Introduction:
In this modern digital era, online transactions play a pivotal role. As technology is comforting people by reducing their burden in one prospect, there is also another grotesque side of it which is called as “Cyber War”, that is surreptitious in actions but clamorous in its repercussions. So, “Cyber war” is the use of computer technologies to disrupt the normal ongoing activities in a state (or) organization. The hardest and saddest part of it is that, these startling facts aren’t even acknowledged by many in this cosmos and it is their innocence that generate the path for hackers to prove their insolence. Another reason for these hacks to remain with a status like “never-decreasing and ever-increasing” is the pathetic fact that, even decade old vulnerabilities aren’t patched till now.
Contents:
Are you still unaware about the attack vectors?
Do attacks play a vital role in cyber war?
Have the XSS (Cross site scripting) attacks vanished?
SQL injection is still the leading method of cyberattack!
How to overcome business driven cyberattacks?
Conclusion
How Briskinfosec helps you
Curious to read our studies?
Last but not the least
You may be interested on
Are you still unaware about the attack vectors?
As organizations or individual accounts can be hijacked through hacking, hackers can use these attack vectors to infiltrate a network or to disrupt the access to sensitive data over the applications, whether it’s personally identifiable information (PII), payment card information, or any other type of sensitive data.
So, for eg: If you are running an older technology version that existed before a decade, then the attackers can easily deface your applications. Using this older technology, the vulnerabilities were created from various dimensions. These are the attack vectors that are still persisting even in today’s application. In an organization, the application level or infrastructure level should have a proper authorization. If it doesn’t have, it could lead to unauthorized access attacks such as broken access controls, insecure direct object references (IDOR).
The majorly covered attack vectors are phishing attacks, SQL injection attack vectors, DDOS attacks, Cross site scripting (XSS), unpatched vulnerabilities and Advanced Persistent Threats (APTs). The bar graphical representation indicating the percentage of various dreadful cyberattacks are illustrated below:
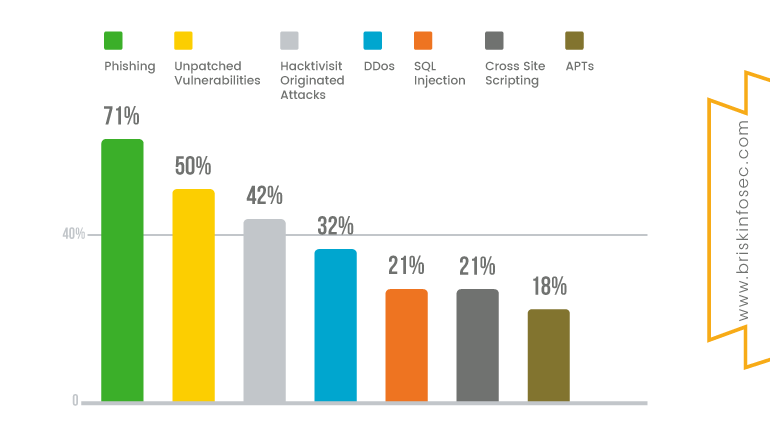
The most peculiar attacks faced by organizations are Phishing attacks. Through “phishing attack”, perpetrators try to impersonate a legitimate person, or a reputed firm through an email that tempts the user to click the link for gaining beneficiaries like “Win the prize of 50,000 INR” or “Win a free trip to foreign lands”, and through much more fascinating mails. Once when the users enter their details such as name, date of birth, address and bank details in order to claim the reward, the link redirects them to some other vicious page. Obviously, there's no prize as guaranteed by the faceless entity. All that the user got as a gift is that, “He has been deceived and all his personal and sensitive details into the hands of hackers has been received”.
A DDoS (Distributed Denial of Service) attack is launched from numerous compromised devices, often distributed globally in what is referred to as ‘Botnet’. It is distinct from other Denial of service (DoS) attacks. In DoS, a single source (one network connection) is used to flood a target with malicious traffic. But in DDos attack, multiple sources are used to flood the target machine, thus crashing down the server. They target a wide variety of important resources, from bank news to websites.
“Unpatched vulnerability” is another term for security vulnerability. It’s a security exploit that is unintended and an unpatched flaw existing in software code that exposes potential exploitation by hackers. Malicious software codes such as virus, worms, Trojan-horses and other malwares are such examples. Since the old decade vulnerabilities aren’t patched till now, contingencies for the inception of new vulnerabilities isn’t a startling fact.
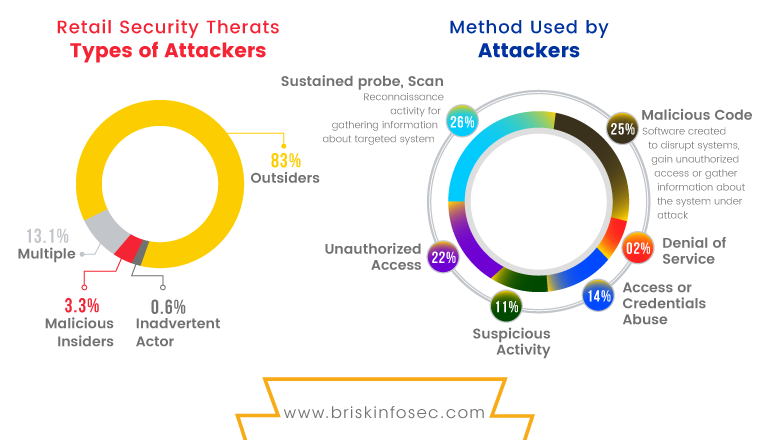
In the above diagram, some of the few methods are explained in detail. Malicious code is a term that defines unwanted files or programs that can cause harm to a computer or may affect your storage devices. The various contents in the above diagram are briefed below:
Suspicious activity: By using this attack, an attacker can bind a pre-loaded malware behind a link (phishing) or behind an image (Steganography), to get the shell or backdoors of the targeted individual or from any organizations.
Do attacks play a vital role in cyberwar?
Various threats are troubling the organizations in various ways. Among the uncountable number of terrifying attacks that are tormenting various digital firms, two attacks have been remembered from then till now as “notorious and unforgettable”. They are XSS and SQL based attacks.
Have the Cross-site scripting (XSS) attacks vanished?
XSS has been over a decade. Since then till now, these vulnerabilities remain unpatched!
XSS vulnerabilities were exploited and reported in 1990 itself. Post it, Microsoft security engineers introduced the term “Cross-site scripting” in 2000. It is defined as the “Act of loading attacked third-party web application from the unrelated attacked-site, in a manner that executes a fragment of corrupted packet prepared by the attacker to be launched on the targeted domain. Prominent sites like Google, Microsoft, Facebook, YouTube, Twitter and Orkut have suffered, because of XSS attacks. Mandatory steps to preclude XSS attacks aren’t even initiated in most of the organizations, which is truly a pathetic fact.
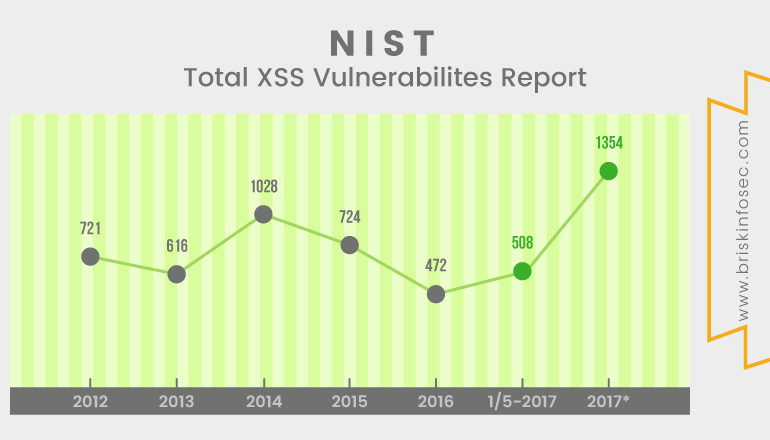
Statistics of XSS:
The below statistical representation indicates the XSS records of the past 6 years. From the graph, it is lucid that XSS attacks are like “Never-decreasing and ever-increasing”.
SQL injection is still the leading method of cyberattack!
SQL injection is a type of common attack vector. So, basically SQL injection vulnerability allows an attacker to inject malicious input into a SQL statement. In this SQL injection vulnerability, an attacker can easily insert the malicious SQL queries and can gain the access of the victim’s system.
Diagram indicating the percentage of attacks:
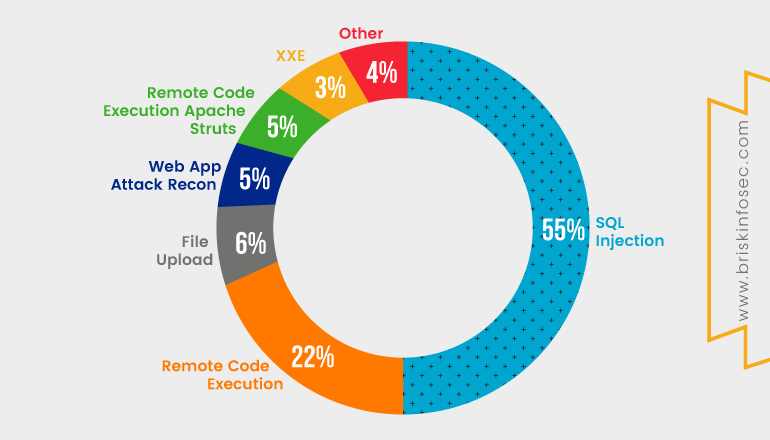
As shown above, when compared, most of the attacks that have occurred are SQL injection. It is a critical vulnerability and makes a higher impact on organizations and this issue isn’t still patched on internet.
How to overcome Business driven application level attacks?
Web applications are being developed under devops phase. In this phase, as the name suggest, applications are developed rapidly with development operations alone. But this entire deed forgets the security need. It is because of this recklessness towards security that has made even a ‘decade old vulnerabilities’, to remain unpatched till now. This is also a significant reason for various applications to be infiltrated with breaches.
In order to amend these existing flaws, implementation of security during the phase of development must be made as a necessity. Prior to this, proper security assessment must be facilitated during staging environment and post the development of applications.
CYBER QUOTE ON CYBER ATTACKS:

Conclusion:
The period of application technology has brought with itself numerous benefits that is secretly accompanied with some risks. Cyberattacks have become common and the majorities of businesses are at risk.
In the 21st century, the security investments are significant. So, make your business immune against attacks by constantly updating your security defence mechanisms.
CYBER QUOTE ON PROCESS:

How Briskinfosec helps you:
Day by day, as technology evolves, the opportunities for hackers to destroy the obsolete security defences also becomes easy. Setting up a firewall nor upgrading the antivirus to the trending version or hosting your security services on cloud servers alone won’t accomplish best security protection, unless and until you perform a proper security assessment on a regular basis from a competent cybersecurity organisation. Briskinfosec provides all its clients a complete security assessment, identifies all the security vulnerabilities and secures the attack surfaces. Customised security assessments are also done to patch the required bugs. Further, Briskinfosec delivers awareness to its clients on all possible cybersecurity issues.
We also do testing with our very own ANSE (Advanced Nmap Scripting Engine) scanner. Apart from this, Briskinfosec also utilizes its MAST framework (Mobile Application Security Testing) for performing mobile related security testing, which was officially released by the NCDRC (National Cyber Defence and Research Centre). One common uniqueness among these both is that, they are created by us which makes Briskinfosec one step ahead of others.
Curious to read our case studies?
Case studies are the best examples for readers to understand the process of various security assessments, and the techniques used by the company during assessment. Check out our case studies to understand the way we perform our assessments.
Last but not the least:
Browsing internet about the companies affected by attacks, the type of loss faced, and all these to be searched one by one through night and day, indeed is time-consuming and patience-exhausting. Doesn’t this sound tedious?
Don’t worry!
Briskinfosec prepares Threatsploit Adversary Report on a monthly basis, by collecting various cyberattacks and its impacts on the respective company. Instead, of searching here and there, just a single click is more than enough. You’ll be amazed, as what you’ve bought is a billion could’ve never got.


