If we discuss about injection vulnerability, SQLi is a type of injection vulnerability, SQLi, allows an attacker to alter, steal or even delete the data in the backend database by exploiting the SQLi vulnerability Because SQL Database is so widely used, it poses a serious risk to a wide range of software and websites around the world.
Contents
- What is Injection Attacks?
- Most Common Types of Injection Attacks?
- What is a SQL Injection?
- Types of SQL Injection
- Tools to Find SQL Injection Attacks
- Addons and Extensions to Find SQL Injection vulnerability
- Exploiting SQL Injection Vulnerability Using Burp Suite Tool
- Manual testing for SQL injection flaw
- Remediation Measures to Prevent SQL Injection Attack
- Conclusion
What is Injection Attack?
When it comes to web security issues, injection vulnerability is one of the oldest and most common issues. It has been at the top of the OWASP Top 10 list of web application security risks since 2003. This type of attack is considered the most dangerous because it allows an attacker to inject malicious code that runs through an application to another system (normally an Interpreter). Attacks on the operating system, external programmes, and the backend database are all part of these attacks.
Most Common Types of Injection Attacks?
Aside from SQL injection and Cross-Site Scripting, injection attacks are not limited to these two categories. The following attacks come in a variety of shapes and sizes as well. Vulnerabilities involving injection that can be dangerous.
Code Injection
It is possible for an attacker to take advantage of a flaw in the application's input validation by executing malicious code via an injection vulnerability known as Remote Code Execution (RCE) or Code injection. The server-side interpreter for that language is responsible for executing the code injected into the target application (e.g. PHP, Python, JAVA, Perl, Ruby, etc.).
Impact: Full System gets compromised.
CRLF Injection
CRLF injection the word CRLF refers to Carriage Return (ASCII 13, \r) Line Feed (ASCII 10, \n) characters is used to denote the termination of a line. If an attacker can inject the CRLF characters into a web application, for example through a user input form or an HTTP request, then they have exploited a CRLF injection vulnerability.
Impact: It may cause a Cross-Site Scripting attack.
Email Header Injection
Email Header Injection is very similar to CRLF injections. The attacker sends IMAP/SMTP commands to a mail server that is not directly available via a web application.
Impact: Spam Relay, Information Disclosure
Host Header Injection
Host Header Injection value in the HTTP request determines that, which website or web application should refer to. An attacker tampers the Host Header value in an incoming HTTP request and inject his/her malicious value that will perform nefarious actions if executed (e.g. injecting a crafted phishing domain in Host Header value). It mainly occurs due to improper input filtering.
Impact: Password Reset, Web Cache Poisoning, URL Redirection
LDAP Injection
The attacker injects LDAP (Lightweight Directory Access Protocol) statements to execute arbitrary LDAP commands. They can gain permissions and modify the contents of the LDAP tree.
Impact: Authentication Bypass, Privilege Escalation, Information Disclosure.
OS Command Injection
OS Command Injection or shell injection is a web security vulnerability that allows a remote attacker to execute arbitrary Operating System (OS) level shell commands on the server that is running an application. It is a rare case vulnerability, Command injection occurs only when the web application code includes operating system call and user input is used in the call.
Impact: Full System Compromise.
HTML Injection
HTML Injection (HyperText Markup Language injections) are vulnerabilities that are very similar to XSS attacks. The delivery mechanisms are exactly the same but the injected content is pure HTML tags, instead of scripts like in the case of XSS. HTML injections are less dangerous than XSS but they may still be used for malicious purposes.
Impact: URL Redirection, Website Defacement, Content Modification, Phishing Attacks (Injecting crafted Fake Login portals)
XPATH Injection
In XPath injection, the attacker injects data into an application to execute crafted XPath queries. They can use them to access unauthorized data and bypass authentication.
Impact: Information Disclosure, Authentication Bypass.
What is a SQL Injection?
SQL injection is an attack where an attacker persuades to inject his malicious SQL code into someone’s database and then executes it to launch his SQL attacks. This could potentially ruin the database tables of the victim, and can even compromise his sensitive and other important data. In this blog, we will see how we can identify SQL injection using Burp Suite. Burp Suite is a Proxy interceptor tool specifically used by penetration testers for web application penetration testing.
Risk Factors
The platform affected can be:
- Language: SQL
- Platform: Any (requires interaction with a SQL database)
Impact
A successful SQL injection attack may lead to,
- Authentication Bypass
- Data Loss
- Modification, Corrupting or Deleting the data
- Remote Code Execution
- In the worst case, it will make way to an entire system compromise threat. (When performing Privilege Escalation to gain Root access).
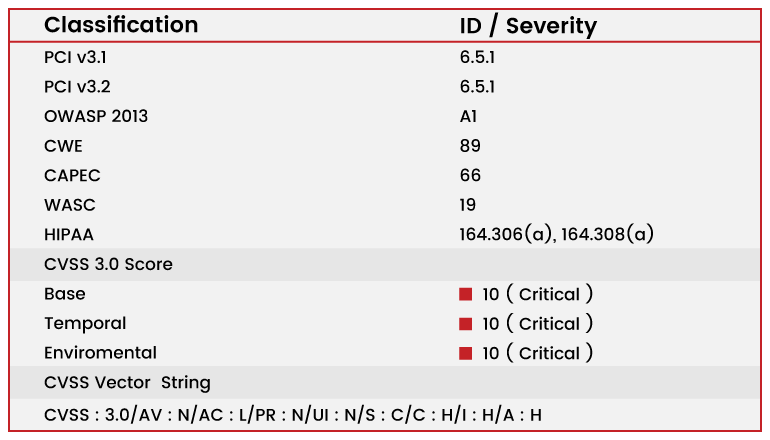
Vulnerability Classification and Severity Table
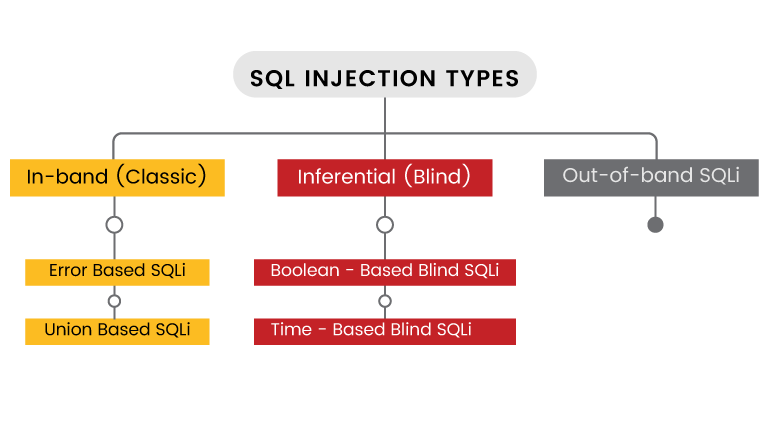
Types of SQL Injection
SQL Injection can be classified into three major categories – In-band SQLi, Inferential SQLi, and Out-of-band SQLi.
Error-Based SQL Injection
This technique relies on error messages thrown by the database to obtain hints about the DB structure. The attacker sends a malicious query to the database which results in errors. On a live site, errors should be disabled or it should be generic (that should not reveal any hints to the attacker about the DB.)
Example: www.vuln-web.com/photo.php?id=1′
The above query will result in a syntax error and might reveal the backend database type, version info etc.
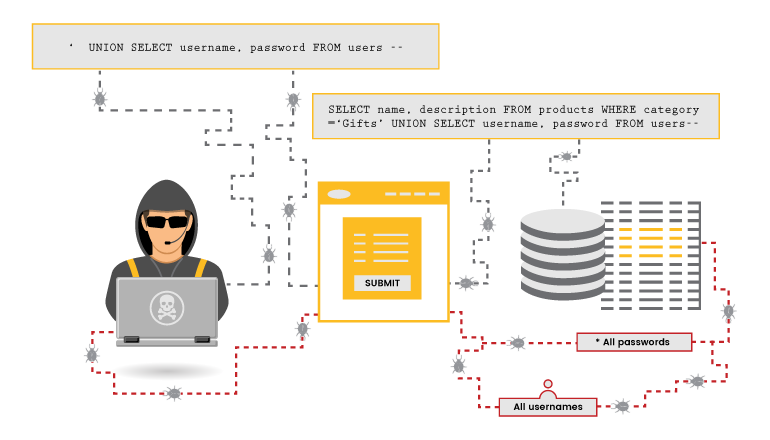
Union-Based SQL Injection
This technique uses union command in SQL query to execute additional queries; thereby, modifying, inserting, deleting or dropping the contents of the table.
Example: Query : Select table_schema from information_schema.schemata
Injection: http://fakesite.com/report.php?id=-23 union select 1,2,version(),4,5–+
An attacker can view the Database information from the webpage itself by simply injecting the malicious queries in the URL request.
Boolean-Based SQL Injection
In some case, there is no visible error message on the page when an SQL query fails, making it difficult for an attacker to get information from the vulnerable application. However there is still a way to extract information.
When an SQL query fails, sometimes some parts of the web page disappear or change, or the entire website can fail to load. These indications allow attackers to determine whether the input parameter is vulnerable and whether it allows extraction of data.
Attackers can test for this by inserting a condition into an SQL query:
https://example.com/index.php?id=1+AND+1=1
If the page loads as usual, it might indicate that it is vulnerable to an SQL Injection. To be sure, an attacker typically tries to provoke a false result using something like this:
https://example.com/index.php?id=1+AND+1=2
Since the condition is false, if no result is returned or the page does not work as usual (missing text or a white page is displayed, for example), it might indicate that the page is vulnerable to an SQL injection.
Here is an example of how to extract data in this way:
https://example.com/index.php?id=1+AND+IF(version()+LIKE+'5%',true,false)
With this request, the page should load as usual if the database version is 5.X. But, it will behave differently (display an empty page, for example) if the version is different, indicating whether it it is vulnerable to an SQL injection.
Time-Based SQL Injection
This technique relies on sending an SQL query to the database which forces the database to wait for a specified amount of time (in seconds) before responding. The response time will indicate to the attacker whether the result of the query is TRUE or FALSE. If a time delay is observed, one can conclude that the input syntax used can be utilized for further elaborate injections.
Example: If the first letter of the first database’s name is an ‘A’, wait for 10 seconds.
http://www.site.com/vulnerable.php?id=1' waitfor delay '00:00:10'--
This is a time consuming process.
Out-of-Band SQL Injection
Out-of-Band SQL Injection is not very common, mostly because it depends on features being enabled on the database server being used by the web application. Out-of-band SQL Injection occurs when an attacker is unable to use the same channel to launch the attack and gather results.
Out-of-band SQLi techniques would rely on the database server’s ability to make DNS or HTTP requests to deliver data to an attacker. Such is the case with Microsoft SQL Server’s xp_dirtree command, which can be used to make DNS requests to a server an attacker controls; as well as Oracle Database’s UTL_HTTP package, which can be used to send HTTP requests from SQL and PL/SQL to a server an attacker controls.
Tools to Find SQL Injection Attacks
Some of the Best Free Open source Tools and scanners to find SQL Injection vulnerability are as follows,
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester, and a broad range of switches including database fingerprinting, over data fetching from the database, accessing the underlying file system, and executing commands on the operating system via out-of-band connections.
jSQL Injection is a lightweight application used to find database information from a distant server. It is free, open source and it works cross-platform on Windows, Linux and Mac OS X with Java from version 8 to 15. Kali Linux logo jSQL Injection is also part of the official penetration testing distribution Kali Linux and is included in various other distributions like Pentest Box, Parrot Security OS, ArchStrike and BlackArch Linux.
Burp Suite is an Application layer intercepting proxy tool that captures HTTP request and analyzae the flow of the application or website to check for vulnerabilities. It is designed to be used by hands-on testers to support the testing process. With a little bit of effort, anyone can start using the core features of Burp to test the security of their applications.
Sqlninja is a tool targeted to exploit SQL Injection vulnerabilities on a web application that uses Microsoft SQL Server as its back-end. Its main goal is to provide a remote access on the vulnerable DB server, even in a very hostile environment.
Whitewidow is an open source automated SQL vulnerability scanner that is capable of running through a file list, or can scrape Google for potential vulnerable websites. It allows automatic file formatting, random user agents, IP addresses, server information, multiple SQL injection syntax, and a fun environment.
Addons and Extensions to Find SQL Injection vulnerability
Hackbar addon is a simple Mozilla extension which can be used by newbies and helps in testing simple SQL as well as XSS holes to easily test the existence of any form of vulnerabilities. It’s an encryption and encoding tool which helps in testing XSS vulnerability and supporting keyboard shortcuts in performing various tasks. Since you can send post data to bypass client side validations, can effectively be used in determining POST XSS vulnerabilities.
Websecurify is a powerful cross platform web security testing tool. It’s available for various desktop, mobile platforms and browsers. This is the first web security tool that runs directly from the browser. It’s capable of finding XSS, XSRF, CSRF, SQL Injection, File upload, URL redirection and various other security vulnerabilities. It has a built in crawler that scans and crawls pages. Then it will try to find vulnerability on pages. It’s not a fully automatic tool. It lists possible vulnerability on the URL. You will need to confirm the vulnerability manually. While scanning, it pulls all features from the WebSecurify server, so you do not need to worry about database updates. The vulnerability engine will be updated at all times. Penetration testing tools are just a click away. Use this either as a browser tool or desktop tool.
Tamper Data is similar to the Live HTTP Header add-on but, has header editing capabilities. With the tamper data add-on, you can view and modify HTTP/HTTPS headers and post parameters. Thus it helps in security testing web application by modifying POST parameters. It can be used in performing XSS and SQL Injection attacks by modifying header data.
Let’s see an example of exploiting SQLi vulnerability using the Burp Suite Tool.
Exploiting SQL Injection Vulnerability using Burpsuite Tool
First, ensure that Burp Suite is correctly configured with your browser.
- Next, visit the web page of the application that you are testing.
- Then, return to Burp Suite and ensure “Intercept is on” in the Proxy “Intercept” tab.
- Now send a request to the server. In this example, by clicking the “Submit” button, it can be done.
- The request will be captured in the Proxy “Intercept” tab.
- One way to test an application for SQL injection vulnerabilities is to send the request to Burp Suite -Scanner.
- Right click anywhere on the request to bring up the context menu.
- Click “Do an active scan” for performing a scan.
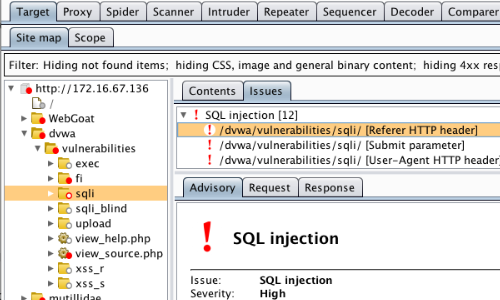
- Once the scan is complete, go to the Target “Sitemap” tab.
- In this example, the Scanner has found a number of SQL injection issues.
- Click on an individual issue to view the “Advisory” tab, which provides details about each specific vulnerability.
- You can also view the requests and responses on the basis of which Burp Suite has reported the issue.
Manual testing for SQL injection flaws
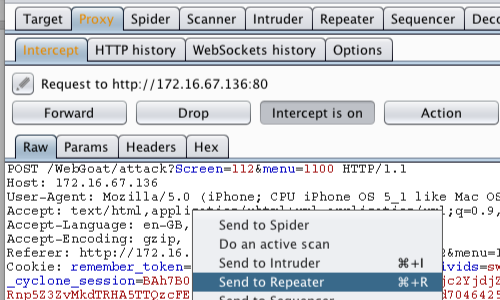
- The request will be captured in the Proxy “Intercept” tab.
- Right click anywhere on the request to bring up the context menu and click, “Send to Repeater”.
- Go to the “Repeater” tab.
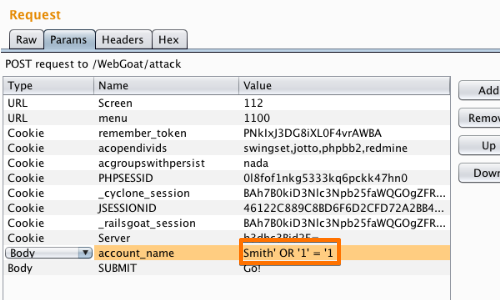
- Here, we can input various payloads into the input field of a web application.
- We can test various inputs by editing the values of appropriate parameters in the “Params” tabs.
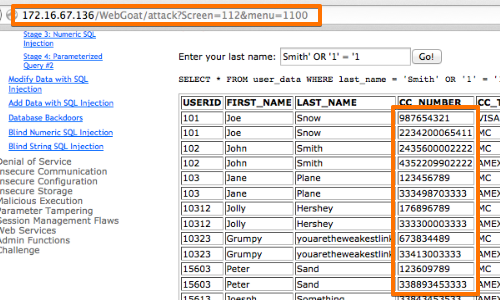
- In this example, we are attempting to reveal the credit card details held by the application.
- Smith’ OR ‘1’ = ‘1 is an attempt to alter the query logic and reveal all the user information held in the table.
- The response can be viewed in the “Response” panel of the Repeater tool.
- Responses that warrant further investigation or confirmation can be viewed in your browser.
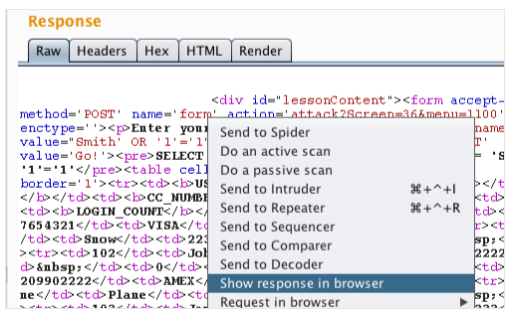
- Click “Show response in browser”.
- Paste the URL into the browser to view the response there.
- In this example, the attack has yielded the credit card details of all users.
Remediation Measures to Prevent SQL Injection Attack
These following suggestions may help to prevent SQL Injection attack from succeeding:
- Avoid accepting the user supplied inputs directly into SQL statements.
- Use Prepared statements and Parameterized queries for a safer side.
- Use Stored procedures which is safer than dynamic SQL.
- Strictly validate and sanitize the user supplied inputs (block the malicious inputs like. (,.,/,<,>,#,&,@,(,) etc.,).
- Use Escaping functions or Encoding mechanisms to avoid malicious script executions.
- Follow SQL Prevention Cheat sheet while building the application to avoid SQL injection attack..
- Encrypt the Business Sensitive Data being stored in the database. In addition to it Salt the encrypted hashes.
- It is better to follow the Principle Of Least Privilege (POLP), limit the user with minimum privilege and permission.
- Avoid displaying Database errors directly to the user which reveals information about the database to the attackers. Implement proper Error Handling Mechanisms to avoid such errors.
- By upgrading and using the latest framework for a website or a web application with all necessary patches and updates installed.
- Implement WAF (Web Application Firewall) which is an additional protection to the websites and web-facing applications form Security threats.
- The website or web application should undergo for a proper Security Audit regularly.
- Proper Security awareness and Secure coding practices Session should be given to the developers.
Conclusion
SQL injection is a popular attack method for an attacker. It is a burning threat to every organizations. But by following the proper precautions steps as mentioned above, it is possible to block the actions of the adversary. If it is not confident about the security posture of the application or the organization, it is better to consult a good Cyber Security Solution Partner who can guide you to protect your organization assets from global cyber threats.
How Briskinfosec helps you?
Briskinfosec scrutinizes the attack surfaces and secures them. Further, our security folks perform intense security assessments and identify the secretly lurking vulnerabilities, obviously terminating all those in the next step. They also perform the process of input validation, and if the incoming requests are detected as vulnerable, they thwart them. If found valid and harmless, they permit it. We have successfully identified and jettisoned many SQL injection flaws during our assessments. If we can do for others, surely we can do such wonders also for you.
Curious to read our case studies?
We have a huge collection of case studies for significant security sectors like mobile, network, web-based, database, wireless, and much more. Read out our case studies to know the way we prospered during the challenge of vulnerabilities eradication.
Last but not the least
The happenings of many global cyber breach incidents go unnoticed. This is due to the ubiquitous presence of them in indistinct websites, rather than all those being eligible for people to see and download from one spot at a single click shot. But, we present you a priceless gift disguised as a Threatsploit Adversary report which contains the globally occurred cyber breaches, the losses faced by companies, and much more. Instead of wandering here and there in search engines, just click our above report. You’ll save your time.
You may be Interested On
- Null Byte SQL Injection
- Server-Side-Includes Injection
- Cross-Site Port (XSPA) Attack
- DNS Zone Transfer Attack
- XML-External-Entity Attack
Refer for more Resource
“Note: Blog Category:-Web application Security”