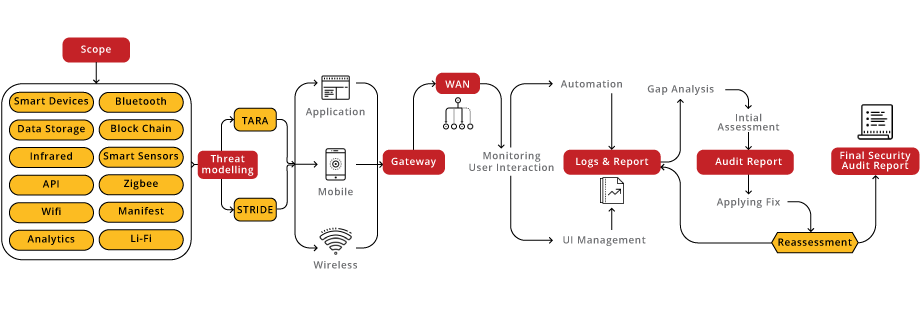
Our IoT Security Audit service is a comprehensive solution tailored to address the unique challenges of Internet of Things (IoT) devices. Leveraging industry best practices and guided by the OWASP IoT Top 10, our approach encompasses a thorough examination of device vulnerabilities, network security, data privacy, and firmware integrity.
IoT VA/PT Hybrid Approach seamlessly integrates automated scans with expert analysis, ensuring a thorough evaluation of IoT security. By combining technology and human insight, it identifies vulnerabilities, fortifies defenses, and guarantees secure and resilient IoT environments.
bSAFE score furnishes a detailed evaluation of your IoT Product security maturity, promoting ongoing improvements and resilience.
Organizations falling into this range have a robust and secure system. Encourage continuous monitoring and periodic security assessments to maintain the high security posture.
Indicates a satisfactory security level but with room for improvement.Suggest implementing additional security measures and staying vigilant to emerging threats.
Organizations in this range are considered fragile and may have significant vulnerabilities.Recommend patches, and strengthening overall security protocols.
The lowest score suggests a system with severe security vulnerabilities. Urgently address and remediate identified issues to prevent potential breaches.




Cybersecurity starts with proper awareness. Briskinfosec BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download the one-page IoT Security Flyer, IoT Security Case Study and Threatsploit Adversary Report.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Nowadays the biggest danger that we come across and also something that we are about to face in future is The cyber threat the crime that happens via internet and technology.
Read the blogThe term Internet of Things"was first used in 1999 to promote a technology called Radio Frequency Identification. IoT didn't become more popular until 2010/2011. By early 2014, it was used by most people. IoT forensics is a type of digital forensics that looks
Read the blogBiometric Identification has changed the way people were identified. Since the Last decade, its growth is incredible and has transformed a lot of industries from military
Read the blogElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.