Table of Contents
In February 2025, the Indian Clearing Corporation Limited (ICCL) faced a penalty of 5.05 crore for failing to establish a Disaster Recovery Site (DRS) and Primary Data Centre (PDC). This major oversight violated SEBI’s mandatory cybersecurity framework, leaving ICCL vulnerable to data loss and operational downtime. Such incidents highlight the severe consequences or impacts of neglecting or not implementing SEBI’s security requirements, which are mandatory.
This blog will help you to explore SEBI’s cybersecurity framework, compliance challenges, and proactive strategies for securing financial institutions. Before starting, let’s refresh our knowledge of the basics.
A short glimpse of SEBI?
For a more precise definition, SEBI is a regulatory body established by the Indian government to oversee financial institutions and ensure they follow secure practices to protect investors' funds and data. SEBI can be seen as a shield that safeguards the vast amounts of sensitive data managed by financial institutions. The Indian government established SEBI in response to the rise in fraudulent activities, which created a gap between financial entities and investors by damaging their reputation and causing financial losses. SEBI was introduced to bridge this gap and restore trust in the financial system.
This raises a common question: Don’t banks need to be SEBI compliant?
While SEBI regulates financial institutions such as stock exchanges, depositories, and mutual funds, banks fall under the jurisdiction of the Reserve Bank of India (RBI). However, institutions like IDBI and EXIM Bank that operate across both SEBI and RBI regulated domains must adhere to the respective cybersecurity frameworks, ensuring alignment with both regulatory bodies.
Why is SEBI compliance more essential?
SEBI compliance is vital for financial institutions to adhere to mandatory regulations, ensuring smooth business operations. Compliance helps in gaining customer trust, avoiding legal penalties, and enhancing cybersecurity measures to safeguard sensitive financial data. By following SEBI’s regulatory framework, organizations can mitigate risks, maintain market integrity, and ensure transparency in financial operations.
On August 20, 2024, SEBI introduced the Cyber Security and Cyber Resilience Framework (CSCRF) under Section 11(1) of the SEBI Act. This framework outlines the security controls that financial institutions must follow to ensure data protection and cyber resilience. In addition to the CSCRF, there are four key cybersecurity principles that institutions must adopt.
Principles of SEBI’S Cybersecurity Framework
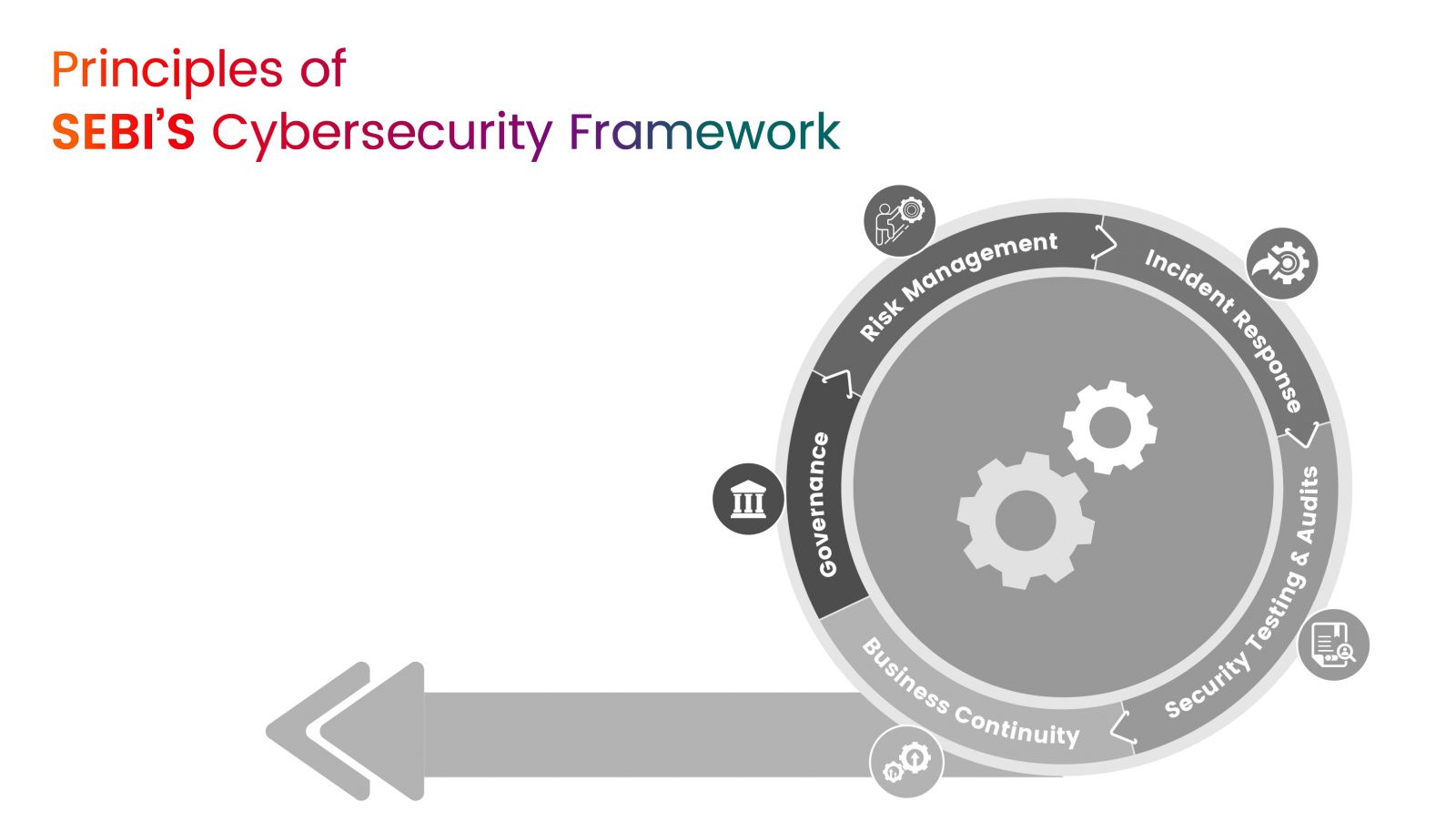
- Governance
- Risk Management
- Incident Response
- Business Continuity
- Security Testing & Audits
Now we are going to dig into the most important section, which is “What are the consequences of a financial institution being non-compliant with SEBI? Let’s now refer to the recent case studies.
Lessons from SEBI Non-Compliance Cases
ICCL’s 5.05 Crore Penalty for Disaster Recovery Gaps
ICCL’s failure to implement a Disaster Recovery Site (DRS) and Primary Data Centre (PDC) resulted in a 5.05 crore penalty. The absence of these systems exposed ICCL to severe risks, including data loss and prolonged service outages. SEBI’s investigation revealed ICCL lacked:
- A Primary Data Center (PDC) for data continuity.
- A Near Site (NS) for immediate data recovery.
- An effective Disaster Recovery Plan (DRP) with defined recovery timelines.
This case highlights the importance of robust disaster recovery frameworks and business continuity planning.
HDFC Securities Penalized 65 Lakh for Monitoring Failures
HDFC Securities faced a 65-lakh penalty after failing to detect unauthorized system activities. SEBI’s investigation revealed inadequate monitoring tools, resulting in delayed responses to suspicious activities. Contributing gaps included:
- Absence of SIEM tools for real-time alerting.
- Lack of endpoint monitoring solutions to identify compromised systems.
- Failure to implement user behavior analytics for detecting unusual access patterns.
This incident emphasized the need for continuous monitoring solutions and proactive threat detection mechanisms.
Link Intime India Pvt Ltd Fined 1 Lakh for Delayed Remediation
Link Intime India Pvt Ltd was penalized 1 lakh for failing to resolve security vulnerabilities identified during a security audit. Despite SEBI’s instructions, the firm delayed patching identified vulnerabilities. Key weaknesses included:
- Outdated firewall rules that failed to block known threats.
- Delayed application of security patches for identified vulnerabilities.
- Lack of a structured vulnerability management process for timely remediation.
This case highlights the importance of efficient vulnerability management and timely patching processes.
An entity or a financial institute not willing or not completely aligned with the SEBI has to pay a penalty amount, which can be an unimaginable amount, which can also destroy the reputation and cause financial damages.
Best Steps to be SEBI Compliant
Once you have covered the Cyber Security and Cyber Resilience Framework (CSCRF), you will be compliant with SEBI, to be more precise, and for easy understanding on how to implement this CSCRF, refer to the below steps.
1. Governance
- Establish a cybersecurity governance framework with clear policies and procedures.
- Form a cybersecurity committee to monitor compliance and risk management.
2. Risk Management
- Conduct regular risk assessments to identify vulnerabilities and mitigate threats.
- Implement a risk-based approach to prioritize security measures.
- Ensure third-party risk management by assessing vendor security controls.
3. Incident Response
- Develop a structured Incident Response Plan (IRP) covering detection, containment, eradication, and recovery.
- Establish a dedicated Incident Response Team (IRT) with defined escalation procedures.
- Conduct cyber incident simulations to test and refine response strategies.
4. Business Continuity
- Implement a Business Continuity Plan (BCP) to ensure operational resilience during disruptions.
- Conduct regular BCP testing and updates to adapt to evolving threats.
- Maintain secure data backup and recovery mechanisms to prevent data loss.
5. Security Testing & Audits
- Perform quarterly Vulnerability Assessment & Penetration Testing (VAPT) to identify weaknesses.
- Conduct firewall and network security audits to ensure proper configurations.
- Regularly review security policies and compliance gaps to align with SEBI regulations.
Securing Your Compliance Journey with Briskinfosec
At Briskinfosec, we are committed to helping your organization achieve seamless SEBI compliance with clarity, confidence, and complete cybersecurity assurance. Our team of seasoned professionals offers:
-
Comprehensive VAPT assessments to uncover and mitigate vulnerabilities
-
Tailored cybersecurity policies aligned with SEBI’s CSCRF framework
-
Robust incident response planning for swift and effective crisis management
-
Advanced red teaming and third-party risk evaluations
-
24/7 SOC monitoring for real-time threat detection and response
-
Targeted phishing simulations and employee awareness programs
Partner with us to strengthen your compliance posture and proactively defend against evolving cyber threats. Let’s secure your future together.
Frequently Asked Questions
1. Are banks required to follow SEBI’s CSCRF?
No, banks follow RBI guidelines, but institutions under both regulators must comply with both.
2. How can financial institutions achieve SEBI compliance?
By implementing CSCRF controls like governance, risk management, and regular security audits.
3. Does SEBI require VAPT testing?
Yes, regular Vulnerability Assessment and Penetration Testing (VAPT) is mandated for compliance.
4. What is the role of Briskinfosec in SEBI compliance?
Briskinfosec provides end-to-end cybersecurity services aligned with SEBI's framework.
5. How frequently should VAPT be conducted to stay compliant with SEBI?
SEBI recommends quarterly VAPT to proactively uncover and fix security flaws. It’s a key element of maintaining a compliant and secure environment.


