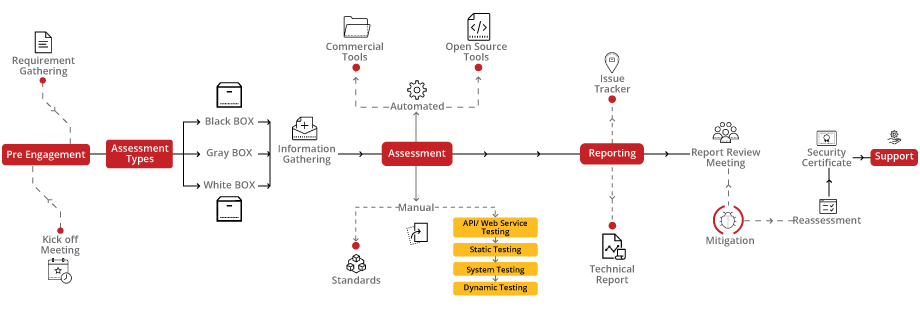
Elevate your thick client applications security with our specialized VA/PT audit, specifically designed for the unique security challenges of desktop and standalone applications. Our approach integrates comprehensive testing techniques to uncover vulnerabilities that could compromise your thick client software, ensuring thorough protection and resilience against cyber threats.
Our Thick Client VA/PT methodology provides an end-to-end security evaluation, from the initial analysis to the final certification. This process is crafted to meticulously assess and enhance the security of your thick client applications, leveraging advanced testing tools and techniques to identify and rectify vulnerabilities effectively, ensuring your software meets the highest standards of security.
bSAFE provides a comprehensive maturity score for your web application security, aligning with OWASP ASVS standards to guide improvements and ensure continuous security enhancement.
Organizations falling into this range have a robust and secure system. Encourage continuous monitoring and periodic security assessments to maintain the high security posture.
Indicates a satisfactory security level but with room for improvement.Suggest implementing additional security measures and staying vigilant to emerging threats.
Organizations in this range are considered fragile and may have significant vulnerabilities.Recommend patches, and strengthening overall security protocols.
The lowest score suggests a system with severe security vulnerabilities. Urgently address and remediate identified issues to prevent potential breaches.




Cybersecurity starts with proper awareness. Briskinfosec BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download the Thick Client Security Flyer, Thick Client Security Case Study and Threatsploit Adversary Report.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Nowadays the biggest danger that we come across and also something that we are about to face in future is The cyber threat the crime that happens via internet and technology.
Read the blogVarious people use various applications for getting their various needs done. Amongst those applications that’re used, the most prominent one’s are thick-client applications.
Read the blogOWASP is the blueprint for testing the web application security controls. It is safe to say that it helps the developers to develop application.
Read the blogElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.