What day is best for you?
- Sun
- Mon
- Tue
- Wed
- Thu
- Fri
- Sat
What time works?
30 minutes meeting
Asia/Kolkata Time
Almost there!
IST
Elevate your website's security landscape with our specialized VAPT audit, designed to navigate the complexities of web security. Our audits, enriched by the comprehensive OWASP framework and the innovative LURA Portal, are complemented by the exclusive bSAFE score, offering unparalleled insights and a robust security framework for your website.
Our Website VA/PT approach is a detailed expedition from the initial engagement through rigorous assessment, reassessment, and ultimately certification. This journey, grounded in the OWASP framework, is carefully crafted to align your website's security with the highest standards, culminating in esteemed certification as proof of your advanced cyber defense capabilities.
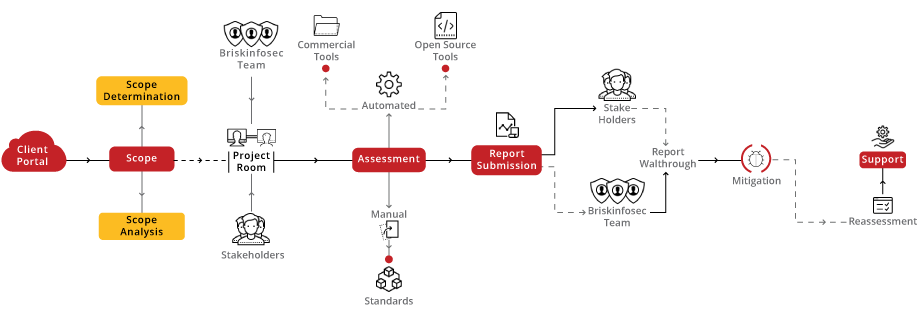
he bSAFE score furnishes a detailed evaluation of your website's security maturity, promoting ongoing improvements and resilience
Organizations falling into this range have a robust and secure system. Encourage continuous monitoring and periodic security assessments to maintain the high security posture.
Indicates a satisfactory security level but with room for improvement.Suggest implementing additional security measures and staying vigilant to emerging threats.
Organizations in this range are considered fragile and may have significant vulnerabilities.Recommend patches, and strengthening overall security protocols.
The lowest score suggests a system with severe security vulnerabilities. Urgently address and remediate identified issues to prevent potential breaches.




Cybersecurity starts with proper awareness. Briskinfosec’s BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download the One-page Website Security Flyer, Website Security Case Study and Threatsploit Adversary report.

Your compass to a secure online presence, showcasing our expertise in safeguarding web integrity and highlighting real-world examples of fortified websites against cyber threats.

Dive into our Website Security Case Studies, where success stories unfold, demonstrating how we fortified websites against cyber threats.

Your window into the evolving threat landscape, offering insights and intelligence to protect against emerging cyber dangers.
Lura cybersecurity simplified portal can help to reduce project execution time, save cost, and bring a positive return on investment (ROI) to customers:
Lura reduces the time spent on documentation and minimizes the overall duration of projects, saving time and resources.
Lura provides a convenient and secure way for customers to access status reports and VA/PT reports, improving efficiency and reducing the risk of errors.
Lura helps to ensure that our cybersecurity services meet the highest standards of quality and regulatory compliance, reducing the risk of costly compliance issues.
Lura is a secure and transparent platform that helps to ensure the integrity of security assessments and build confidence in the quality of our enterprise-grade tests.
Celebrating our achievements and collaborations, shaping a future of excellence.

























Our Case studies are the best reference to prove the dexterity of Briskinfosec.




Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
In today's interconnected digital landscape, web applications serve as the backbone of numerous online services, facilitating everything from e-commerce transactions to social media interactions.
Read the blogGitHub is a hosting platform which helps developers to collaborate in building software’s. It helps the developers to manage source code management.
Read the blogCross-site scripting (XSS) is one of the most prevalent, obstinate, and dangerous vulnerabilities in web applications.
Read the blogBrowse our selection of handy cybersecurity tools. Arm yourself with the right defenses to safeguard your digital life.
peepdf is a Python tool to explore PDF files in order to find out if the file can be harmful or not
Read the tool of the dayElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Discover our vault and dive into our Carousel for dynamic updates, explore our Infographics for simplified knowledge, and browse our Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!



Embark on a journey through BriskInfoSec's comprehensive suite of cybersecurity services, safeguarding your digital landscape with tailored expertise.






Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment