What day is best for you?
- Sun
- Mon
- Tue
- Wed
- Thu
- Fri
- Sat
What time works?
30 minutes meeting
Asia/Kolkata Time
Almost there!
IST
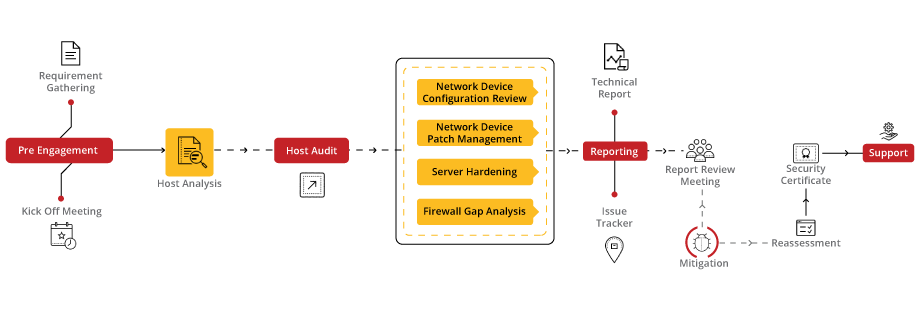
Our Host-Level Security Audit service is designed to fortify the defenses of your digital infrastructure by conducting a comprehensive examination of your host systems. With a focus on identifying vulnerabilities, assessing configurations, and ensuring compliance with industry standards, our audit provides actionable insights to enhance the security posture of your hosts and protect against potential cyber threats.
Our approach to Host-Level Security Audit involves a meticulous evaluation of each host system, including servers, workstations, and endpoints. We begin by conducting a thorough assessment of security configurations, software installations, and access controls. Our team then utilizes industry-leading tools and techniques to identify vulnerabilities, misconfigurations, and potential security gaps. Finally, we provide detailed recommendations and remediation strategies to strengthen host security and mitigate risks effectively.
Cybersecurity starts with proper awareness. Briskinfosec’s BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download the one-page Host Level Security Flyer, Host Level Security Case Study and Threatsploit Adversary report.

Your portal to robust server security, ensuring data integrity and trust in a digitally interconnected world through meticulous analysis and advanced security measures.

Revealing our expertise in safeguarding server integrity, showcasing real-world success stories, and highlighting fortified host-level environments against cyber threats and breaches.

Your window into the evolving threat landscape, offering insights and intelligence to protect against emerging cyber dangers.
Lura cybersecurity simplified portal can help to reduce project execution time, save cost, and bring a positive return on investment (ROI) to customers:
Lura reduces the time spent on documentation and minimizes the overall duration of projects, saving time and resources.
Lura provides a convenient and secure way for customers to access status reports and VA/PT reports, improving efficiency and reducing the risk of errors.
Lura helps to ensure that our cybersecurity services meet the highest standards of quality and regulatory compliance, reducing the risk of costly compliance issues.
Lura is a secure and transparent platform that helps to ensure the integrity of security assessments and build confidence in the quality of our enterprise-grade tests.
Celebrating our achievements and collaborations, shaping a future of excellence.

























Our Case studies are the best reference to prove the dexterity of Briskinfosec.




Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
In the world of networking, computers don’t go by names like humans. Instead, they go by numbers. Computers identify and communicate with each other over a network by means of some unique numbers called as IP (Internet Protocol) addresses.
Read the blogSparta is a Python based GUI application and it’s a network infrastructure pentesting tool by aiding the pentesters in performing scanning and enumeration phase
Read the blogMost people think that Red Teaming and Blue Teaming are different approaches for testing and identifying the security flaws.
Read the blogBrowse our selection of handy cybersecurity tools. Arm yourself with the right defenses to safeguard your digital life.
Elevating digital safety to unprecedented levels, setting the standard for secure online environments.
Discover our vault and dive into our Carousel for dynamic updates, explore our Infographics for simplified knowledge, and browse our Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!



Embark on a journey through BriskInfoSec's comprehensive suite of cybersecurity services, safeguarding your digital landscape with tailored expertise.






Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment