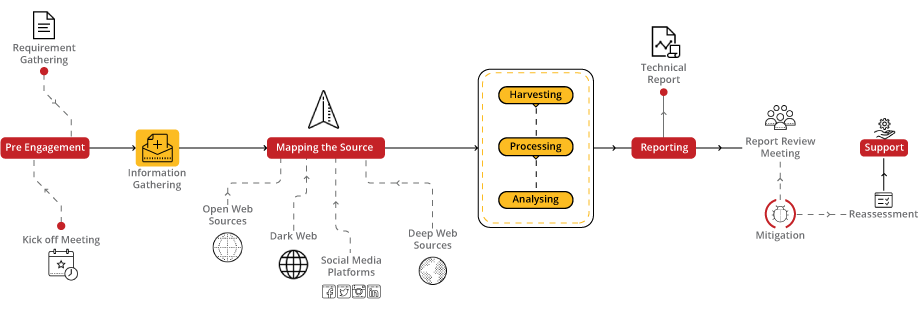
Cyber Threat Intelligence is the proactive process of collecting, analyzing, and interpreting data to comprehend cyber threats and mitigate risks effectively. By understanding the evolving tactics of threat actors, organizations can enhance their security measures and respond swiftly to potential cyber-attacks.
A blend of automated precision and human insight, offering proactive, actionable intelligence to stay ahead of evolving cyber threats.
Cybersecurity starts with proper awareness. Briskinfosec BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download the one-page CTIR flyer, CTIR Case Study and Threatsploit Adversary Report.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Nowadays the biggest danger that we come across and also something that we are about to face in future is The cyber threat the crime that happens via internet and technology.
Read the blogOrganizations face multiple cybersecurity dangers in the digital age, which could compromise confidential information.
Read the blogA type of internet-based computing that provides shared computer processing resources and data to computers as well as other devices are on demand. Cloud is a large server on which different services and datum are stored and one can access it, whenever required.
Read the blogBrowse our selection of handy cybersecurity tools. Arm yourself with the right defenses to safeguard your digital life.
GraphQL is a query language for APIs and a runtime for fulfilling those queries
Read the tool of the dayDomain name permutation engine for detecting homograph phishing attacks
Read the tool of the dayOSRFramework is a GNU AGPLv3+ set of libraries developed by i3visio to perform Open Source Intelligence collection tasks.
Read the tool of the dayElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.