What day is best for you?
- Sun
- Mon
- Tue
- Wed
- Thu
- Fri
- Sat
What time works?
30 minutes meeting
Asia/Kolkata Time
Almost there!
IST
There may be hidden vulnerabilities in your application, network or another part of your system. Therefore, we provide a range of security testing services to analyze the full attack surface. This involves thorough network, physical, and wireless assessments using the latest security testing tools. For companies seeking audits and penetration tests, rely on our experienced team to check quality of the security implementation and effectiveness of the Incident response team.
Cybersecurity starts from proper awareness. Briskinfosec BINT LAB cybersecurity researchers continuously put extraordinary effort to help you to realise cybersecurity better and faster. Just download the Threatsploit Adversary report.

Your window into the evolving threat landscape, offering insights and intelligence to protect against emerging cyber dangers.
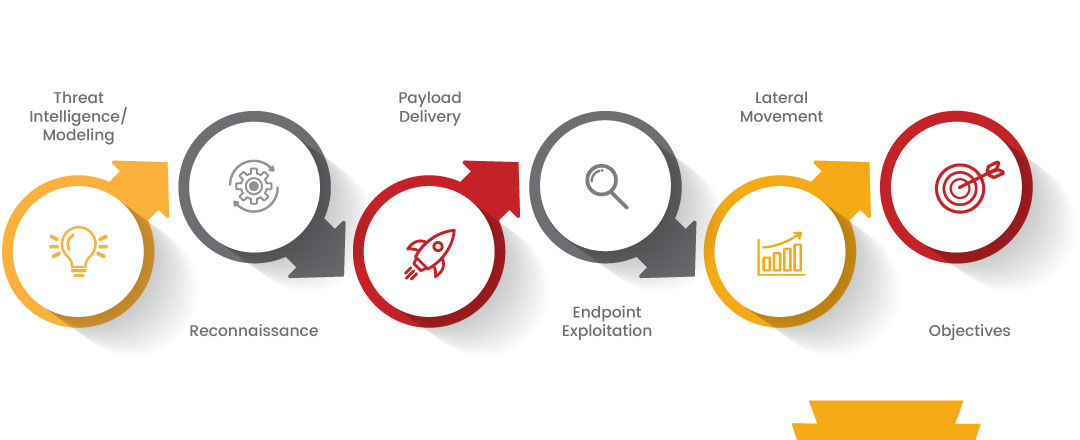
Red teaming VS Penetration testing :As opposed to traditional testing, Red Team attacks are multi-layered and focus on the objectives rather than on the method, allowing our team to think outside the box to create innovative scenarios you may not have planned or prepared for, allowing to you to identify blind spots in your defence strategy. A Red Team attack scope primarily defines the don'ts (i.e. what cannot be done) rather than the do's, leaving our Red Team as unrestricted as an attacker would be.
Steps we follow during Red Team process: Your lead consultant will discuss the objectives of the assessment as well as the methods, techniques and systems excluded and included from the scope of the exercise. You can also ask for specific methods to be included if you need to test a particular process or policy (access card cloning, random dropping of USB infected sticks, etc).
Timeframes will be discussed and agreed prior to commencement and will depend on the level of sophistication desired.
You will be notified one day prior to commencement by your lead consultant. Our Red Team will remain anonymous to not influence the results of the attack one way or the other.
Celebrating our achievements and collaborations, shaping a future of excellence.
























