- Insecure Deserialization
- Content Management System Vulnerabilities
- Server Side Request Forgery
- Apache Struts Framework RCE Vulnerability
- XML External Entity and XML Injection
- AI Powered Attacks
- Blind Cross Site Scripting (XSS)
- APIs Endpoint based Vulnerability
- Server Side Template Injection (SSTI)
- Hostile Sub-Domain Takeover Vulnerability
- Conclusion
- How Briskinfosec helps you?
- Curious to read our case study?
- Last but not the least
- You may be interested on
Introduction:
For a long time, Web applications are subjected to various kinds of security vulnerabilities because of the increase in its usage and the use of dynamic web application technologies like PHP, Server side JS, and Application Program Interface (API) etc., for fetching data from the server based on the user’s request.
Insecure Deserialization:
Insecure Deserialization is one of the latest and trending web application vulnerability and is also included in the latest OWASP TOP 10 2017 list.
Type of Vulnerability: Code Level
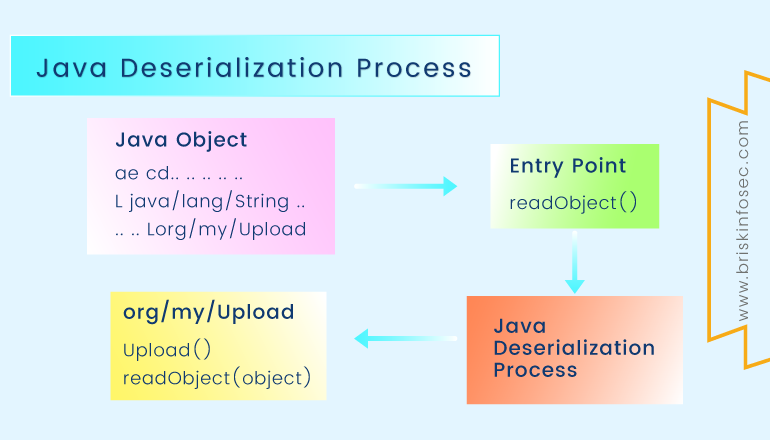
Now a days, Web application’s server side languages provide options to serialize and deserialize user’s input from the applications front-end. Input serialization is the process of converting user’s input into byte code for faster data processing. When the untrusted malicious user data is passed onto unserialize () function, it is possible for an attacker to exploit the web application by injecting server commands through the serialized inputs.
To prevent this, Input validation should be done on unserialize function where all the user inputs are deserialized. Also the use of insecure functions like eval() should be avoided.
Content Management System Vulnerabilities (CMS):
Content Management systems are used to manage the contents of the website or web application. It allows multiple users to create, design, and modify the web contents and publish them. There are many open source CMS available online like WordPress, Drupal, Joomla, etc.
Type of Vulnerability: Code and Configuration Level

All these Content management systems are vulnerable to various web application vulnerabilities which may compromise the application. For example, let’s take WordPress CMS which is affected by many types of web application vulnerabilities.
Vulnerabilities which commonly affect the CMS applications are Cross site Scripting, Remote code execution, SQL Injection, etc.
In WordPress, if the user registration action is not setup properly or if it is not disabled after publishing the web application, a malicious intruder can create a WordPress user account in the context of that web application by using the URL GET request like below:
https://example.com/wp-login.php?acti>
Server Side Request Forgery (SSRF)
Server Side Request Forgery (SSRF) is one of the trending web application vulnerability in which a malicious intruder can forge the request which is going to the vulnerable server. Using SSRF attack, it is possible to access the internal resources of the web server, and access the external websites in the context of vulnerable web application. Therefore, attackers can execute a DDOS attack on a website using the web application which is vulnerable to SSRF.
Types of Vulnerability:Code Level
Below image demonstrates the working of SSRF attack.
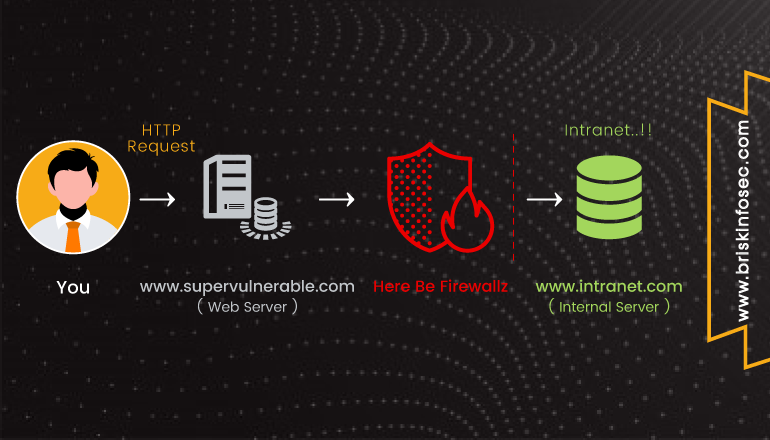
Let’s look at a demonstration of SSRF in a vulnerable web application. In this, the attacker uses the vulnerable application to check the internal web server’s open ports (Cross Site Port Attack XSPA), due the SSRF vulnerability.
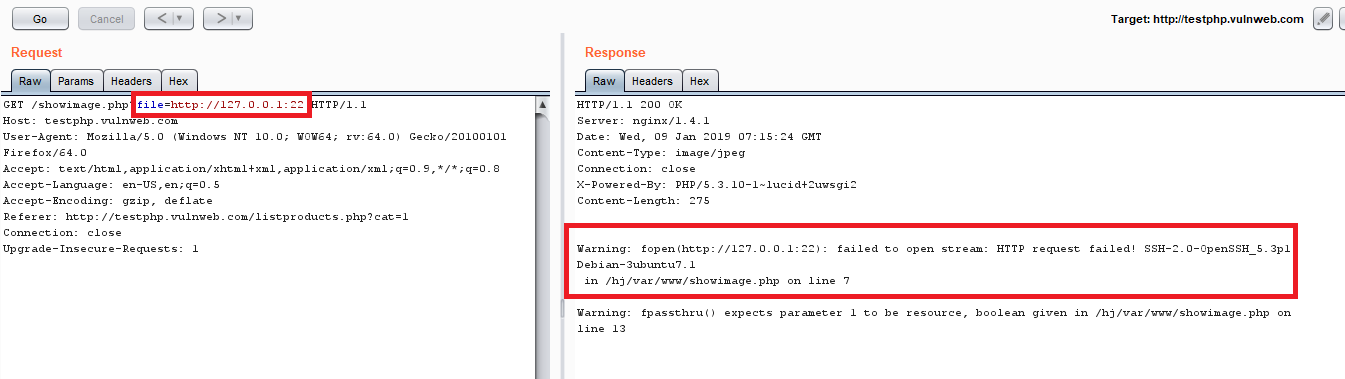
In the example, I had provided an internal URL pointing to port 22 (SSH) and in response I could see the SSH server’s banner is displayed, indicating the port is open.
Apache Struts Framework RCE Vulnerability:
Apache struts framework is an open source framework for developing and publishing modern Java based web applications. In recent times, apache struts plugin is affected by lot of vulnerabilities and the most notable among them is the Remote Code Execution (RCE) vulnerability.
Types of Vulnerability: Code Level
Apache struts plugin is affected with RCE vulnerability and the CVE is CVE-2018-11776. Due to this flaw, a lot of data breach has happened around the world in recent past. One example is the Equifax Data breach that happened due to the usage of outdated version of apache struts plugin in their server.
XML External Entity and XML Injection:
Apart from the vulnerabilities which affects the CMS systems or server plugins, exploiting the XML parsers and external entity function became a trend in web application security in recent times.
Type of Vulnerabilities: Code Level
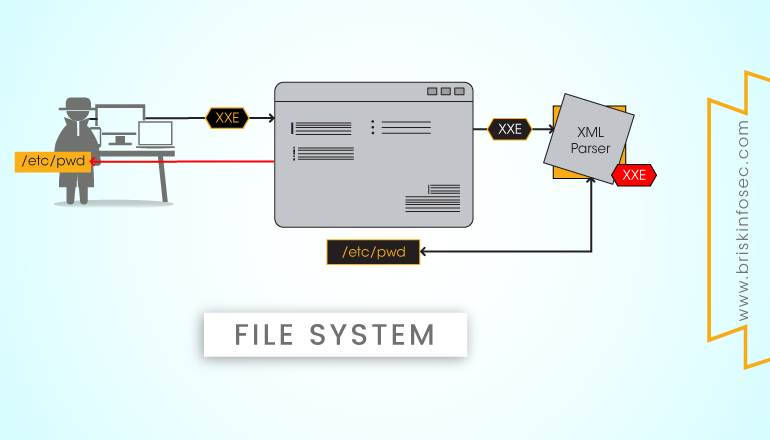
XML Injection/XML External Entity (XXE) injection is an injection or input validation vulnerability, present in modern web applications which uses XML parsers to process user’s input in the backend server.
Any malicious intruder can send a specially crafted XML payload with the external entity function pointing towards some sensitive data like the passwd file in server to fetch the file contents.
Simple XXE Injection payload given below:
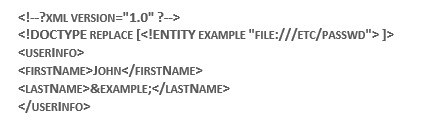
The above payload can be inserted in the GET or POST request of the user’s input to fetch the contents of password file.
AI Powered Attacks:
Artificial Intelligence (AI) is used by developers to create more robust and efficient web applications in modern days. But the same AI can be used in a malicious way to carry out attacks on the web applications.
Type of Vulnerability: Code and Algorithm Level
AI powered algorithms can be used by malicious intruders to find out little known vulnerabilities or hidden locations of the web server and exploit them. One of the advantages of using AI for cyber-attacks is that, it will be very much helpful for the attackers and testers to analyse the web application’s vulnerabilities based on its behaviour.
When used for securing web applications, AI powered vulnerability scanners are being developed in recent times. The advantage of these scanners are that, they will reduce the false positive results to a great extent when compared to the traditional web application vulnerability scanners.
AI algorithms can be used to scan for a vulnerability either statically or dynamically, and then confirm the vulnerability by trying a simple exploit on the given application’s URL or function.
Blind Cross Site Scripting (XSS):
Cross site scripting (XSS) is well known and highly exploited vulnerability which lurks furtively in cyber world, over a decade. In recent times, due to the use of customized frameworks and secure code by developers, it became little hard for an attacker to find and exploit a XSS vulnerability in an application.
Type of Vulnerability: Code Levels
Blind XSS is a new type of XSS vulnerability, which is being discovered and exploited in the wild. The advantage of this vulnerability is that, attacker injects the JavaScript payload in one location (ex: feedback page) and even if the developer validates the input in that location, there will be high probability that the JavaScript gets executed in a completely different location (ex: admin page, where admin checks all feedbacks).
Below image shows the Attack flow of Blind XSS:
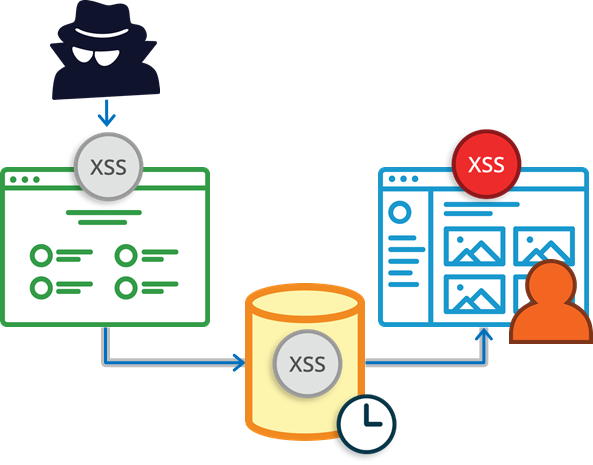
Blind XSS occurs, when the user input from one location is stored in database and gets loaded in completely different location of the web application.
APIs Endpoint based Vulnerability:
Application Program Interface (APIs) are defined functions and communication protocol, to connect the front end web application with the various services available in the backend server.
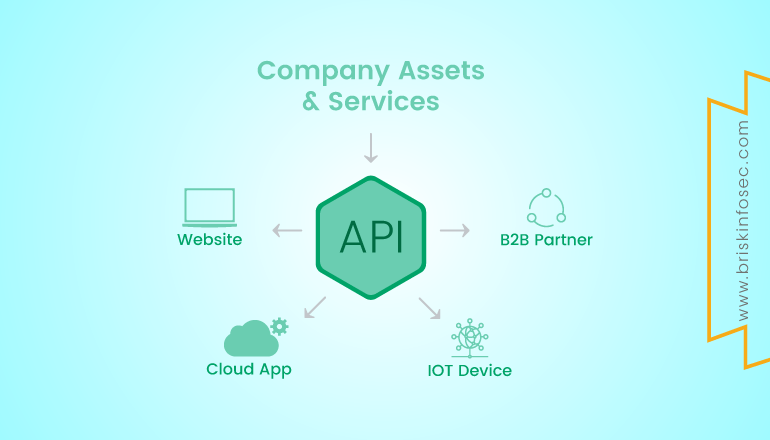
Types of Vulnerabilities: Code Level
In simple words, API serves the purpose of intermediate function to carry user’s data in web API request to the backend services. For this purpose, an API server is configured with endpoints. An endpoint is a URL or request in general and is used to serve one purpose for the application’s user. Ex: user login endpoint is used to authenticate users to the application by assigning a user token or cookie (generally JSON Web Tokens) to the user’s browser session.
APIs are prone to many vulnerabilities just like the normal web applications. An attacker can try to execute XSS payloads, or try to inject database queries to retrieve the server’s database etc.
An example for XSS attack in API endpoint is given below:
https://api.example.com/user/login?usertoken=”>
An example for Local File Inclusion through API endpoint:
https://api.example.com/user/profile?file=/etc/passwd
An example of SQL injection through API endpoint:
https://api.example.com/user/?page_id=1’ AND SELECT db_name from table
Below image shows the user login in API endpoint:
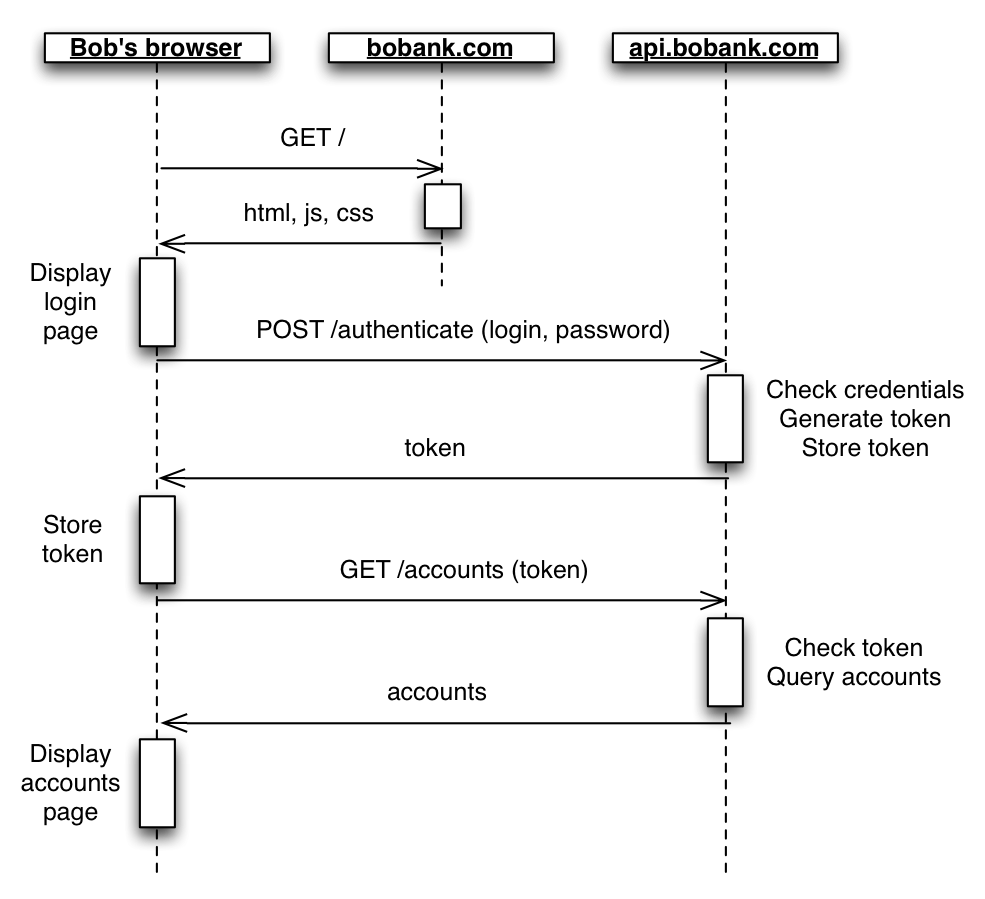
Server Side Template Injection (SSTI):
Template Engines are used in web applications for presenting the dynamic web application content to the end users via emails or web pages. Template Injection is a type of vulnerability which is exploited in recent times due to the increased usage of web application templates by developers, to present end users with dynamic web content in faster way.
Type of Vulnerability: Codes Level
Some of the commonly used web application template engines are Twig and FreeMarker. Template injection occurs when the user input is inserted in the server side template engine without proper input validation. Template injection is confused with XSS attacks some times. Unlike XSS attacks, Server side template injection can compromise the server to carry out Remote Code Execution (RCE) on the server side.
Example server side code of Template Engine:
$output = $twig->render("Dear {first_name},", array("first_name" => $user.first_name) );
In the above code sample, one can clearly see that the user input is inserted into the Template function without any input validation in the server side.
Hostile Sub-Domain Takeover Vulnerability:
Hostile Sub-Domain takeover is one of the rarely found and exploited web application vulnerability. In recent times, there are many companies who register their services (sub domains) with third party service providers for purposes like mail service, customer support etc. If the registered domain is not maintained properly or if not used with account details unremoved, it is possible for an attacker to register in the name of a given company in that third party site and take ownership of the sub-domain.
Types of Vulnerability: Code and Configuration Level
There are lot of automated scanners available in code repositories like GitHub for finding the unused sub-domains of an organization. Some of the best known tools are Hostile-subbruteforcer, aquatone etc.
Hostile-Subbruteforcer
https://github.com/nahamsec/HostileSubBruteforcer
Aquatone
https://github.com/michenriksen/aquatone
Below image shows the example scenario of hostile sub-domain scanning:
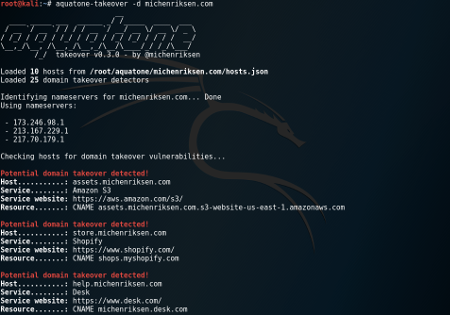
Conclusion:
These are some trending web application vulnerabilities which are exploited more in the recent times by attackers and penetration testers. Cyber security is always a continuous process, therefore it is necessary for any Organization to carry out a Security Assessment or Penetration Testing on their web applications and products to keep it secure from the emerging attacks of modern cyber world.
How Briskinfosec helps you?
Briskinfosec provides top notch cybersecurity assessments for a wide array of security requirements. We have an expert team of security professionals experienced in web applications security. Our security quality has always surpassed the expected quality of our clients. Moreover, you’ll be working the organisation who has been listed as one among the “Top 20 Most Promising Cyber Security Provider” consistently for two years, and also with the one who set the “India Book of Records for identifying most number of vulnerabilities”.
Curious to read our case study?
Our stakeholder, one of the leading HR solutions company in Singapore, requested us to conduct security assessments on their web applications. We used our own created tools, along with manual and automated tools and completely performed the assessment. The security flaws were identified and rectified. Check out our case study and see our excellence in deliverance.
Last but not the least:
Briskinfosec prepares Threatsploit Adversary Report which contains a significant collection of global cyberattacks, the consequences faced by organisations, and much more. Just a single click on the above link. You’ll feel elated with what you’ve procured.



