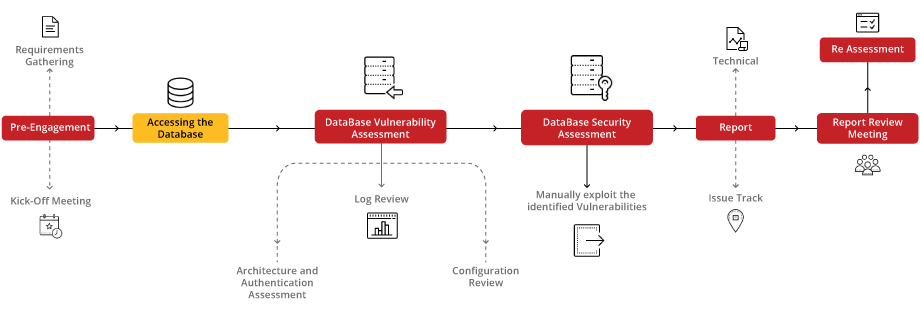
Database Security with Targeted VA/PT Audit Strengthen your database integrity with our focused VA/PT audit, designed to address the unique security challenges of database environments. Our comprehensive approach assesses vulnerabilities and strengthens defenses against potential threats, ensuring your data remains secure and compliant with industry standards.
Our Database VA/PT strategy encompasses a thorough evaluation from start to finish, employing advanced techniques to scrutinize your database for vulnerabilities and misconfigurations. By focusing on in-depth testing and remediation, we safeguard your critical data assets against unauthorized access and breaches, enhancing your overall cybersecurity posture. This targeted process aims to fortify your database's security framework, ensuring resilience in the face of evolving cyber threats.
Cybersecurity starts with proper awareness. Briskinfosec BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download the one-page Database Security Flyer, Database Security Case Study and Threatsploit Adversary Report.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Nowadays the biggest danger that we come across and also something that we are about to face in future is The cyber threat the crime that happens via internet and technology.
Read the blogNull Byte Injection is an exploitation technique which uses URL-encoded null byte characters to the user-supplied data. This injection process can alter the intended logic .
Read the blogSQL injection is an attack when an attacker persuades to “inject” his harmful/malicious SQL code into someone else’s database, and force that database to run his SQL
Read the blogElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.