In recent times, the InfoSec field has been buzzing about Frida and tools based on Frida API. So what exactly is Frida?
Frida is a dynamic instrumentation toolkit. It is mainly created for testers, developers, and reverse engineering enthusiasts. For mobile app security testers, Frida is like a Swiss army knife. Using the Frida tool, we can inject our JavaScript into apps of Windows, macOS, GNU/Linux, iOS, Android, and QNX.
CONTENTS:
- Mode of Operation
- Installation
- Setting up Frida on Kali Linux:
- Setting up Frida-server on Android
- Setting up Frida-server on iOS devices
- Frida basic commands
- Loading Custom Frida Scripts
- The Best Frida Flavors to Mobile App Security
- Conclusion
Mode of Operation
- Injected
- Embedded
- Preloaded
Injected:
If you are having a jailed ios and android device (it is not a jailbroken/rooted device) then it is not possible to run the injected mode. In this case, we have to patch the app with “frida-gadget” a shared library that should be embedded with your apps and you can you the existing tool from frida.
Embedded :
If you are having a jailed ios and android device (it is not a jailbroken/rooted device) then it is not possible to run the injected mode. In this case, we have to patch the app with “frida-gadget” a shared library that should be embedded with your apps and you can you the existing tool from frida.
Preloaded:
Its something related to the previous section, it uses the frida-gadget, a shared library for loading the script from the file system. Its something familiar with Environment variables like LD_PRELOAD, DYLD_INSERT_LIBRARIES but here it will be JS_PRELOAD?

Installation:
Setting up Frida on Kali Linux:
Installing Frida tool is pretty easy but make sure you have installed the below requirements and OS options:
- Python – latest version 3.x is highly recommended.
- Windows, macOS, or GNU/Linux supported OS.
As given in their official site, use pip command to install frida in Windows, macOS, or GNU/Linux.
# pip install frida-tools
Once it is installed, verify whether it’s working or not. To know that, use the below command to verify.
# frida-ps
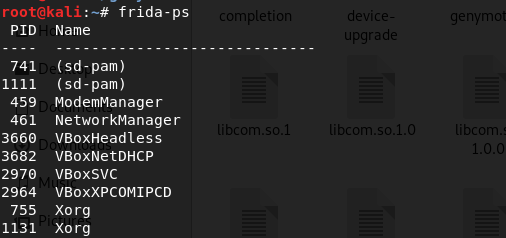
frida-ps will show you the running process name and its PID.
Verify the installed frida version using below command:
# frida –-version
![]()
Note down the installed version number, needed for installing Frida server in mobile devices.
Setting up Frida-server on Android:
We are going to use the injected mode for installation which is easy if you having physical rooted device or rooted emulators(most of the emulators come with root only). If you want to use it on a non-rooted phone, you need to repack the target app with frida-gadget. For the demo, let us use a rooted device to install the frida server.
For installation, you need an ADB tool that you can use from Android SDK (Software Development Kit) or use the Android studio tool which will have an inbuilt ADB in the Android studio SDK path. Example for in kali Linux - it will be in /root/Android/Sdk/platform-tools/path.
First, you need to download the Frida server for your specific android platform (arm, arm64, X86, X86_64). If your not sure about the platform then use the below command to find your specific android platform.
![]()
Now you have to download the Frida server for your platform from their official release page .
Once you downloaded the frida server zip file, unzip it, and rename the filename into “frida-sever”.
Step 1: Copy the frida-server file into the Android phone’s tmp directory using adb push command.
$ adb push frida-server /data/local/tmp/
Step 2: Change the permission of the frida-server file.
$ adb shell "chmod 755 /data/local/tmp/frida-server"
Step 3: run the frida-server file.
$ adb shell "/data/local/tmp/frida-server &"
Every time, you must run the frida-server file to connect with desktop terminal. Now, connect your device over USB or Wi-Fi. Also, use adb devices to confirm whether the device is connected or not.
# adb devices
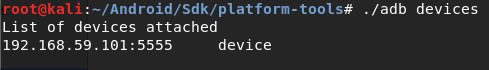
Now, everything is ready. From desktop terminal, we can connect frida-server by using the below command:
# frida-ps -U
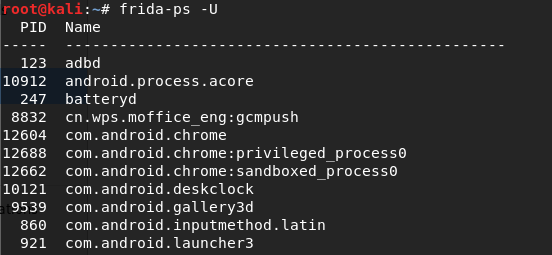
If everything works fine for you, it will give you the running process id’s and names from your device. Now, you’re good to go with frida.
Setting up frida-server on iOS device
Like Android, we can use jail break device or non- jail break device. Here, we are using the jail broken device to install the frida-server. Comparing to android, in iOS, it’s pretty easy.
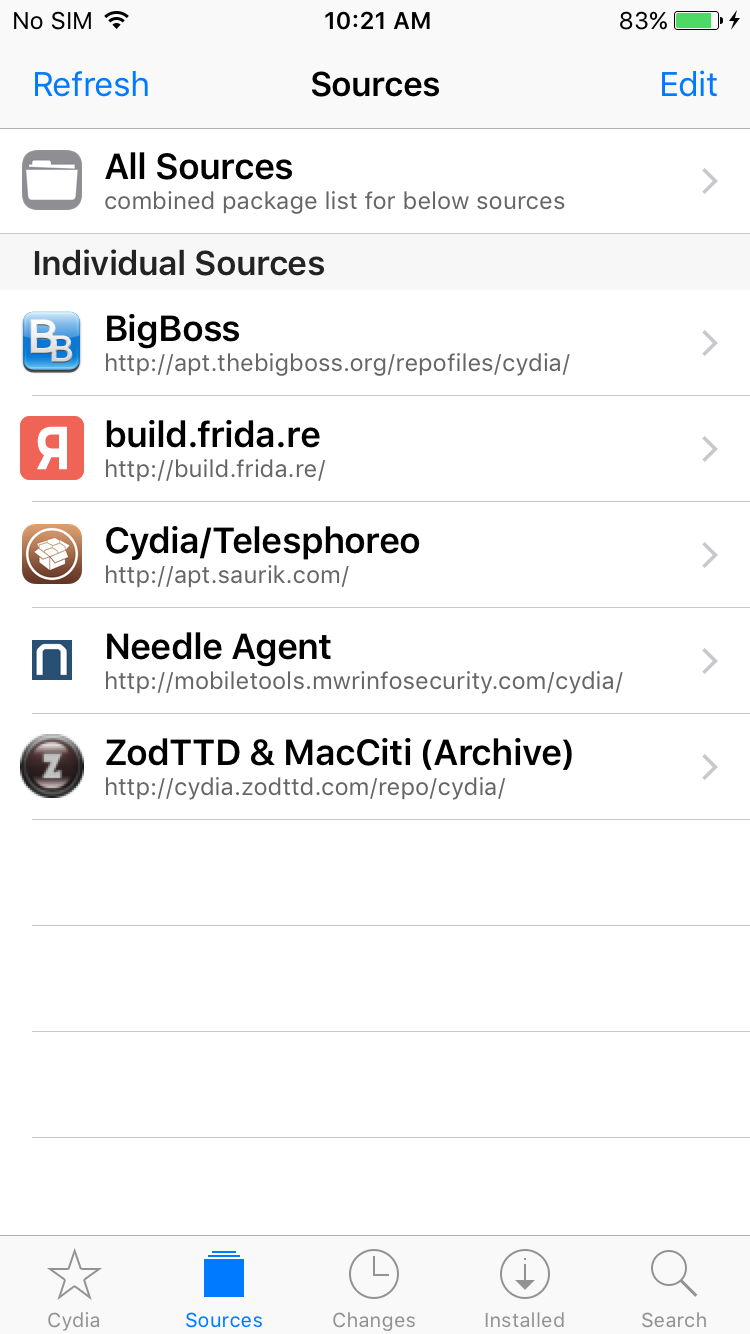
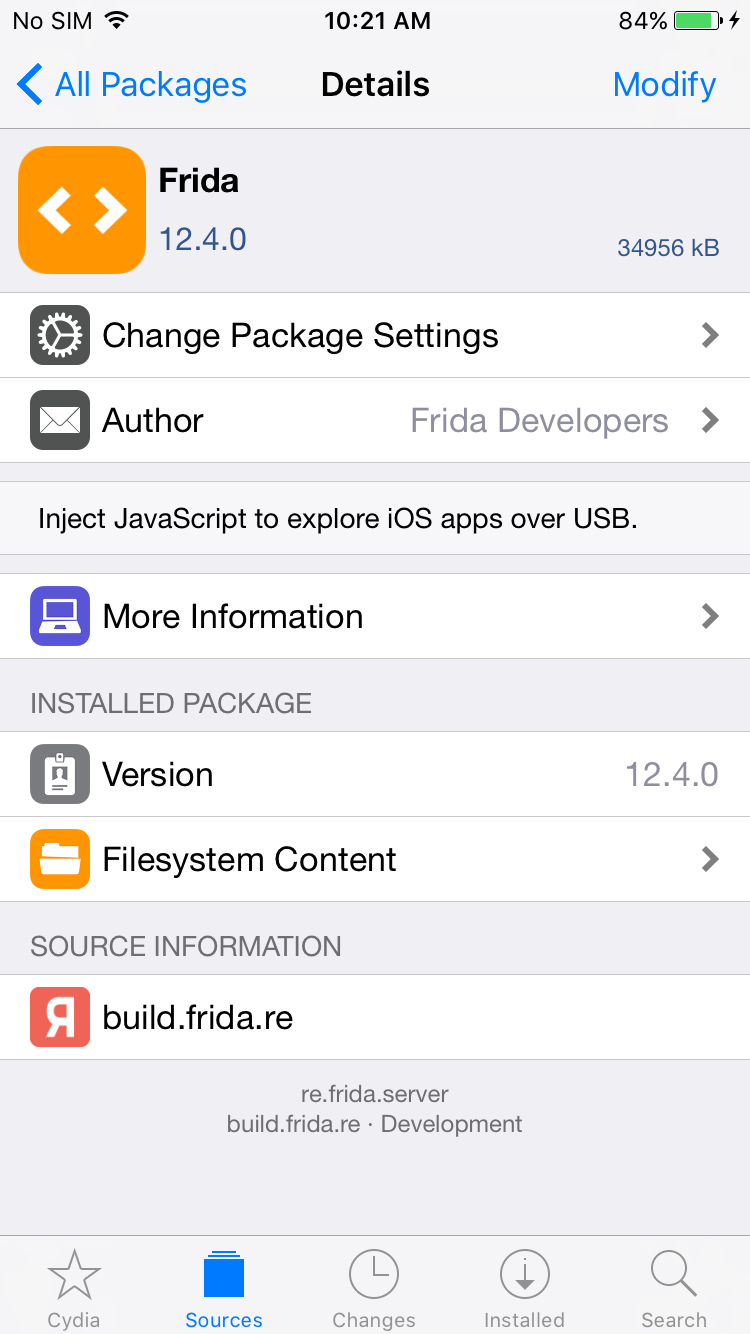
Step 1: Go to Cydia app and add Frida’s repository by going to Manage -> Sources -> Edit -> Add and enter https://build.frida.re. It will add a new source in the source list. Go to the frida source, now you should install the Frida package.
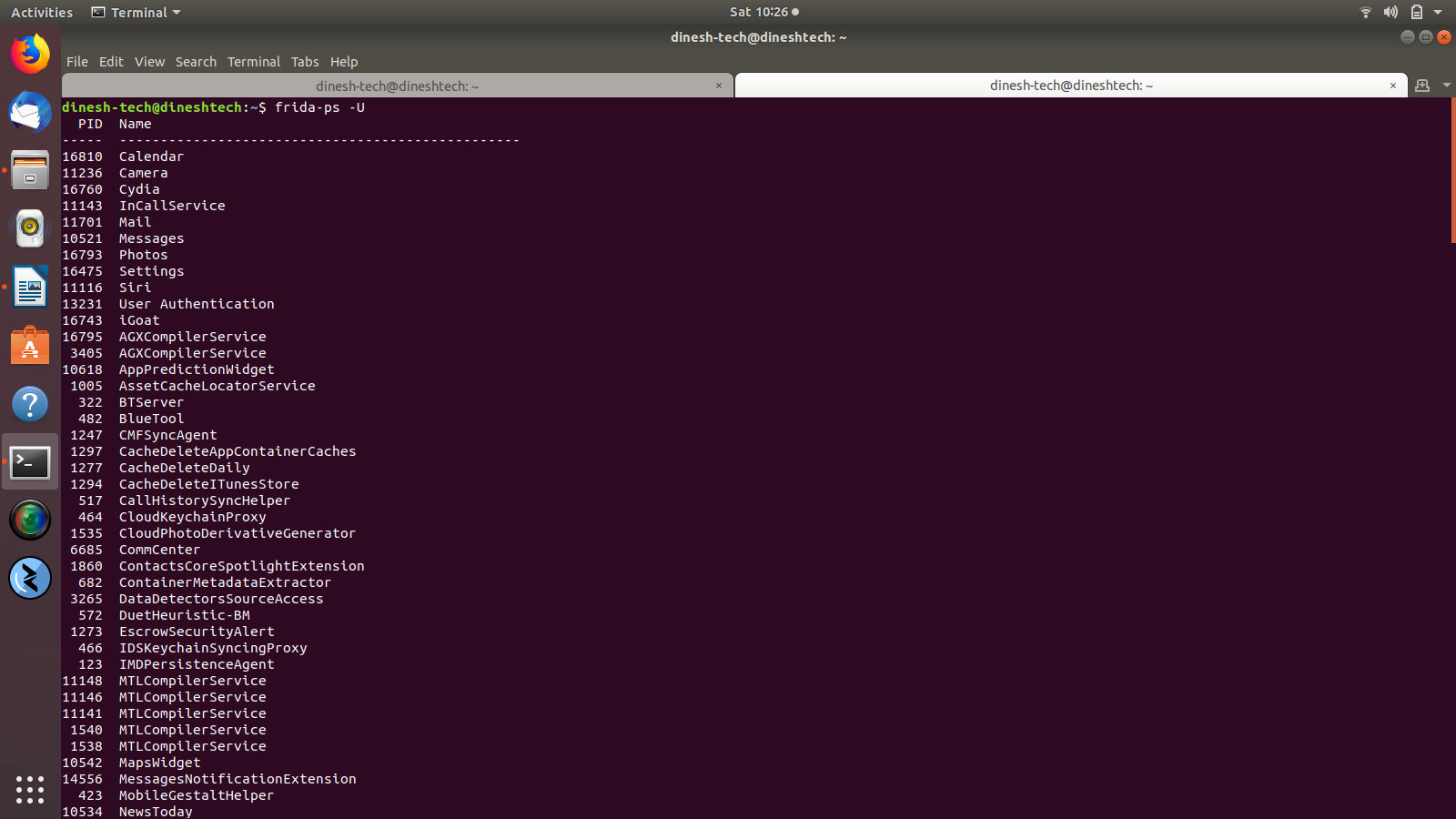
Now, go back to your system. Connect your device over USB and verify the frida connection using the below commands.
# frida-ps -U
Frida Basic Commands:
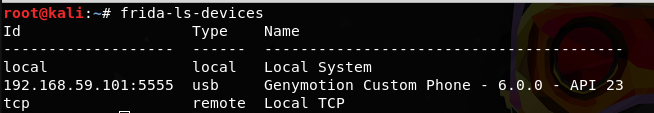
# frida-ls-devices:
This command is used to list all the attached devices.
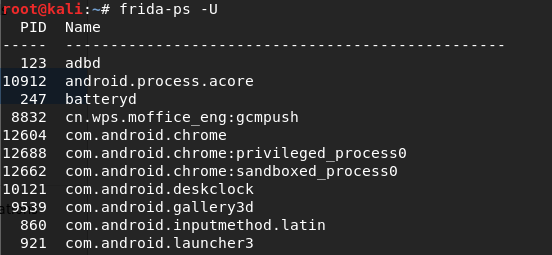
# frida-ps
This command is used for listing processes, which will return all the running processes. To return the process from the connected device over USB, add -U option.
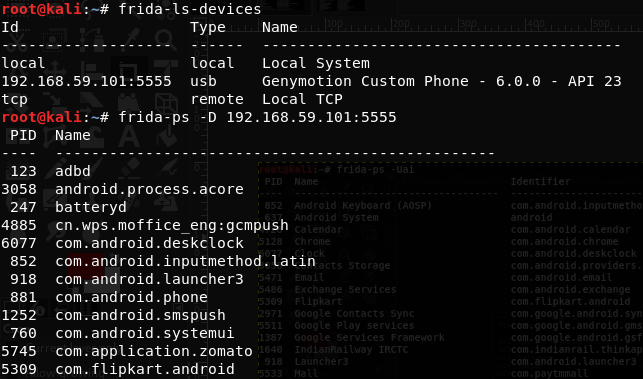
$ frida-ps -D 192.168.59.101:5555
This command is used to connect Frida to the specific device listed from frida-ls-devices
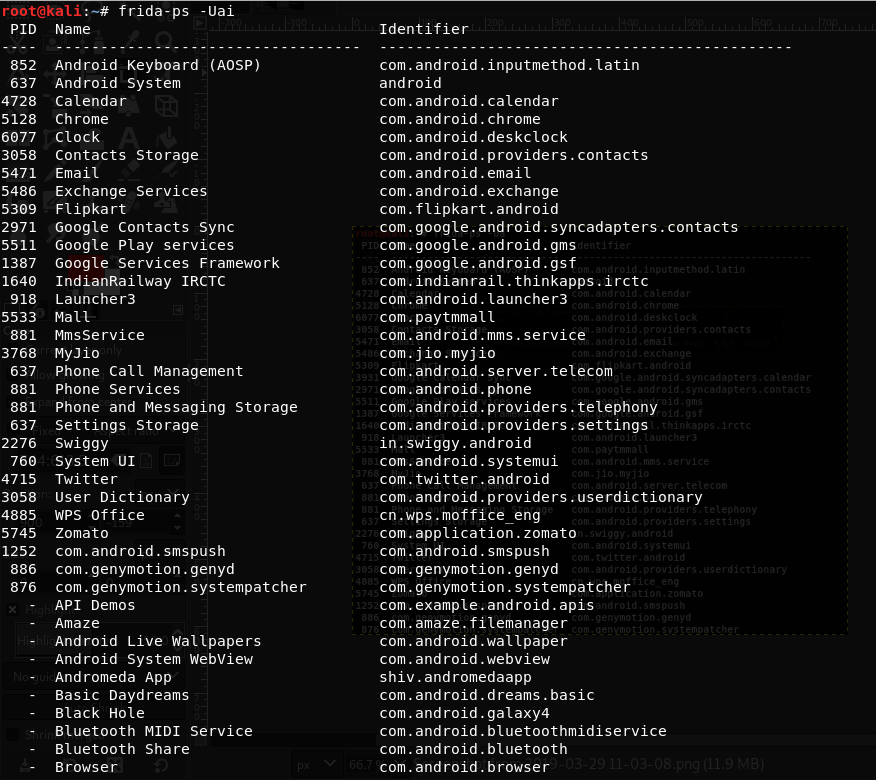
$ frida-ps -Uai
This will list the installed applications in the device.
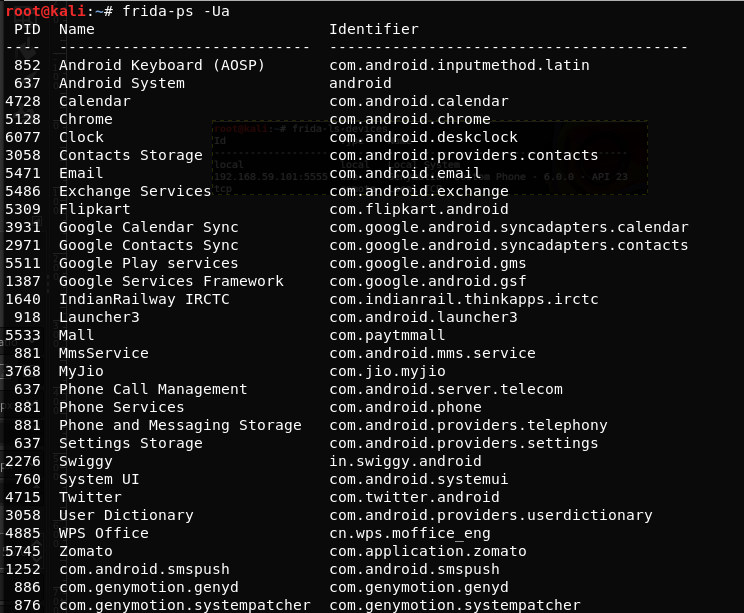
$ frida-ps -Ua
This will list all the running applications in the device.
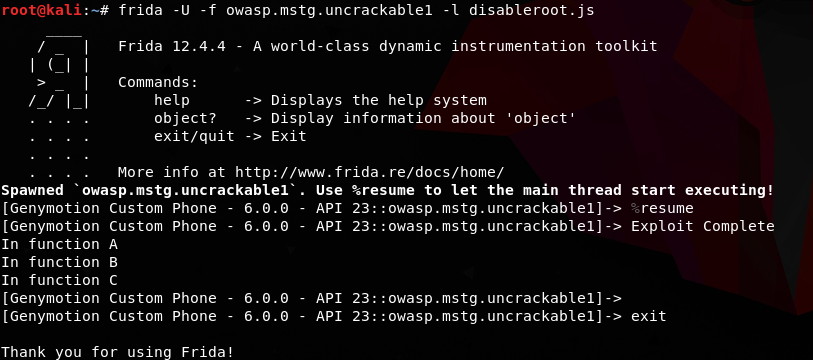
Loading Custom Frida Scripts
# frida -U -f owasp.mstg.uncrackable1 -l disableroot.js
Using these commands, we can load external scripts (javascript) into the application by adding -l options with Javascript file. Option -f is for finding the application, and then to hook it.
Want to learn more about the frida, its recommended to checkout this frida live work shop conducted by leonjza. if you miss that event dont worry session is available in youtube.
The Best Frida Flavors to Mobile App Security
Most of the infosec community is using the Frida flavored tools because of the benefits and easiness given by tools. Infosec researchers have taken the Frida and made so many tools for a different purpose. There are so many tools out there but I am going to list some tools which are really helpful for your assessment.
- Objection - has lot of features, Regularly updating and very useful for Assessment. (My personal Favourite).
- RMS-Runtime-Mobile-Security - similar to objection but it has web interface and currently supports android only.
- Grapefruit - iOS app blackbox assessment tool.
- r2frida - if you already using Radare, the r2frida makes it better together.
Conclusion:
Best things about Frida tool are, it’s free and open source, and supports multi platforms such as Windows, Linux, and macOS. Frida supports scripting which means, we can inject our own scripts and hook any functions, even an API without application source code. Based on Frida, in GitHub, there are so many tools available with different features. If your new to mobile app security or need to setup a separate environment for testing purpose then feel free to use our BIMOS virtualbox images which has most of the needed mobile app security tools. They’re truly awesome. Try them out now!
How Briskinfosec helps you?
Briskinfosec has a well experienced team of security engineers whom are highly skilled in providing top notch security assessments for various security sectors like Network, Mobile, Web, Database, Wireless, Docker, and much more. Frida is used for mobile applications and with regards to mobile security testing, we use our also our own framework, MAST-NCDRC (Mobile Application Security Testing- National Cyber Defence and Research Centre). It was officially released by NCDRC. This catapults us to a place, much ahead of other security firms.
Related Services: