Our Cyber Forensics Investigation service delves deep into digital systems and data to uncover evidence, identify perpetrators, and reconstruct digital incidents. By employing advanced forensic techniques and methodologies, we aim to provide conclusive findings and support legal proceedings, ensuring justice and accountability in cyberspace.
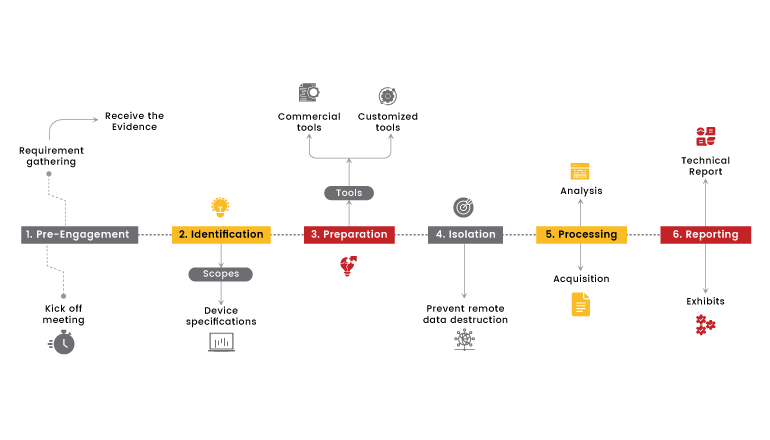
Our approach to Cyber Forensics Investigation begins with the identification of digital assets and evidence preservation to maintain integrity throughout the investigation. We then utilize specialized tools and forensic analysis techniques to extract and analyze data, reconstructing events and uncovering potential threats. Our team provides comprehensive reports and expert testimony to support legal proceedings and guide future security measures.
Cybersecurity starts with proper awareness. Briskinfosec BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download the One-page Cyber forensics flyer, Cyber Forensics Case Study and Threatsploit Adversary Report.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Zero-day vulnerabilities are a major threat to the security of computer systems and networks.These vulnerabilities are unknown to software vendors and their users.
Read the blogThe term Internet of Things"was first used in 1999 to promote a technology called Radio Frequency Identification. IoT didn't become more popular until 2010/2011. By early 2014, it was used by most people. IoT forensics is a type of digital forensics that looks
Read the blogDigital Forensics is the field of forensic science that is concerned with retrieving, storing and analyzing electronic data that can be useful in criminal investigations. This includes information from computers, hard drives, mobile phones
Read the blogElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.