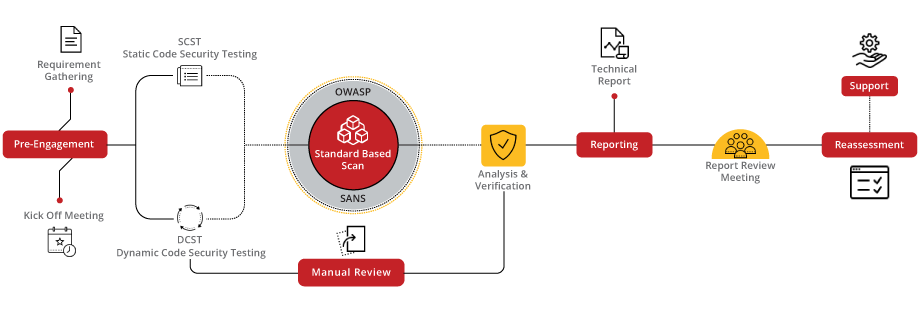
Elevate your application's defense with our secure code review service, meticulously designed to identify and mitigate vulnerabilities at the code level. By integrating best practices and leveraging advanced analysis tools, we ensure your codebase is not just compliant but also optimized for security. Our process involves a thorough examination using a combination of automated tools and expert manual review to uncover potential security flaws, ensuring your application is built on a foundation of security.
Our secure code review process is a detailed journey from code assessment to actionable insights, designed to fortify your application against emerging threats. By focusing on the critical aspects of your codebase, we offer comprehensive insights and recommendations for improvement, ensuring your application’s security is ironclad.
Cybersecurity starts with proper awareness. Briskinfosec BINT LAB researchers continuously put an extraordinary effort to help you to realise secure code review better and faster. Just download the one-page Secure Code flyer, Secure Code Case Study and Threatsploit Adversary Report.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Nowadays the biggest danger that we come across and also something that we are about to face in future is The cyber threat the crime that happens via internet and technology.
Read the blogThe protection of software applications against potential flaws and security breaches in today's digital environment .
Read the blogAndroid Manifest file provides the system with necessary data like application’s configuration information, permissions, and app components. Android Manifest File can be obtained by extracting any APK File and also while doing assessment, you can use APKtool & Drozer for extracting the Manifest file from the application.
Read the blogElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.