Cybersecurity starts from proper awareness. Briskinfosec BINT LAB cybersecurity researchers continuously put extraordinary effort to help you to realise cybersecurity better and faster. Just download the Threatsploit Adversary Report.
Millions of credit card records are compromised annually due to data breaches, leaving businesses facing financial ruin and shattered reputations. But there's hope! Payment Card Industry Data Security Standard (PCI:DSS) framework outlines comprehensive security requirements to safeguard cardholder data throughout its entire journey, from collection to storage and transmission.
To achieve PCI:DSS compliance and boost your brand's credibility, start by assessing your organization's current compliance level. Compliance levels are determined by the volume of credit card transactions processed annually.
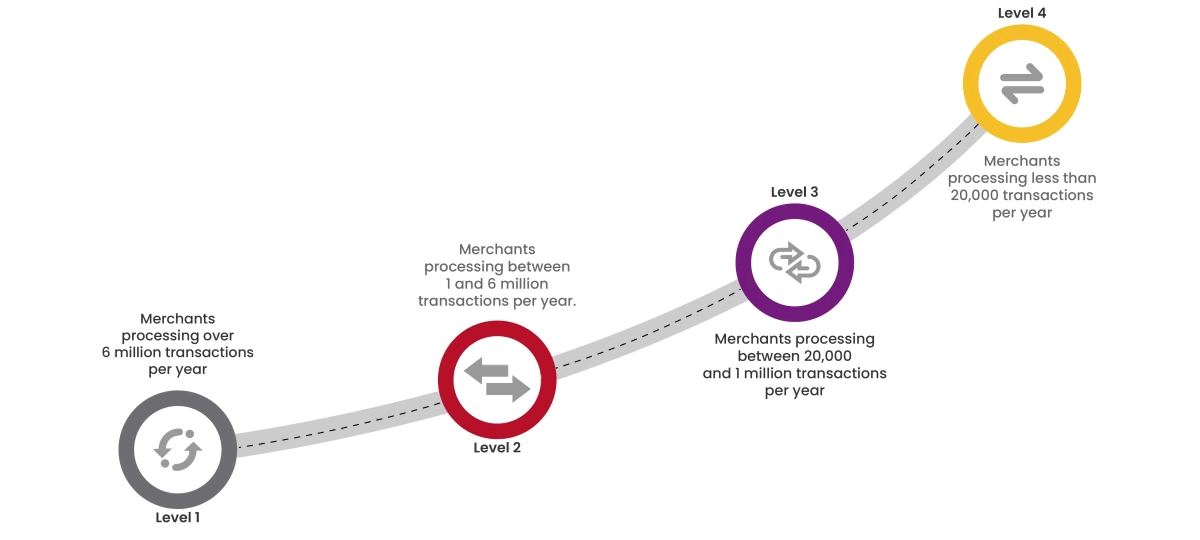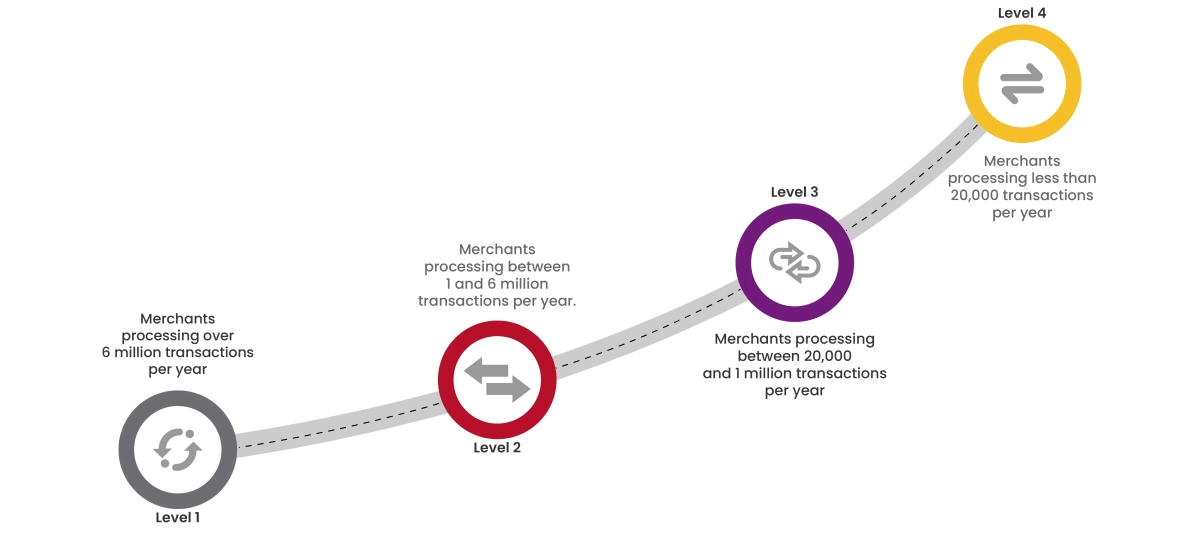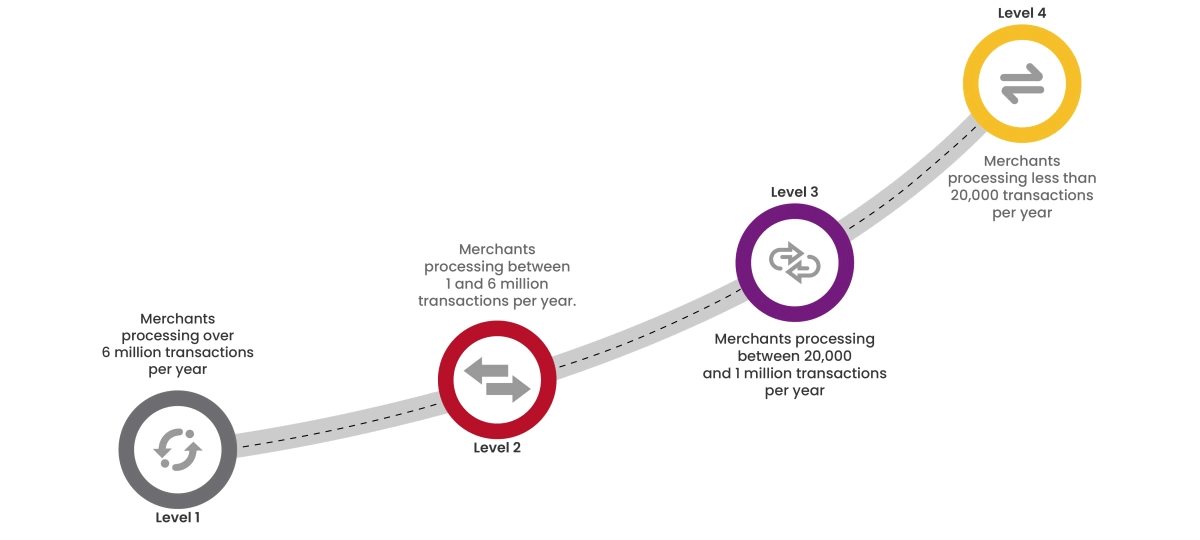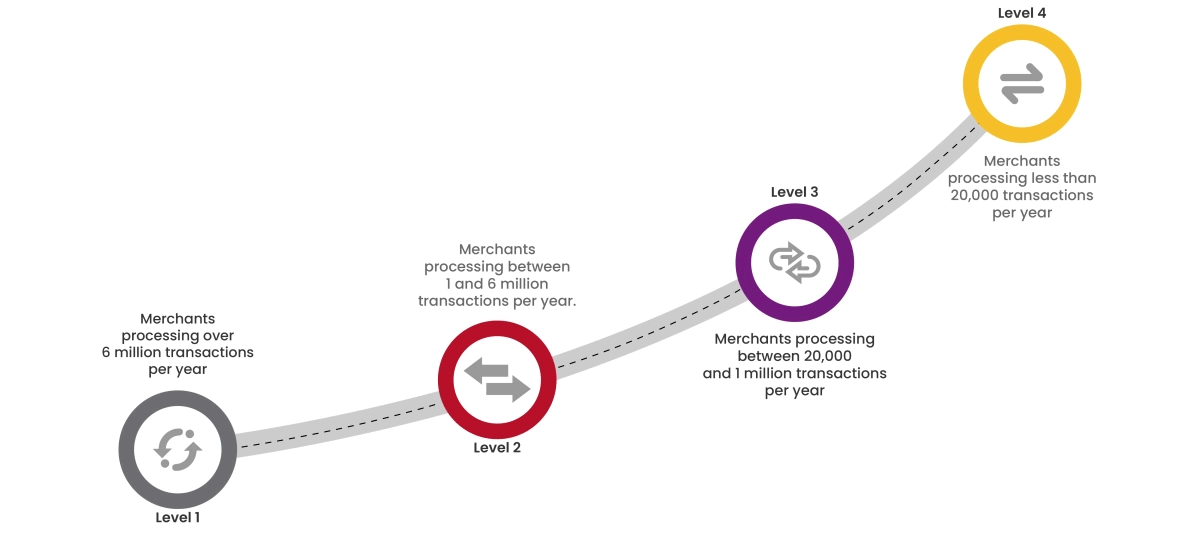
Cybersecurity starts from proper awareness. Briskinfosec BINT LAB cybersecurity researchers continuously put extraordinary effort to help you to realise cybersecurity better and faster. Just download the Threatsploit Adversary Report.
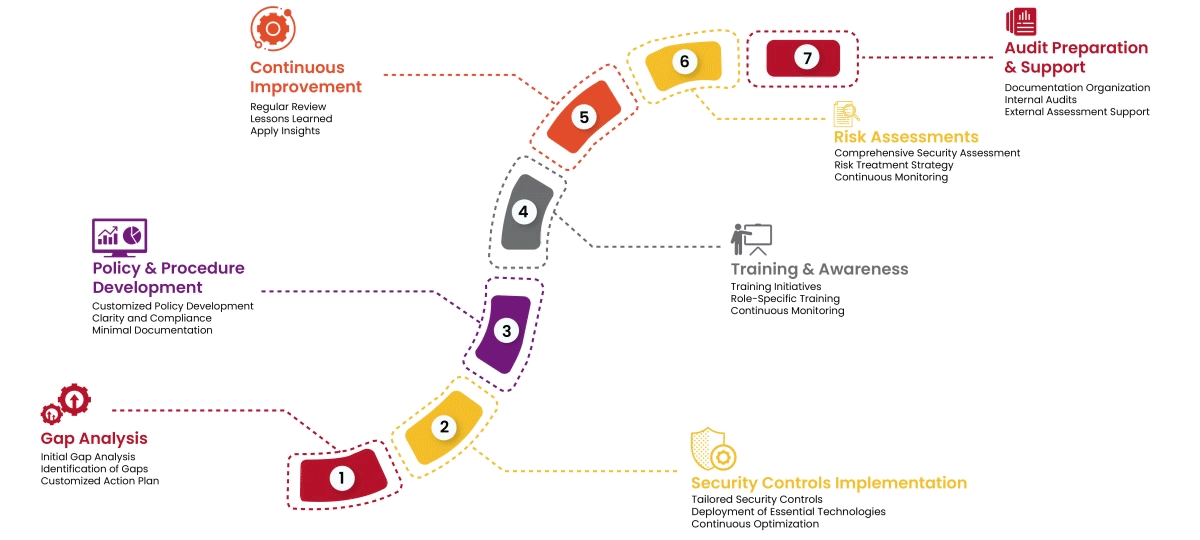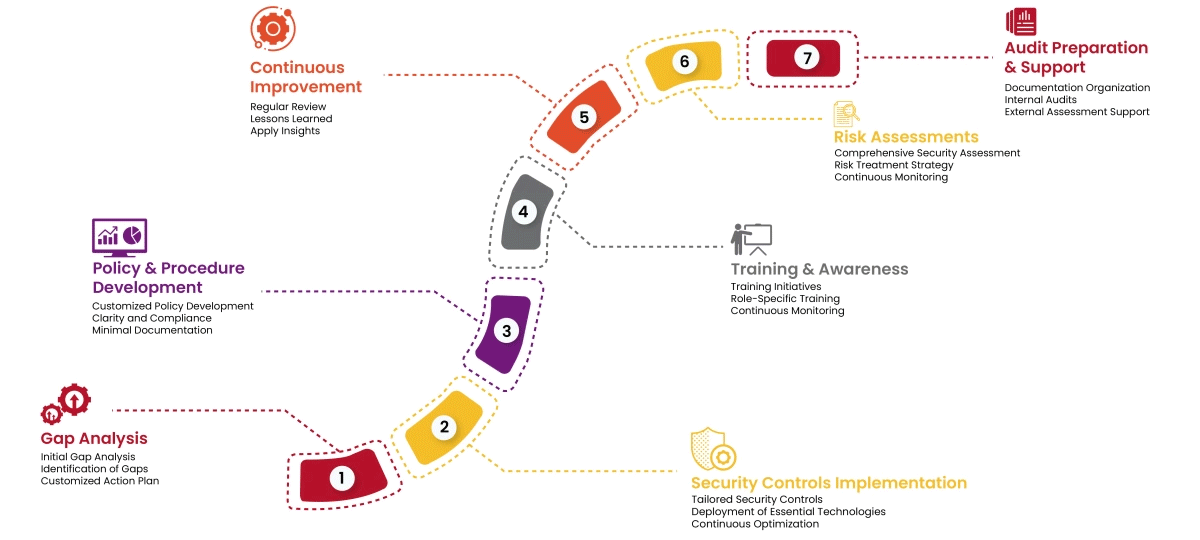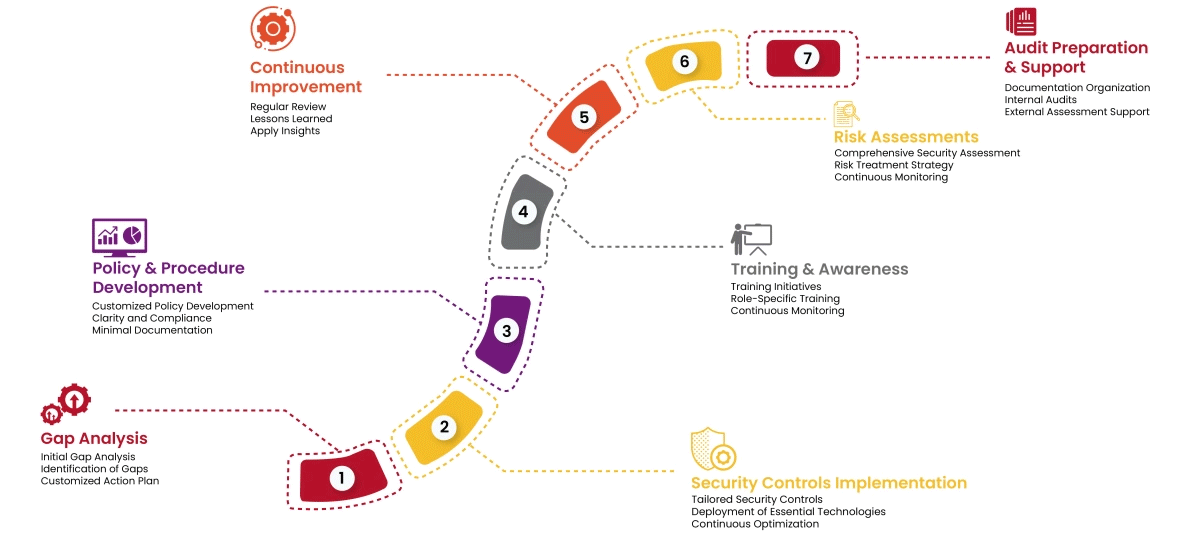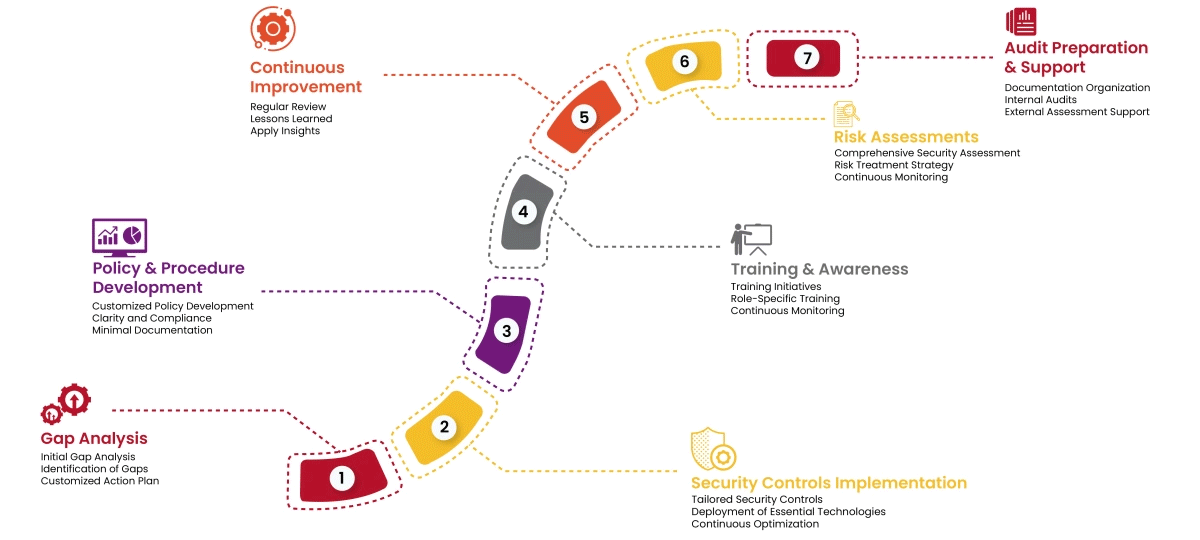
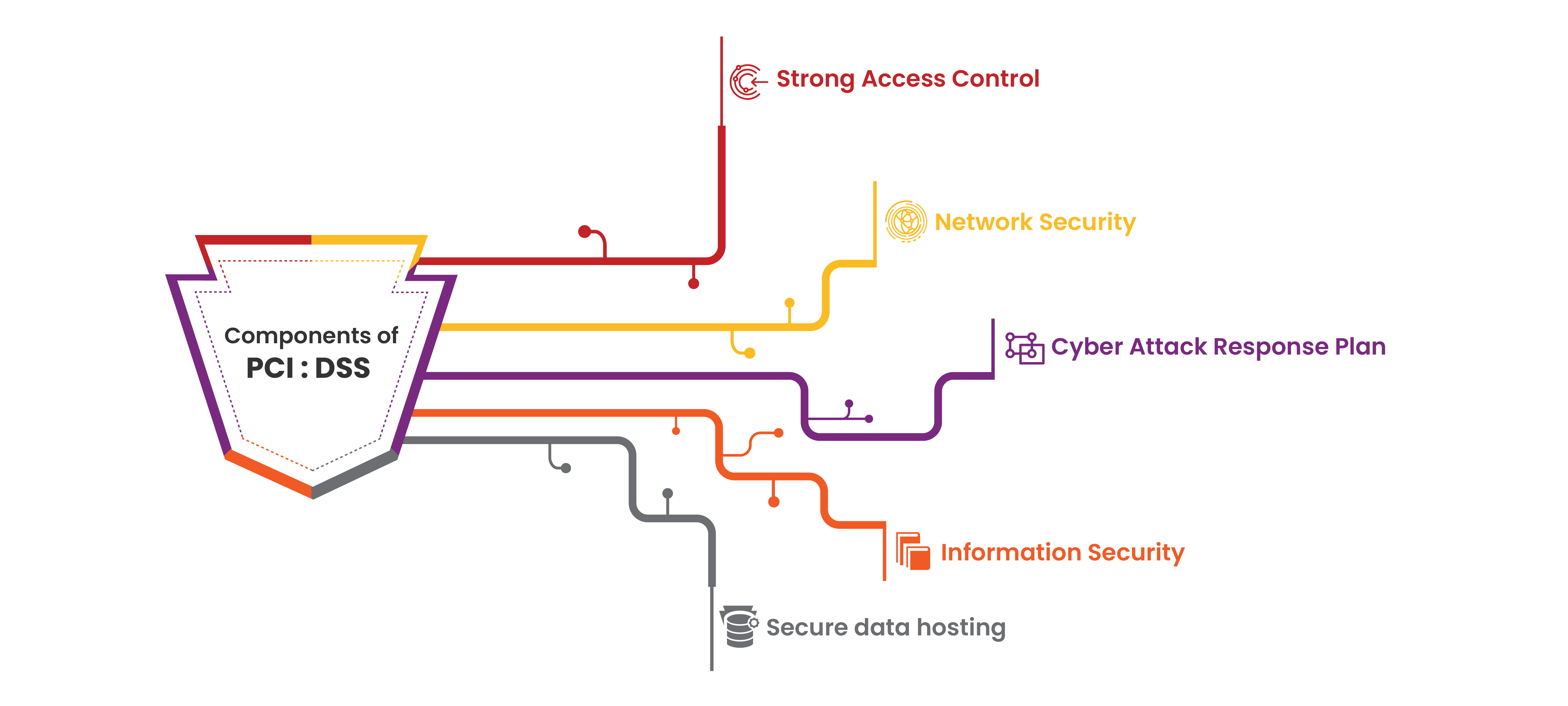
Our approach mitigates PCI:DSS risks by making compliance straightforward and cultivating a data-centric security culture within your organization. Here's how we achieve this:
Tackle the world's toughest business challenges with proven information management solutions and services
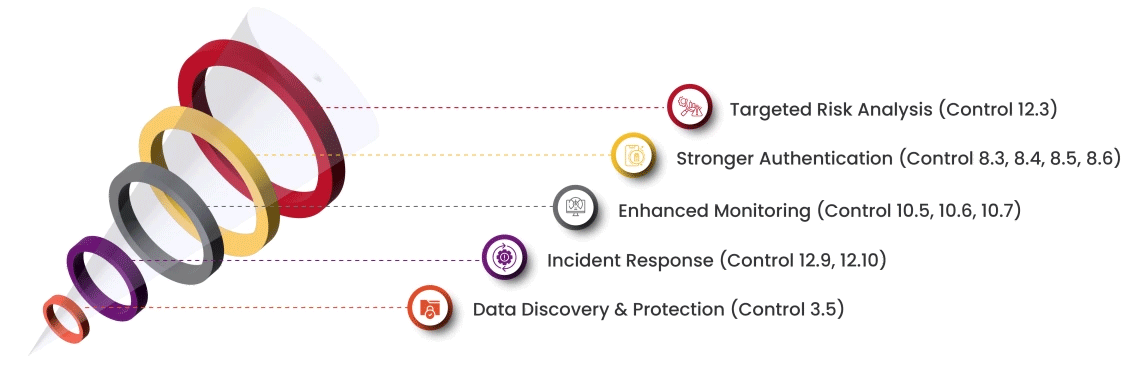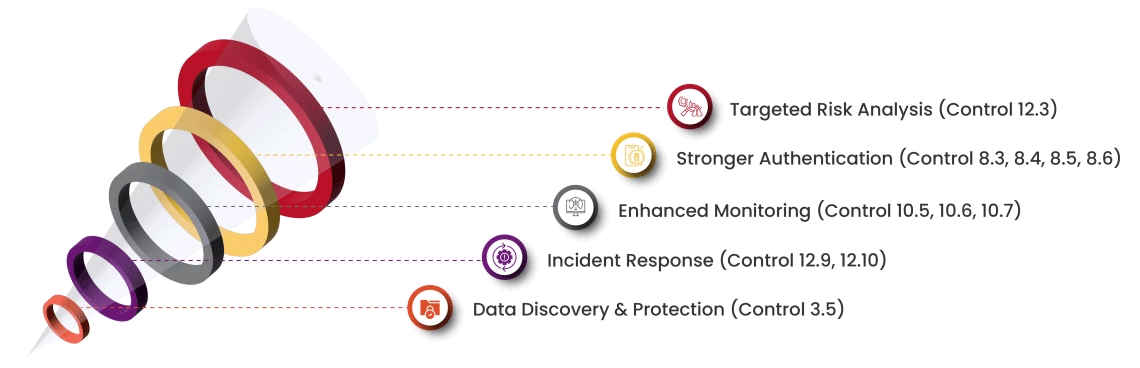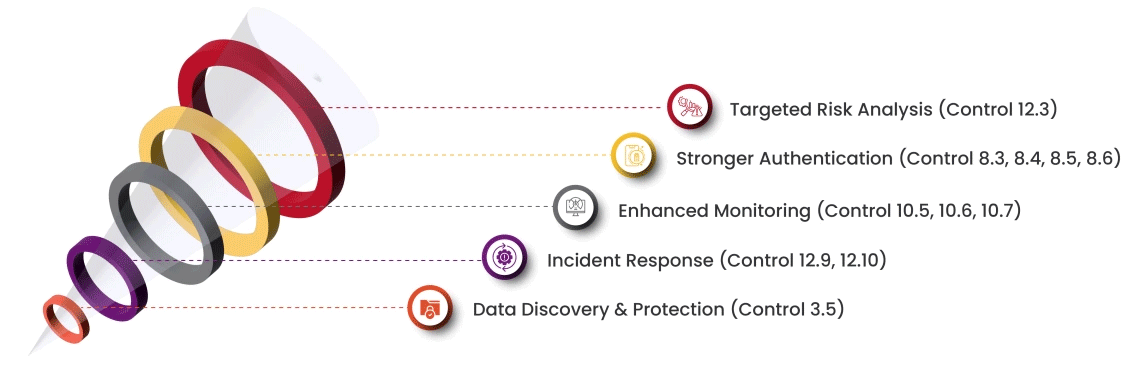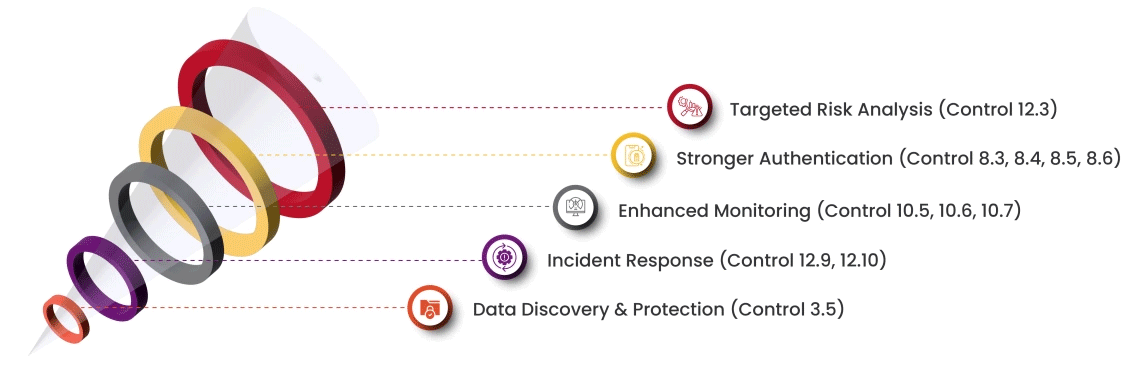
Streamline your PCI compliance journey with our expertise, ensuring a smooth transition and unlocking the benefits of the latest standard.
Is your company listed in these categories? We provide comprehensive services for PCI:DSS compliance ensuring unbreakable security measures across diverse industries.Contact us today to safeguard your business with unbreakable security solutions.
By implementing these robust security measures, organizations can achieve PCI:DSS compliance and gain the dual benefits of safeguarding sensitive customer data while building trust and credibility with their clients.
Let's discuss your unique requirements and craft a customized PCI:DSS compliance strategy that fosters peace of mind and positions your organization for success in the digital age.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book an AppointmentCelebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Elevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book an Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.