What day is best for you?
- Sun
- Mon
- Tue
- Wed
- Thu
- Fri
- Sat
What time works?
30 minutes meeting
Asia/Kolkata Time
Almost there!
IST
Unlock the potential of your mobile applications with our tailored VAPT audit, engineered to meet the unique challenges of mobile platforms. Leveraging the MAST (Mobile Application Security Testing) framework alongside our dynamic LURA Portal, we offer a comprehensive security evaluation enriched with our exclusive bSAFE score for in-depth insights and unparalleled protection.
Our approach to Mobile App VA/PT is a holistic journey from initiation to certification, utilizing the MAST framework to ensure every aspect of your mobile app's security is scrutinized and fortified. This meticulous process ensures your mobile application adheres to stringent security standards, culminating in a respected certification that attests to your robust defense mechanisms.
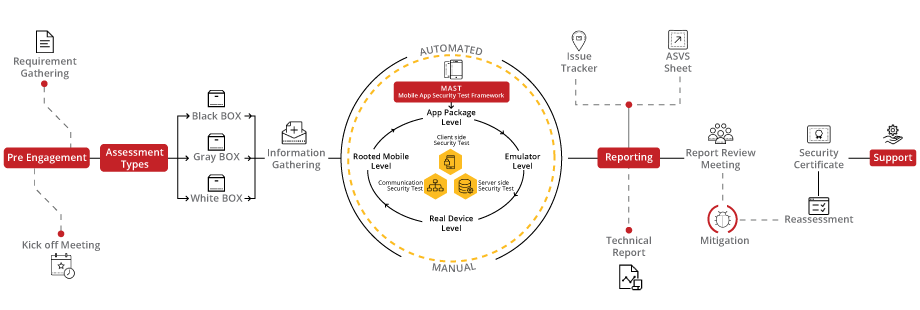
bSAFE delivers a detailed security maturity score for your mobile application, guided by best practices and industry standards to foster continuous improvement and resilience.
Organizations falling into this range have a robust and secure system. Encourage continuous monitoring and periodic security assessments to maintain the high security posture.
Indicates a satisfactory security level but with room for improvement.Suggest implementing additional security measures and staying vigilant to emerging threats.
Organizations in this range are considered fragile and may have significant vulnerabilities.Recommend patches, and strengthening overall security protocols.
The lowest score suggests a system with severe security vulnerabilities. Urgently address and remediate identified issues to prevent potential breaches.




Cybersecurity starts with proper awareness. Briskinfosec’s BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download one-page the Mobile App Security Flyer, Mobile App Security Case Study and Threatsploit Adversary report.

Your ticket to fortifying apps, ensuring robust cybersecurity, and inspiring user trust in the digital realm.

Unveiling success stories, showcasing our expertise in crafting secure, user-friendly, and innovative mobile solutions that redefine app experiences.

Your window into the evolving threat landscape, offering insights and intelligence to protect against emerging cyber dangers.
Lura cybersecurity simplified portal can help to reduce project execution time, save cost, and bring a positive return on investment (ROI) to customers:
Lura reduces the time spent on documentation and minimizes the overall duration of projects, saving time and resources.
Lura provides a convenient and secure way for customers to access status reports and VA/PT reports, improving efficiency and reducing the risk of errors.
Lura helps to ensure that our cybersecurity services meet the highest standards of quality and regulatory compliance, reducing the risk of costly compliance issues.
Lura is a secure and transparent platform that helps to ensure the integrity of security assessments and build confidence in the quality of our enterprise-grade tests.
Capturing the essence of unforgettable moments, our current event videos tell compelling stories that resonate with emotion and excitement.

Boost Your Security Today with Our Cybersecurity Self-Assessment Questionnaire! Ready to strengthen your organization's defenses? Our tailored questionnaire is your key to pinpointing vulnerabilities and fortifying your cybersecurity strategy. Download now for a secure tomorrow!
Celebrating our achievements and collaborations, shaping a future of excellence.

























Our Case studies are the best reference to prove the dexterity of Briskinfosec.




Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Biometric Identification has changed the way people were identified. Since the Last decade, its growth is incredible and has transformed a lot of industries from military
Read the blogServer-Side Request Forgery (SSRF) refers to an attack, wherein an attacker can send a maliciously crafted request from a vulnerable web application
Read the blogAndroid Manifest file provides the system with necessary data like application’s configuration information, permissions, and app components. Android Manifest File can be obtained by extracting any APK File and also while doing assessment, you can use APKtool & Drozer for extracting the Manifest file from the application.
Read the blogBrowse our selection of handy cybersecurity tools. Arm yourself with the right defenses to safeguard your digital life.
Domain name permutation engine for detecting homograph phishing attacks
Read the tool of the dayFrida IPA/iOS dump is an instrument whose primary point is to download IPA files from an jailbroken device
Read the tool of the dayElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Discover our vault and dive into our Carousel for dynamic updates, explore our Infographics for simplified knowledge, and browse our Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!



Embark on a journey through BriskInfoSec's comprehensive suite of cybersecurity services, safeguarding your digital landscape with tailored expertise.






Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment