What day is best for you?
- Sun
- Mon
- Tue
- Wed
- Thu
- Fri
- Sat
What time works?
30 minutes meeting
Asia/Kolkata Time
Almost there!
IST
Every year, data security is becoming a critical concern among enterprise businesses as cyberattacks are increasingly rapid and widespread. Throughout the business, government and healthcare sectors, attacks have been persisting with great frequency despite the use of advanced high-tech, in-house security systems. In one third of those cases, the attacks occur within seconds and give the victims some time to redouble or recoup their losses.
Cybersecurity starts from proper awareness. Briskinfosec BINT LAB cybersecurity researchers continuously put extraordinary effort to help you to realise cybersecurity better and faster. Just download the Threatsploit Adversary report.

Your window into the evolving threat landscape, offering insights and intelligence to protect against emerging cyber dangers.
SOC (Security Operations Center) is a security team that works with organizations to protect them against cyberattacks. The team will utilize a range of technology and processes that are designed to spot system vulnerabilities and prevent possible occurrences of cybersecurity theft.
The SOC teams consist of experts with extensive backgrounds in cybersecurity operations. As hackers develop new ways to break into systems and steal data from unsuspecting targets, the SOC engineers constantly studies the latest threats and would develop countermeasures to ensure the security of client-business networks.
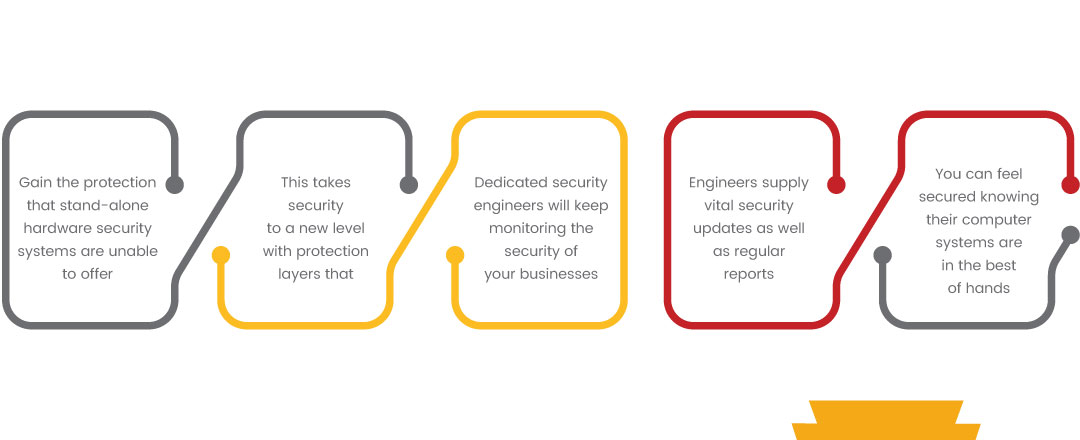
Instead of investing money in security hardware, enterprises can do 24/7 monitoring with the help of SOC-As-a-Service. At times, companies also make use of hardware systems that are designed to make systems breach-proof but they fail to deliver on that promise.
With SOC-as-a-service, companies can cut down on the expenses typically associated with cybersecurity and receive advanced protection from cyber intrusions.
As the SOC teams operate off site, the required hardware systems will be set up elsewhere to protect client businesses.
SOC-as-a-service makes it possible to allocate more resources for that company, focusing on promoting their own products and services, leaving security up to trained professionals.
Even a small organization can hire SOC-as-a-service, and the engineers who run the third-party service can handle the important aspects of security enforcement.
This service allows companies to rank the importance of layers of data and determine the severity of threats that surface on the radars of computer networks.
Antivirus software identifies the “threats” at various levels on a computer system, many of which are benign. Others really do require action.
For many companies, tracing cyber threats is a confusing and time-consuming process due to the vast range of harmless and more critical discrepancies that emerge on network radars.
With SOC-as-a-service, companies can more easily distinguish true threats and act upon those problems with focus and urgency.
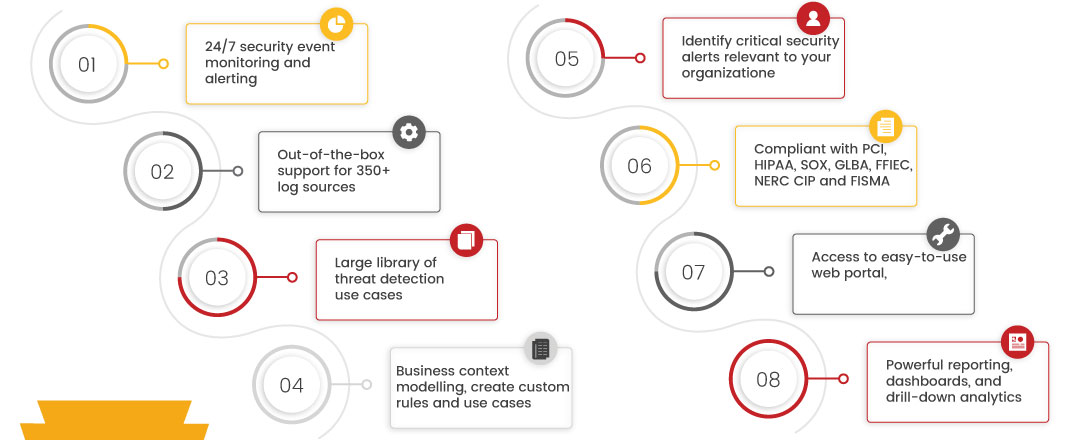
From a managed security operations center, regular analyses (daily and even hourly) are performed on the company’s networks and servers and also connect with the customers.
With the most highly skilled cybersecurity analysts, a SOC-as-a-service team can pinpoint security events the moment they appear on the radar.
Businesses might take hours or even days to realise their cyber security breaks, within that span of time, hackers can access the personal information of the customers, as well as vulnerable company data. Events like these can attract bad publicity and seriously damage a company’s reputation in the marketplace. Consequently, the loss of business can soar into millions and even cause some companies to fold once the dust has settled.
As cyber criminals are more covert and intricate in their techniques, security standards must constantly be updated to prevent company systems from being penetrated.
Even though there are several security upgrades hackers devise new ways to bypass system security parameters so, new levels of skill are required to combat these threats
SOC-as-a-service teams are staffed with engineers who possess the most advanced skills for handling the attacks that are perpetrated by today’s cyber criminals.
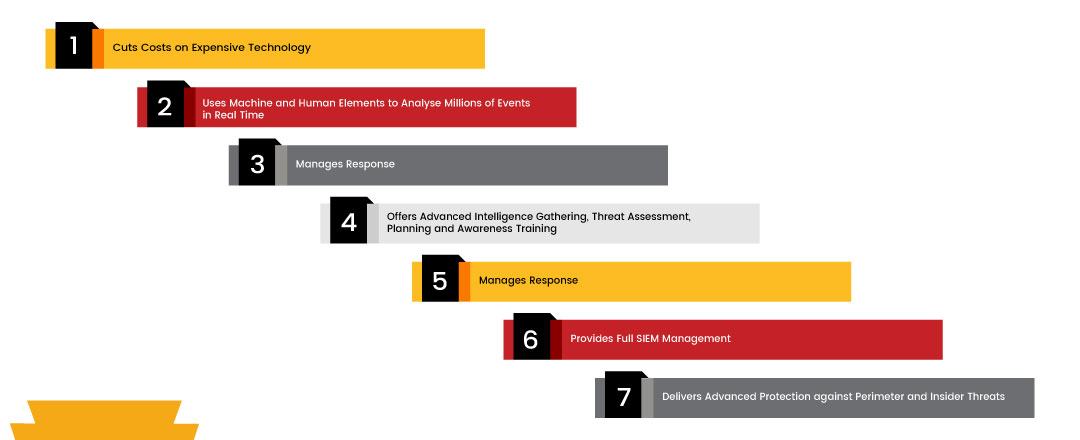
SOC-as-a-service makes the companies to remain secure against the most advanced threats by offering a coordinated approach to intelligence gathering. With up-to-the-minute threat assessments, companies can develop more fool proof plans for security response, the moment potential threats emerge on the radar.
The tiers of SOC-as-a-service also operate at different levels of involvement with company clients. Few companies would wish to receive status reports on security threats and use that info to enact security measures, whereas other companies want full security information and event management (SIEM) service where everything is handled by the third party.
In a hybrid model of SOC-as-a-service, the SOC provider offers a cloud-based SIEM service that the company’s client uses to monitor and correct its own security events.
For many companies, tracing cyber threats is a confusing and time-consuming process due to the vast range of harmless and more critical discrepancies that emerge on network radars.
Some companies go for a more autonomous approach, where they maintain their own in-house SIEM system but seek a third party to remotely monitor security alerts during off hours and holidays. Whether a company prefers full or partial SIEM management, the security benefits are vital in today’s cyber climate.
Celebrating our achievements and collaborations, shaping a future of excellence.
























