Contents
- Overview
- What is a Ransomware Attack?
- Evolution of Ransomware over the period of time:
- Top 6 Worst Ransomware
- Top 5 Biggest Ransomware Payouts of all time
- Horrible and shocking Ransomware Statistics facts in previous years
- Best Practices that will reduce the Risk of Ransomware Impacting Your Business
- Conclusion
Overview
Nowadays the biggest danger that we come across and also something that we are about to face in future is “The cyber threat,”the crime that happens via internet and technology. Nowadays, the hackers are becoming more matured and they find a lot of new ways to make money from cyberspace by making people as victims. In this we are going to see about a cyber-threat that ranks on the top of the table and ruled for nearly two decades and in future also “The Ransomware”.
Ransomware is really a major threat to individuals, businesses and public sectors and even government that can shut-down their network, productivity, reputation and finally data and financial losses. In the fast-growing technology, the Ransomware is going to take more new dimensions in future instead of ending.
Let us look into the origin, rapid evolution over the time, major ransomware attack, its damages and payouts statistics and the best practices that may help an individual or an organization to prevent data and business loss in detail.

What is a Ransomware Attack?
Ransomware is a form of malware or a crypto virus that prevents the users from accessing their systems or data by encrypting it until a requested amount of money is paid as a ransom to decrypt them back.
Evolution of Ransomware over the period of time:
Ransomware is not like the other common types of malware that affect the end-user, the possibility of damage & risk involvement is formidable and the threat has been evolving over a period of time. Ransomware has been really evolving for nearly two decades now, Its growth and dimension shows a tremendous sign of progress that threatens the world and it does not seems to end now or in the future also. Let's take a look at its evolution,
The first known malware extortion attack happened in 1989 called AIDS Trojan that was spread by a Harvard Academic namely Joesph L Popp via Floppy Disks for the delegates who attended W.H.O AIDS Conference. The idea of ransomware was reinvented nearly after a one and a half decades later as the internet got evolved. The word Ransomware became famous during 2005-2006 as many ransomware came to existence such as GPCode, Archievus, Krotten, Cryzip, GPCode. AK. They used a complex encryption scheme with strong key sizes like 660-bit RSA (GPCode.AG) and 1024-bit (GPCode.AK) RSA keys which involves a lot of effort and high computational mechanism to break.
Then in 2012-2013, the encrypting ransomware was returning to the top of the cyber threat as it adopts the platform of Digital Cryptocurrency as a mode to collect ransom from the victims as it is an untraceable and anonymous payment method. In 2012, the Reveton payload spread and also known as Police Ransomware it displays a fake warning message stating that ‘your system was locked down for doing illegal activities,’ and demands them to pay the fine (ransom) via anonymous cash service Ukash and Paysafecard online to unlock the system back. In 2013 CryptoLocker ransomware which uses the 2048-bit RSA key to encrypt has extorted nearly US $3 million from the victims over Bitcoin cryptocurrency. The Technique of CryptoLocker prevailed form 2013-late May 2014 and it also got many forms such as CryptoLocker 2.0, CryptoDefense.
Click here to know more about Securing your Network
Top 6 Worst Ransomware
From 2015 to now the ransomware has taken several dimensions and many new ransomware is rising every year. Let us look into some of the worst ransomware that affects millions across the globe.
SimpleLocker 2014
SimpleLocker was the first Android-specific ransomware as the hackers understand that hype in the android market as it holds 75% of the market share at the time. So they find the mobile platform to yield more profit to them. SimpleLocker encrypted files and data such as photos, videos, documents for ransom by delivering malicious payload in the form of the trojan downloader and which is impossible to break without the help of the creator. The main reason for this type of android ransomware infection is, while downloading and installing applications that are suspicious and from unknown third parties instead of downloading it from the authorized trustworthy source like (Google play, Apple store, Galaxy store, etc).
TeslaCrypt 2015
TeslaCrypt ransomware was introduced in February 2015. It targeted the gamers and infects the game-play data for a few computer games like Call of Duty series World of Warcrafts, Minecraft and World of Tanks. It encrypts the SaveData, Player Profiles, Custom maps, and Game modes files of the games that are stored on the victim’s hard drive. TeslaCrypt mostly affects the gamers in the US, UK, Spain, France, Germany, Italy infecting the files such as game saves and user profiles. It demanded the victims to pay a ransom of $500 to decrypt the infected files and the ransom will be doubled if they delayed paying. TeslaCrypt had made up 48% of Ransomware Attacks.
WannaCry 2017
WannaCry Ransomware attack was a worldwide cyberattack that happened in May 2017 which targeted windows based systems and demand the ransom in Bitcoin. It proliferates via the exploit called Eternal Blue which was leaked from NSA by a hacking group called The Shadow Brokers. This Ransomware attack was one of the largest attacks as it infected more than 230,000 computers in over 150 countries using 20 different languages. They demanded a ransom of US$300 per infected computer with a deadline of 7 days after that the encrypted files would be deleted. The attack hits many organizations such as Telefonica, National Health Service, FedEx, Honda, Renault, MegaFon, Russian Interior Ministry, Deutsche Bahn.
Petya 2016-2017
Petya is an encrypting Ransomware that was found in 2016.Petya affects the windows based system by infecting the Master Boot Recorder (MBR) to execute a payload that encrypts the hard drives’ file tables (NTFS) of the file system and blocks the windows from booting and demanded the ransom in Bitcoin. Petya also used Eternal Blue exploit like WannaCry ransomware. It is believed that Petya was developed by the National Security Agency (NSA) targeting Russia.
SamSam 2016
In 2016 a new ransomware strikes that target the JBoss servers called SamSam that exploits the vulnerabilities on weak servers. This ransomware uses the RDP brute-force attack to break into the system which has weak passwords. SamSam majorly hits the government organizations, healthcare sectors in the Town of Farmington New Mexico, the Colorado Department of Transportation, Davidson Country, North Carolina and the infrastructure of Atlanta which is a major security breach in recent times. Two Iranian hackers were wanted by the FBI for launching this ransomware attack. The two hackers have made extortion of $6 million and caused $30 million in damages using this malware.
Ryuk 2018-2019
Ryuk is one of the Ransomware types that hit big from 2018-2019 that targets the organization with less resistance downtime. It affects US local government sectors Rivieria beach, Florida Lake City, Georgia. Ryuk earned around $640000+ BTC.
Top 5 Biggest Ransomware Payouts of all time
Attack on South Korean web hosting providers Nayana ($1million)
In June 2017, hackers took down more than 153 Linux Servers of south Korean hosting providers have hosted and shut down nearly 3400 websites by spreading ransomware and demanded $4.4 million in Bitcoins to free up all the servers. Then after some negotiations with the hackers, the ransom was reduced as $1 million. This was the largest known payout for a ransomware attack that too by one company.
Florida Riviera beach Attack ($600000)
Florida’s largest city Riviera met with a ransomware attack that paralyzed the city’s computer system for nearly three weeks and demanded a ransom of $600000 to unlock the systems back. Then after three weeks, The Riviera Beach City Council agreed with the demand of the hackers.
Florida Lake City Attack ($500000)
In a three week timespan, another city in Floria called Lake City was hit by a ransomware attack called Ryuk. The city authorities were forced to pay the ransom of $500000 in exchange for unlocking email accounts and the communication between the government officials, their co-workers, and the public.
Anonymous Canadian Organization ($335,000)
A Leading Canadian company had hit with the ransomware attack that encrypts both the production and the backup databases and made the company inoperative. The hacker demanded a ransom of CA$425000 (US$335,000) to restore the systems to normal. It is believed to be the largest ransomware payment for one single company in Canada to date.
Ransomware attack in Jackson County, Georgia ($400000)
US local governments had become one of the most common targets for ransomware attacks. Jackson Country officials had paid $400000 to the hackers to get the decryption key and to regain the access over the infected files from the ransomware attack as it hit the countries internal network and made most of the local government IT systems down except 911 and some websites.
Horrible and shocking Ransomware Statistics facts in previous years
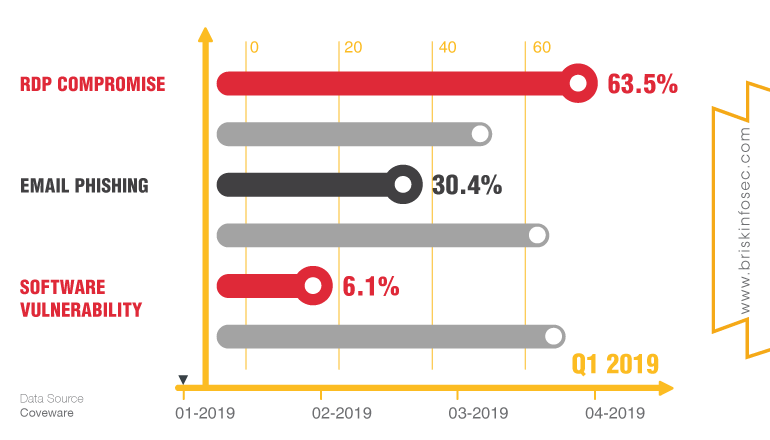
Most Common Ransomware Attack Vectors 2019 In what ways a ransomware can affect the victims and the type of vectors by which it infects are shown below.
Most Prevalent Ransomware Variant 2019
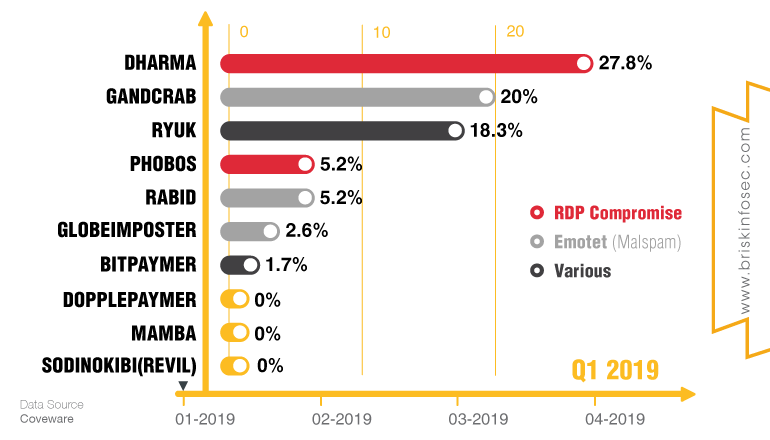
The above chart tracks the shifting “market share” of the most active ransomware operations based on infections reported to ransomware incident response specialists Coveware.
Ransom demand and payment sum increased abruptly and rapidly in 2019
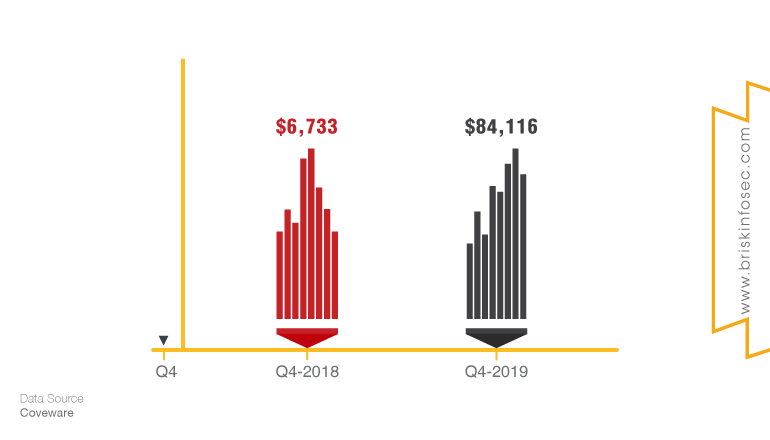
Coverware states that it’s not the average amount demanded in Q4 2019. It is the average amount paid up from an average of $6,733 just 12 months prior.
The Average Period of Downtime caused by Ransomware Attack increased 2.6X times in 2019
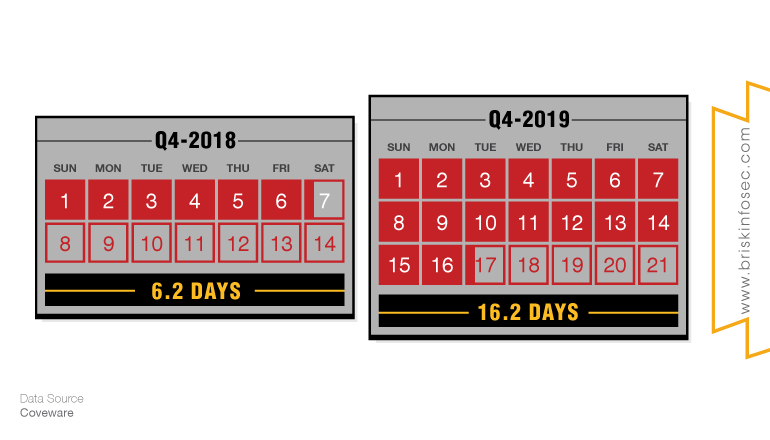
Beyond the jaw-dropping hike in ransom amounts, another extremely important number that resides with the current ransomware attack is 16.2 days (which is the average number of days that an organization takes to recover from the infection.)
As the business downtime period increases then the production and the cost associated with the ransomware related downtime are also going up to the organization.
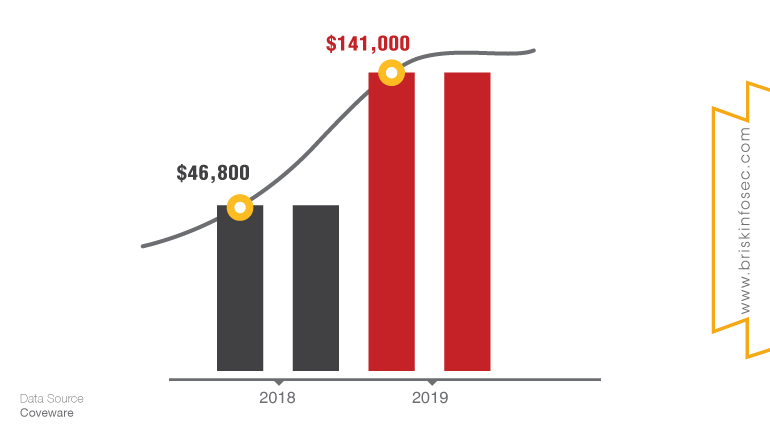
These facts are sobering. How many organizations especially (Small and Medium-sized Business) can afford $141,000, and how can bear more than two weeks of downtime and disruption in the business?
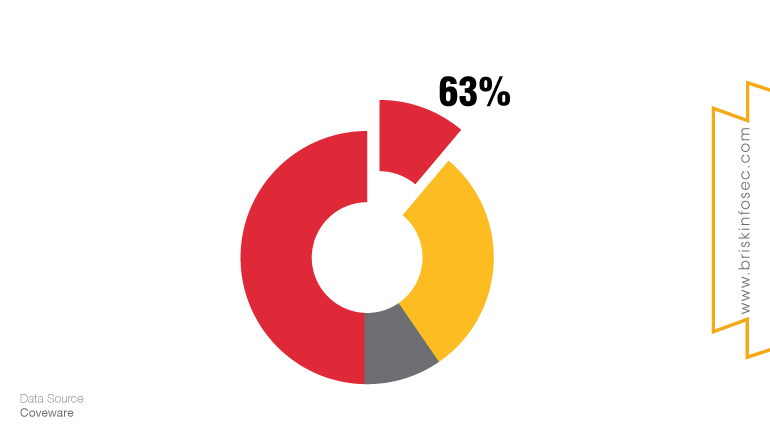
Who is being targeted most?
People only know the attacks that happen on a large organization like Travelex and Municipalities which is widely known to everyone but the actual truth is nearly two-third of ransomware victims in 2019 were small and medium-sized businesses who obviously do not aware about cyber-threats.
Best Practices that will reduce the Risk of Ransomware Impacting Your Business
Here are some key tips that may safeguard your organization from Ransomware:
- Maintaining Data Backups – The strongest defenses against ransomware attack is to have Backups of Business Critical Data in both cloud and in local environment. These backups must be encrypted, de-militarized from the public facing internet and password protected.Backup files should be tested regularly to ensure data is complete and not corrupted.
- Approach of White Listing – Follow the process of whitelisting, the use of applications and processes that runs in your environment by providing a defined list of approved applications and processes. Like a VIP List for your PC, if it’s not on the list, it’s not allowed.
- File Integrity Monitoring—Monitor your IT environment 24x7x365 for any changes to the critical OS, files and processes such as directories, registry keys, and values. It also monitors for any changes to application files, rogue applications running on the host and unusual process and port activity, as well as system incompatibilities.
- Principle of Least Privilege (POLP) Access Policy– It is better for the organization to ensure that the user have the least privilege for their job and also to follow the Zero Trust Model to cut-down trust level dependencies.
- Enable Multi-Factor Authentication Mechanism- Remote connection services to the organization network such as VPN, RDP, SSH should have a strong and unique credential as well as Two-Factor Authentication(2FA) to avoid malicious intrusions.
- Internal and External Security Audit/Penetration Testing- It helps to assess the strength and weaknesses of the IT environment and also to make sure that you are implementing the best practices to defend against the threats.
- Security Awareness Program to Employees – It is necessary to educate the employees about the emerging cyber threats and the way that how a hacker may break into the organization and several Social Engineering attacks and phishing and spam emails. It will protect the organization and its employees from falling as bait to the attacker’s tracks.
- Business Continuity Plan- Drafts a Disaster Recovery Strategy and ensures that everyone knows their roles and what should be done if a compromise happens.
- Strict Patch Management- A report says that 57% of data breaches are happening due to poor patch management. Ensure that all the software runs on the host are latest version with all the necessary security updates and patches installed.
- Endpoint Security Solution – Endpoint Devices(Firewall, IDS/IPS,Router etc.,) are responsible for Protection, Detection and Response of Malicious activities and intrusions happening in a network. Make sure that the Endpoint is installed with Antivirus and Antimalware software to block cyberattacks.
Conclusion
As technology grows every day cyber threats also increases and they will not come to an end. A Cybersecurity Ventures survey states that, “A new organization will fall victim to ransomware every 14 seconds in 2019, and every 11 seconds by 2021”. If you are a business owner irrespective of size, it is hard to concentrate on the security constraints of the organization as they concentrate on their business development. So, Finding and Partnering your business with a Cyber Security Service Provider in the market is the best way to prevent you from cyber attacks and they will help in assessing the organization with an eye of an adversary and would tell your organization’s strength and weaknesses. They will take-care of the business continuity during cyber-crisis by providing a clear disaster recovery strategy, and also educate the employees about the cyber threats across the globe. According to the Cybersecurity Ventures predictions “Cybercrime damages will cost the world $6 trillion annually by 2021,” so it is better to invest in cyber security service than to pay a cyber criminal.
References
- https://www.soscanhelp.com/blog/how-ransomware-has-evolved
- https://kraftbusiness.com/cyber-security/evolution-of-ransomware-2019-brings-30-year-anniversary/
- https://www.ninjarmm.com/blog/must-know-ransomware-statistics-2020/
- https://www.itgovernance.co.uk/blog/the-5-biggest-ransomware-pay-outs-of-all-time


