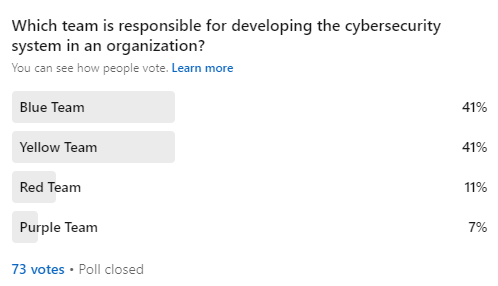
We wanted to find out how much pros know about the different teams. We were surprised by the results of the poll about who is in charge of building an organization's cybersecurity system. There were equal responses for both Blue and Yellow answers. The right answer is yellow, and we're going to tell you in the below write up
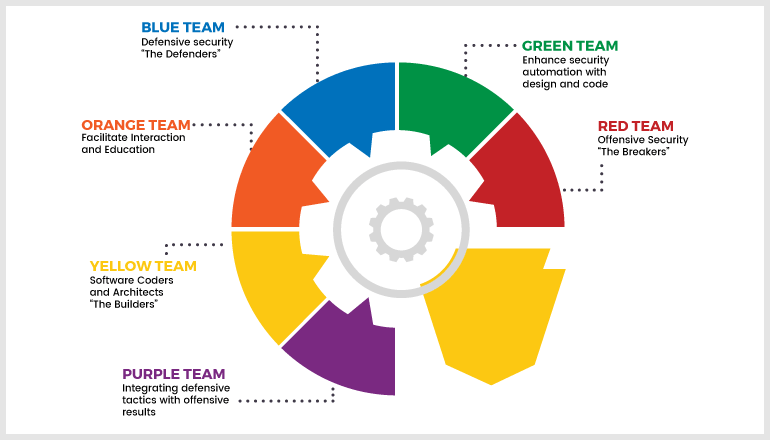
Color’s play important part in our lives. In school, if we were running out of a particular color, we would mix the basic colors and produce new ones. What if I tell you that in Cybersecurity, the teams are named as per the colors. And, these colors represent the tasks that they do.
Let’s find out how teaming happens in a cybersecurity environment. What does Red, Blue, Yellow, Purple, Green, and Orange represent?
Here is the strategy behind the colors and naming.
Primary Colors - Red, Blue, Yellow
Secondary Colors - Purple, Green, Orange
If you mix any of the two primary colors, you’ll get the secondary colors. Likewise, if we mix any two primary teams, we’ll get the secondary team.
Let’s understand one by one.
Red Team
Red Team is responsible for an offensive testing process. They behave exactly like an attacking team and do offensive testing in the real time scenario. Red teaming operations will be effective if they were hired from an offshore cybersecurity company.
Here is a simple scenario of how the red team works?
Only the top-level management in the company knows that an offshore Red team is going to do an Red teaming operation. Usually, a red team enters like an interview candidate, a pest control team, or a rest room cleaning team and so on. Yes, they enter in that specific way, just like spy in the movies.
Then they note down all the loopholes and pain points in an organization like total number of security cameras installed on the sensitive places, total number of exit possibilities, any feasibility for fire alarm, total guards protecting the sensitive places and other weaknesses.
This might take place for a period of 30 days or even months depending on the requirement. The Red teamers analyze the behavior and prepare a strategy to do attacks.
Note: No one in an organization knows anything about these Red teaming operations except the top-level management.
Once they exploit the resources, they’ll make a report of the entire operation and deliver it to the company.
Their tasks include,
- Offensive security
- Ethical hacking
- Exploiting vulnerabilities
- Penetration testing
- Blackbox testing
- Social engineering
- Web App scanning
Usually, the Red team doesn’t have any task boundary. They use all possible and new methodologies to perform the Red teaming operation.
Blue Team
The Blue team is responsible for the defensive operation. They work closely with highly sensitive data and information and provide defensive security.
Their tasks include,
- Defensive security
- Infrastructure protection
- Damage control
- Incident response
- Operational security
- Threat hunters
- Digital forensics.
Note: Enterprise companies will have thousands of defensive security engineers (Blue team) different functions in a system.
Purple Team
The purple team works on maximizing the performance of Red team and in the same time, they enhancing the performance of Blue team.
Basically, a purple team should know both Red teaming and Blue teaming task. In other words, we can say, a combination of Red and Blue team to improve the outcome.
Their roles are mainly to,
- Improve detection and defence capabilities.
- Improve the abilities of Blue and Red team’s operation.
- Improve overall performance of Attack and defence.
Orange Team
Orange team helps developers to think like an attacker by getting as much informations in real time from the Red team.
It’s like, if you want to make a highly secure lock, you know the art of breaking the lock, basically like a locksmith.
Orange team plays an important role in developing loop holes free, error free and bug free applications.
Yellow Team
Yellow team also called as “builders”, is responsible for building software and applications that are free from security issues. They work closely with Research and Development and improve the security features for the company.
The Yellow team gets insights from the Red team and Blue team and work on the same to make the outcome better.
The following category people falls under the Yellow team.
- Software developers
- Application developers
- Software Engineers
White Team
White Team acts like a refer between the Red Team and the Blue Team and they help to perform the activities of Red Team and Blue Team in a fair manner.
Basically, a White team performs the judgmental operations between the Red team and Blue team. During an unplanned Red teaming operation, the White team eavesdrop the performance of the Blue team.
White team is also responsible for,
- Analysing Compliances
- Logistics Management
- Hardware and other Management
Green Team
It might be difficult for a programmer or developer (Yellow team) to have real time knowledge on the security issue and similarly Blue team won’t have real time knowledge on the frameworks, functionalities, software dependencies.
Here comes the Green team role. They acts as a mediator between the Blue team and the Yellow team.
Green team gets insights from Blue team (defenders) and they educate the Yellow team (builders) to provide a better outcome.
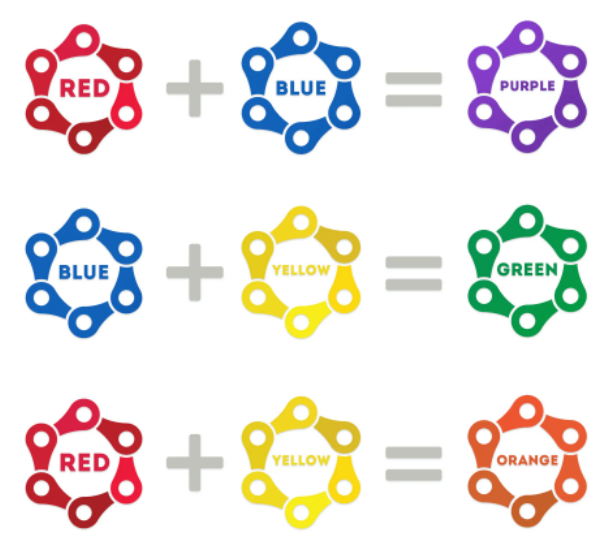
Source: Hackernoon
As of now, these are the teams. The more the security scenarios keep on changing, many more teams may emerge. One thing is crystal clear, the cybersecurity scenarios are not safe anymore. There is an immediate need of raising such teams at enterprise levels. VA/PT assessments, Virtual cybersecurity services are a must.