Table of Contents
In today's interconnected digital landscape, web applications serve as the backbone of numerous online services, facilitating everything from e-commerce transactions to social media interactions. However, with this increased reliance on web applications comes the heightened risk of cyber threats and attacks. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in web applications to gain unauthorized access to sensitive data or disrupt services.
To combat these threats effectively, organizations must adopt a proactive approach to web application security. This is where Web Application Vulnerability Assessment and Penetration Testing (Web App VAPT) comes into play.
What is Web App VAPT?
Web Application Vulnerability Assessment and Penetration Testing (Web App VAPT) encompasses a proactive approach to identifying and addressing security vulnerabilities within web applications.
Vulnerability Assessment involves systematically scanning web applications to uncover potential weaknesses and vulnerabilities exploitable by malicious actors. This process typically employs automated tools and manual inspections to comprehensively assess the application's security posture.
On the other hand, Penetration Testing involves simulating real-world cyber-attacks to evaluate the effectiveness of existing security controls. Ethical hackers, known as penetration testers, employ various techniques to exploit vulnerabilities and gain unauthorized access to systems and data. This hands-on approach provides valuable insights into an application's security vulnerabilities and weaknesses.
Importance of Web App VAPT:
The importance of Web App VAPT cannot be overstated in today's threat landscape. Cyber-attacks targeting web applications are on the rise, with attackers constantly evolving their tactics to exploit vulnerabilities and compromise sensitive data.
Conducting regular Web App VAPT assessments enables organizations to:
Mitigate Security Risks: Identifying and addressing vulnerabilities early in the development lifecycle helps mitigate security risks and prevent potential data breaches or cyber-attacks.
Maintain Regulatory Compliance: Compliance with industry regulations and standards, such as PCI DSS, GDPR, and HIPAA, requires organizations to conduct regular security assessments, including vulnerability assessments and penetration testing.
Protect Brand Reputation: A data breach or security incident can have severe repercussions for an organization's brand reputation and customer trust. Proactively addressing security vulnerabilities minimizes the risk of reputational damage.
Demonstrate Due Diligence: Conducting Web App VAPT assessments demonstrates due diligence and a commitment to cybersecurity best practices, instilling confidence in stakeholders and customers alike.
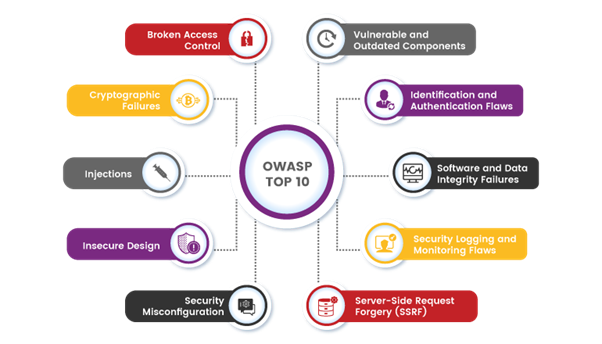
Web Application Vulnerabilities:
Web application vulnerabilities pose significant risks to the security and integrity of online systems. Understanding these vulnerabilities is crucial for effectively mitigating risks and fortifying defenses. Here are some common web application vulnerabilities:
Injection Attacks: SQL Injection, NoSQL injection, and LDAP injection are prevalent vulnerabilities allowing attackers to execute malicious code by inserting unexpected input into data queries or commands.
Cross-Site Scripting (XSS): XSS vulnerabilities enable attackers to inject malicious scripts into web pages viewed by other users, potentially leading to data theft, session hijacking, or website defacement.
Cross-Site Request Forgery (CSRF): CSRF attacks trick users into executing unintended actions on a web application where they are authenticated, leading to unauthorized transactions or data manipulation.
Broken Authentication: Weak authentication mechanisms, such as insecure password storage or session management flaws, expose user accounts to compromise.
Sensitive Data Exposure: Failure to adequately protect sensitive data, such as passwords or credit card numbers, results in data breaches and exposes users to identity theft or fraud.
Security Misconfigurations: Improperly configured web servers, databases, or application frameworks may leave system vulnerabilities exposed, allowing attackers to exploit weaknesses and gain unauthorized access.
Insecure Deserialization: Insecure deserialization vulnerabilities can lead to remote code execution or denial-of-service attacks by allowing attackers to manipulate serialized data objects sent between applications.
Understanding these vulnerabilities is essential for conducting effective vulnerability assessments and penetration tests, enabling security professionals to prioritize remediation efforts and implement targeted security controls.
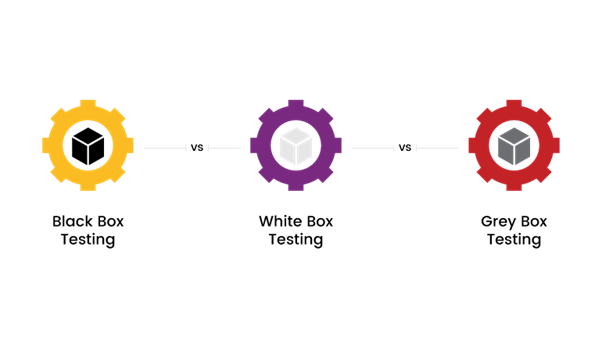
Methods and Techniques:
Various methods and techniques are employed in vulnerability assessment and penetration testing to identify and mitigate web application vulnerabilities:
Black-box Testing: Black-box testing simulates an attacker's perspective by assessing an application without any prior knowledge of its internal workings or architecture. Testers interact with the application as an external user, probing for vulnerabilities and weaknesses.
White-box Testing: White-box testing, also known as clear-box testing or structural testing, involves assessing an application's internal architecture, codebase, and configurations. Testers have full access to the application's source code and can perform in-depth analysis to identify vulnerabilities and security flaws.
Grey-box Testing: Grey-box testing combines elements of both black-box and white-box testing methodologies. Testers have limited access to an application's internal architecture or codebase, allowing them to assess security from a semi-informed perspective.
Manual Testing: Manual testing involves human intervention to identify vulnerabilities that automated tools may overlook. Manual testing techniques include code review, threat modeling, and manual exploitation of vulnerabilities to assess their impact.
Automated Testing: Automated testing utilizes specialized tools and scripts to scan web applications for known vulnerabilities and security weaknesses. Vulnerability scanners, such as Burp Suite, OWASP ZAP, and Nessus, automate the process of identifying common vulnerabilities like SQL injection, XSS, CSRF, and more.
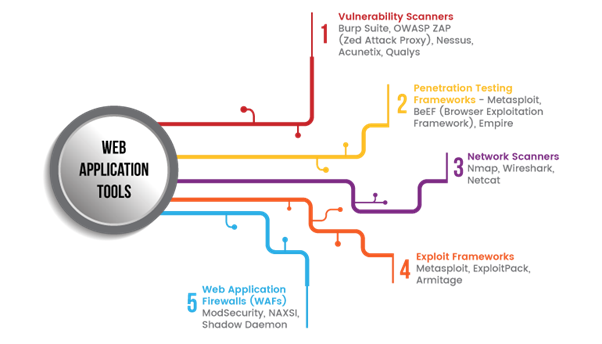
Tools and Technologies:
A wide array of tools and technologies are available to support vulnerability assessment and penetration testing efforts:
Vulnerability Scanners: Vulnerability scanners automate the process of identifying security vulnerabilities in web applications, networks, and systems. Popular vulnerability scanning tools include Burp Suite, OWASP ZAP, Nessus, Acunetix, and Qualys.
Penetration Testing Frameworks: Penetration testing frameworks provide comprehensive suites of tools and scripts for conducting penetration tests and security assessments. Frameworks such as Metasploit, BeEF, and Empire facilitate various stages of the penetration testing lifecycle, including reconnaissance, exploitation, post-exploitation, and reporting.
Network Scanners: Network scanners, such as Nmap, Wireshark, and Netcat, enable security professionals to gather information about target systems and networks, identify open ports, services, and vulnerabilities, and assess network security posture.
Exploit Frameworks: Exploit frameworks like Metasploit offer a repository of pre-built exploits and payloads for targeting vulnerabilities in web applications, operating systems, and network devices. These frameworks streamline the process of testing and validating vulnerabilities in a controlled environment.
Web Application Firewalls (WAFs): Web application firewalls are security appliances or software solutions designed to protect web applications from common security threats, including SQL injection, XSS, CSRF, and more. WAFs like ModSecurity provide a layer of defense against malicious traffic by filtering and blocking potentially harmful requests before they reach the application server.
Best Practices:
Effective vulnerability assessment and penetration testing rely on adherence to best practices to ensure comprehensive coverage and accurate results:
Regular Assessments: Conduct regular vulnerability assessments and penetration tests to proactively identify and address security vulnerabilities before they can be exploited by attackers.
Collaboration: Foster collaboration between security teams, development teams, and other stakeholders to ensure a holistic approach to web application security. Establish clear communication channels and workflows for reporting and remediation of vulnerabilities.
Continuous Monitoring: Implement continuous monitoring mechanisms to track changes in the security posture of web applications and detect new vulnerabilities or emerging threats in real-time.
Stay Informed: Stay abreast of emerging threats, vulnerabilities, and security trends by participating in industry forums, attending conferences, and engaging with the cybersecurity community. Leverage threat intelligence feeds and security advisories to stay informed about the latest security risks and mitigation strategies.
Patch Management: Implement robust patch management processes to promptly address security vulnerabilities identified during vulnerability assessments and penetration tests. Regularly update software, applications, and libraries to mitigate known vulnerabilities and reduce the attack surface.
By adhering to these best practices, organizations can enhance the effectiveness of their vulnerability assessment and penetration testing efforts, mitigate security risks, and fortify their web applications against potential threats.
Conclusion:
Web App VAPT plays a vital role in securing web applications against cyber threats. This guide covers methods like black-box, white-box, and grey-box testing, as well as manual and automated approaches. Key tools and technologies, including vulnerability scanners, penetration testing frameworks, and web application firewalls, are also discussed. Adhering to best practices such as regular assessments, collaboration, continuous monitoring, staying informed, and robust patch management significantly enhances Web App VAPT effectiveness.
This blog provides a thorough understanding of Web App VAPT, enabling proactive measures to safeguard web applications from evolving cyber threats.