used Memory Analysis tools are:
1. Winhex:
WinHex is a superior tool that’s highly beneficial for digital forensics, recovering lost data, low-level data processing, and IT security. It’s also a globally used editor through which professionals can analyze and edit different types of files, and also regain the lost data from hard drives.
2. Volatility:
It’s an open source tool that’s developed under python. It helps people to analyze system’s runtime state by using the data that’s in volatile storage (RAM).
3. Memory Analyzer:
Memory Analyzer aids in analysing Java dump files, Java heap dump files and the system dump files that contains millions of objects. This tool gives information about
- The retained sizes of the objects.
- Processes that are obstructing the objects collection.
- A report to automatically extract leak suspects.
This tool uses the IBM Diagnostic Tool Framework for Java (DTFJ) feature to enable the processing of dump files from IBM virtual machines.
Exploitation Tools:
1. Metasploit:
It’s an exploitation framework with collection of local and remote exploits, payloads and scanners, etc. It is a highly utilized tool in VAPT.
2. Veil-Evasion:
Veil-Evasion is a tool developed for creating Metasploit payloads that bypass common anti-virus solutions. You can catch sight of the Veil-Evasion’s code at https://www.github.com/Veil-Framework/Veil-Evasion/
Conclusion:
Organizations might think that thick-client Penetrating testing isn’t necessary as the application is secured. Sadly, this is the mindset that’s the major reason for increasing security vulnerabilities in it. Moreover, the fact is that, there are vulnerabilities hiding even under the deepest security layers. Hence, a proper penetration testing is not only necessary for web applications and network devices, but also mandatory for thick-client applications as well.
How Briskinfosec can help you?
Briskinfosec has an expert team of security professionals who are well versed in the field of thick-client security assessment. They’ve successfully eliminated many vulnerabilities that were existing in our clients thick-client applications. To know about it in-depth, kindly reach us out.
Curious to read our case studies?
When you think about light, you can’t forget the sun. Similarly, with regards to cybersecurity, if you want to know what a rich security quality is, you need to know the security strategies used to accomplish it. To do so, just check our case studies. They contain the successful security assessment strategies executed by our security folks to eliminate our distinguished client-side vulnerabilities.
Last but not the least:
It’s such a fantastic feeling when an unexpected moment turns into a lasting memory. You’ll experience this beautiful transition, only when you find something special. To help you get a taste of it, we hereby present you a special one of Briskinfosec that’s named as Threatsploit Adversary reports. It’s our report that contains the global collection of a month based significant cyberattacks, the impacts they’d caused and much more. Even the sane tips of how to stay secured against them are also stated by us.
Believe me pals! I’m not lying!
Instead of browsing in search engines and websites about all these in a tiresome manner, a single click on our report is more than enough. It’ll for sure become a delightful memory!


