A systematic assessment of systems and applications to identify and mitigate security weaknesses, enhancing protection against potential cyber threats.
Vulnerability Hybrid Approach seamlessly integrates automated scanning with human expertise, ensuring a comprehensive evaluation of system weaknesses. By combining advanced technology and human insight, it identifies vulnerabilities, offers context-driven insights, and fortifies security measures against diverse cyber threats, ensuring a resilient digital environment.
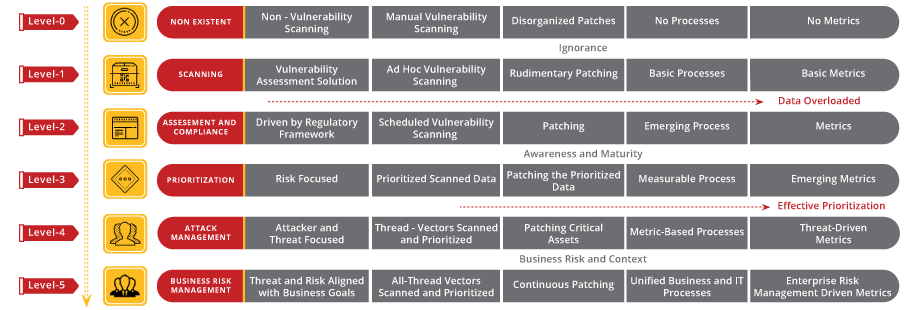
Cybersecurity starts with proper awareness. Briskinfosec BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download the one-page Vulnerability Flyer, Vulnerability Case Study and Threatsploit Adversary Report.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Nowadays the biggest danger that we come across and also something that we are about to face in future is The cyber threat the crime that happens via internet and technology.
Read the blogThere’s a saying, ”Change is the only thing that never changes!” Similarly, each and every year has a change .
Read the blogData as general is a set of information, knowledge or fact that is measured and stored in storage devices.
Read the blogElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.