Data in general is a set of information, knowledge, or fact that is measured and stored in storage devices. In our daily life, we access internet for sharing, purchasing, and storing data. Have you ever thought about the ‘must-be thought’ factor, “Is my personal data safe”? or does someone else own it? This blog will speak about the Data war, its potential impact and how-to safeguard you from it.
Contents:
- Is your personal data in danger
- How social media misuses your data
- Political or social manipulation
- Common mistakes companies do with data security
- How to stay safe from fraudulent data
- How to secure your users data
- Conclusion
- How Briskinfosec helps you
- Curious to see our case studies
- Last but not the least
- You may be interested on
Is your personal data in danger?
As we surf through the internet for our needs, we inadvertently leak some sensitive data such as username, passwords, bank account number etc for authentication and transaction purposes. These details somehow gets scattered in the internet and later gets exploited. In 2017, over 198 million US Voters data were leaked by an organization called as “Deep root Analytics”, due to an unsecured cloud server. I hope now a question would have aroused in your mind? Is my personal data secure or am I a victim of a data breach? In order to find it out, you can use OSINT (Open-Source Intelligence).
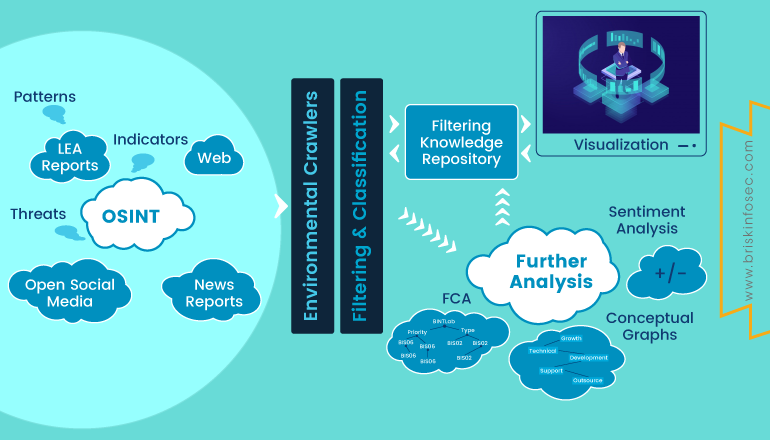
OSINT is information collected from public sources present over the internet for free. It uses sources from social networks, forums, business websites, blogs, videos, tweets, and news sources to fetch information. In order to utilize OSINT to gather information about a company or individual, one has to follow some techniques.
- Who is your target?
- What am I looking for?
- Collect employee names, job roles, as well as the software they use.
- Identify all social media used by the target Company or individual.
- Publicly accessible login pages.
- Job vacancy availability.
- Publicly disclosed HR email.
Some Popular OSINT Tool:
- Spiderfoot
- GOSINT
- Shodan
- Google Dorks
- TheHarvester
How social media misuses your data?
In 2018, Social media has been the major victim to data breaches as over 4.5 million user data were leaked. During the middle of 2018, Facebook revealed that almost 60 thousand South African Facebook user accounts were compromised. Even Google revealed that they are about to shutdown Google+ after exposing 500000 user data, due to the bug that wasn’t bothered for a long time.

Ref: https://www.emarketer.com/content/users-have-little-faith-in-social-networks-privacy-protections
Political or Social Manipulation?
-
On internet, you don’t know much about the political ads you’re shown. You often don’t know who is creating them, since the disclaimers are so small, wondering if they even exist after all. You also don’t really know who else is seeing them. Sure, you can share a political ad, thus fulfilling the advertiser’s hopes and then at least some other people you know will have witnessed the same ad. But you don’t really know if your neighbour has seen it. In addition, digital advertising companies distribute ads based on how likely you are to interact with them. This most often means that they send you ads they think you’re likeliest to engage with. They don’t determine what the nature of that engaging content might be — but they know (just as all advertisers do) that content works well if it makes you very emotional. In simple, an ad that doesn’t make you contemplative or curious, makes you elated, excited, sad or angry.
-
It could make you so angry, in fact, that you’ll share it and make others angry — which in turn gives the ad free publicity, effectively making the advertiser’s purchase cheaper per viewer, since they pay for the initial outreach and not for the shares.
-
Social media giant like Facebook fell prey to the Cambridge Analytica scandal, which helped Donald Trump to win the throne. Over 50 million Facebook user’s data were in the hands of Cambridge Analytica, which was used to favour U.S president Donald Trump by manipulating American voters. Facebook accepted that they used “thisisyourdigitallife” app to get data from users and sold it for Trump campaign. This conspiracy dropped a bombshell among Facebook users. Facebook is a behemoth of social media platforms.
Common mistakes company do with data security
Maintaining the sensitive data secure and vulnerability free is a tough challenge. Though implementation of security is prevalent on all sides, still hackers are able to steal the data from the individual or from the company. By following few methods, data securities can be achieved.
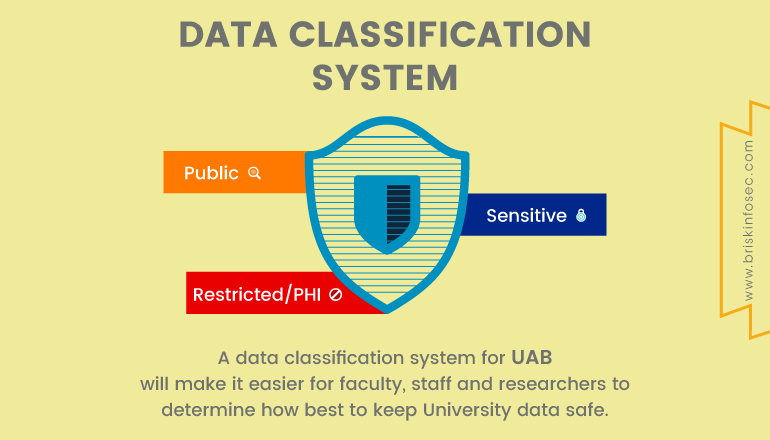
Data Classification:
Before a company attempts to secure their data, first they should understand the sensitivity of the data and create a corresponding data classification policy. The data classification policy can be split into three levels.
Restricted:
Data at this level is considered to be a sensitive one and it could cause great risk, if compromised. Access is on a ‘need-to-know’ basis only.
Confidential:
Data at this level is considered to be less sensitive than the restricted data. Here, the data is only accessible by the personnel. If this data gets leaked, it would cause minimum damage.
Public:
This data is less sensitive and even if compromised, it doesn’t cause any damage to the organization.
Encryption:
Everything that is shared over the internet should be encrypted. Company should follow strong encryption mechanism and proper key management.
Cloud Misuse:
There is a myth among people that data stored in the cloud is safe and secure, but it isn’t because you are storing your data on someone else computer. Best thing to secure your data is to encrypt it before uploading on the cloud. Before sharing your key with your cloud provider, review the cloud provider’s policies.

Train Up your Staffs:
Training your employee about data security is a crucial step in building your infra. Educate each and every member in your organization. There should be a compliance expert to manage and guide.

How to stay safe from fraudulent data:
-
Keep your software up to date and deploy the most contemporary anti-virus.
-
Always, make sure that you’re connected to Https:// URL to make secure online transactions.
-
Be cautious of suspicious e-mails from unknown sources. Don't open e-mails with attachments if you don't know the sender.
-
Use a firewall to assist in blocking dangerous programs, viruses or spyware before they infiltrate your system.
-
Avoid accessing unwanted websites that may lead to drive-by download attack.
-
While using third party computers or mobiles for browsing, use the private/incognito mode.
How to secure your users Data:
Enable brute-force protection:
-
10 consecutive failed login attempts for the same user, just block the IP address.
-
Send a notification email to the user.
-
Block the suspicious IP address for that user.
Enable breached password detection
-
Send an email to the affected user.
-
Block login attempts for suspected user accounts using that username and password combination.
Help your users choose better passwords
-
A strong password must contain a number, special character and should be case sensitive. You can also forbid the use of previous passwords using Password History feature and stop users from choosing common passwords using our password dictionary.
Conclusion:
In this blog, we saw how user’s personal data is misused. It clearly shows, how valuable each and every data is and how it can be used to manipulate people’s mind. In order to avoid exposing your sensitive data over internet, cyber security awareness should be created among people.
How Briskinfosec helps you:
A silent warzone, but with violent impacts is being produced every day in these modern times of cybercrimes. Security was never an option but has ever been a compulsion which demands the best quality implementation for digitalised businesses to attain their perfection, in terms of CIA consideration. Due to complacency, many firms misjudge their security status is firm. When cyberattacks strike, their notions just take a beating. How assured are you about your systems and their capabilities?
Does all this appeal entangled?
Never relinquish! Briskinfosec’s eminent cyber security services will make you to cherish!
Briskinfosec strengthens the attack surfaces of your organisation by its security assessment services. Further, Briskinfosec also provides training to both novice and veterans about cyberattacks and best steps to escape from them. We offer workshops regularly for corporates to enlighten everyone about cyberwar and the need to be aware of these.
Curious to see our Case study?
Case studies are the best examples to prove the security assessment skill of a company. We have a wide array of case studies done for various security sectors to many of our honourable clients. Check them out to acknowledge the way we sorted out the vulnerabilities.
Last but not the least:
Briskinfosec prepares Threatsploit Adversary Report on a monthly basis, by encompassing various global cyberattacks and its impacts on the respective company. In spite, of searching sporadically in search engines, just a single click on our Threatsploit report is more than enough. You’ll be amazed, as what you’ve bought is a billion could’ve never got.


