Empower your web applications with our OWASP ASVS-based Web App Intensive VA/PT audit, utilizing a hybrid approach with LURA Portal for a thorough security assessment, complemented by our exclusive bSAFE score for unparalleled security insights.
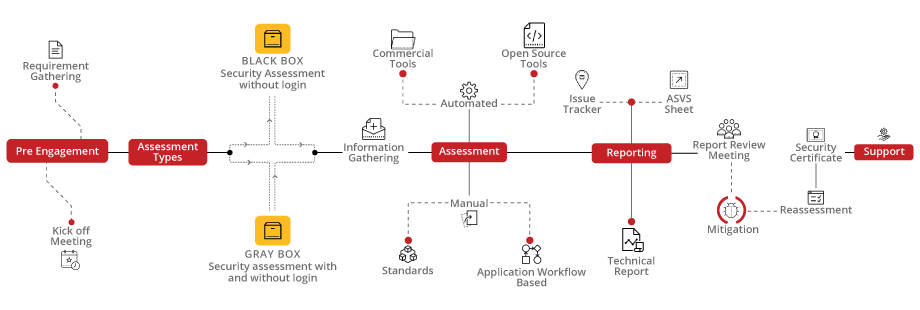
Briskinfosec Web App VA/PT approach encompasses a comprehensive journey from initiation, through in-depth assessment and reassessment, to final certification each step meticulously crafted to ensure your web application's security aligns with the highest standards ending with a respected certification that proves your strong cyber defense.
bSAFE provides a comprehensive maturity score for your web application security, aligning with OWASP ASVS standards to guide improvements and ensure continuous security enhancement.
Organizations falling into this range have a robust and secure system. Encourage continuous monitoring and periodic security assessments to maintain the high security posture.
Indicates a satisfactory security level but with room for improvement.Suggest implementing additional security measures and staying vigilant to emerging threats.
Organizations in this range are considered fragile and may have significant vulnerabilities.Recommend patches, and strengthening overall security protocols.
The lowest score suggests a system with severe security vulnerabilities. Urgently address and remediate identified issues to prevent potential breaches.




Access valuable resources, including one-page flyers, case studies, and our monthly magazine, Threatsploit Adversary Report, to enhance your cybersecurity knowledge and stay ahead of emerging threats. Download now and fortify your digital defenses with Briskinfosec.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
In today's interconnected digital landscape, web applications serve as the backbone of numerous online services, facilitating everything from e-commerce transactions to social media interactions.
Read the blogNowadays the biggest danger that we come across and also something that we are about to face in future is The cyber threat the crime that happens via internet and technology.
Read the blogStarbucks does have the best coffee in the world. But, do they have the best cybersecurity defense? ? Johnstone discovered It was possible to execute arbitrary code by uploading a webshell
Read the blogBrowse our selection of handy cybersecurity tools. Arm yourself with the right defenses to safeguard your digital life.
Elevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.