Contents
- Introduction
- What is FTP?
- What are its applications?
- How it works?
- Other Protocols based on FTP
- Vulnerabilities in FTP
- How to defend from those vulnerabilities?
- Conclusion
- How Briskinfosec helps you?
- Curious to read our case studies?
- Last but not the least
- You may be interested on
Introduction:
How well do you know about FTP server?
Well, this blog will describe the possible ways to attack the FTP servers to compromise your files or the internal network of the organization, how the attacker would try to exploit the FTP, and best possible ways to defend the attack.
What is FTP?
FTP is a protocol which is used for transferring files between the systems. FTP stands for File Transfer Protocol, which is defined by RFC 959 (Request For Comments). This protocol uses port 20 and 21 by default. It is faster in transferring files between the computers, because it is created for that purpose. Also, FTP would automatically resume the download when file transfer is interrupted.
What are its applications?
- With this, it would be helpful for a developer to upload his site to the remote server.
- Used for hosting larger files on a centralized location.
- Used in transferring larger files between the two systems.
How it works?
FTP communication takes place using two ports. One is port 20, used for data transfer while the other is port 21, used for command and control. For transferring files, FTP client and FTP server is required, because FTP works based on the client-server architecture. Apart from this, FTP uses two modes of connections, one is active connection while the other one is passive connection.
The difference between the active and passive connection is based on who initiates the connection. After the handshake, if the server initiates the data transfer from random higher port to the server’s FTP data transfer port, (i.e 20) then the mode of connection is said to be an active FTP mode.
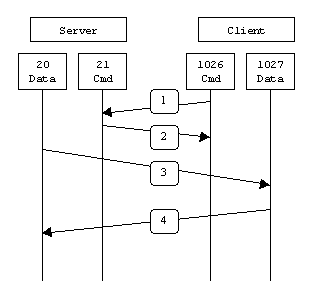
If the client initiates the data transfer from a random higher port to the server’s random higher port, then the connection is said to be a passive one.
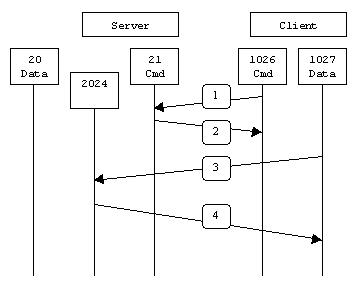
As in passive mode of connection, client always makes an active attempt of connection, so it would work better for clients protected by firewalls.
Other Protocols based on FTP
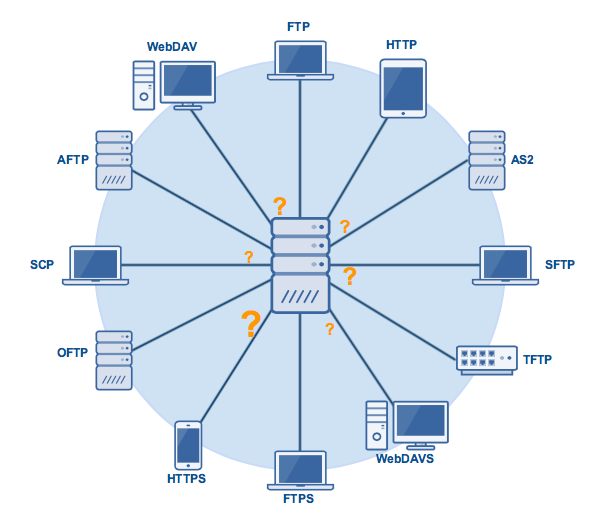
FTPS (FTP over SSL): This protocol uses Transport Layer Security (TLS) to make sure the communication is encrypted. Apart from this, everything is similar to FTP. This has two types of transfer methods. The first one is FTPS (implicit) which allows the client to connect securely via TCP port 990, but no negotiation is allowed. The other method is FTPS (Explicit) which negotiates through encrypted communication, via TCP port 21.
SFTP (SSH File Transfer Protocol): SFTP is bit similar to FTP but it uses SSH to make the transfer secure by encrypting, and it shares the files via TCP port 22, becoming NAT (Network Address Translator) friendly. Since it works on a different port, it is difficult for an ordinary client to connect.
SCP (Secure Copy): This protocol is used to transfer files between the computers securely. It works based on the SSH protocol where it is encrypted and authenticated. It only copies files from local host to remote host via TCP port 22, because it is the combination of RCP (Remote Copy Protocol) and SSH (Secure Shell).
TFTP (Trivial File Transfer Protocol): It is a simple high-level protocol for transferring data between the servers. These are mostly used to boot diskless workstations, X-terminals and routers using UDP. It’s mostly used in places where the security features like authentication and directory visibility aren’t required. File transfer takes via UDP on port 69. Some of the applications are as follows:
- Transferring files
- Remote booting of servers without hard drives
- Upgrading codes
- Backing up network and router configuration
- WebDAV (Web Distributed Authoring and Versioning)
- AS2 (Applicability Statement)
- OFTP (Odette File Transfer Protocol)
- AFTP (Accelerated File Transfer Protocol)
Vulnerabilities in FTP
1. Brute Force attack: When FTP servers are exposed online, it gives a chance for the intruders to create a dictionary file based on the OSINT intelligence. So, it would give a way for an attacker to start a brute force attack against the server to enumerate the credentials. Username Enumeration is also similar to the brute force attack, but here we would try to enumerate the user names of the FTP server.
How to defend from those vulnerabilities?
Some of the possible ways to overcome this vulnerability is to follow the statements below:
- Lock down the accounts based on continuous login failures or pausing the authentication process after multiple failures.
- Other remedial actions are to blacklist the IP which has multiple failures and whitelist the IP address, in case of higher sensitive contents.
2. FTP Bounce: FTP bounce is a type of exploit where attacker first connects to the FTP server and then uses the PORT command to connect to the other servers.
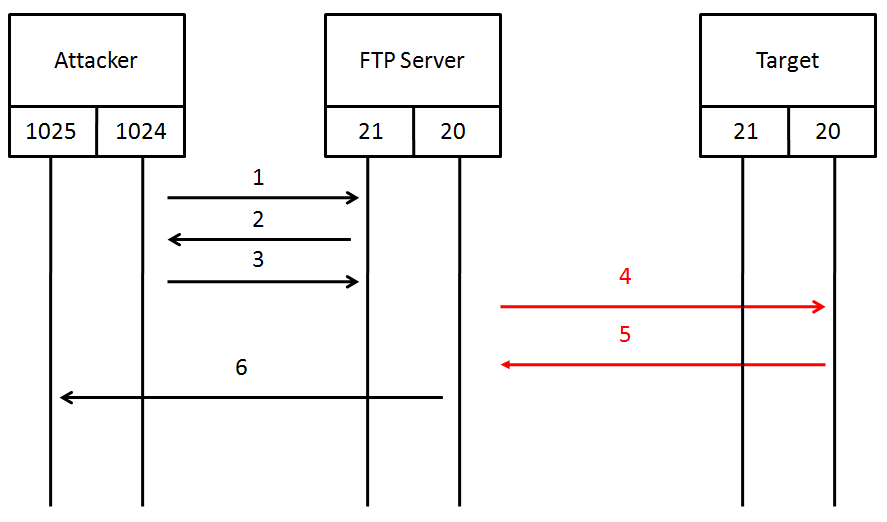
How to fix this?
Any PORT request destined for IP address other than the IP address of the authorized FTP clients should be strictly verified using the firewall. The firewall should be configured to block or properly validate the PORT request or change the configuration of the FTP server, so that it cannot be misused.
3. Capturing FTP traffic: By Default, the FTP will run on un-encrypted communication which would transfer the credentials of the FTP server in plain text where users try to login into the FTP server.
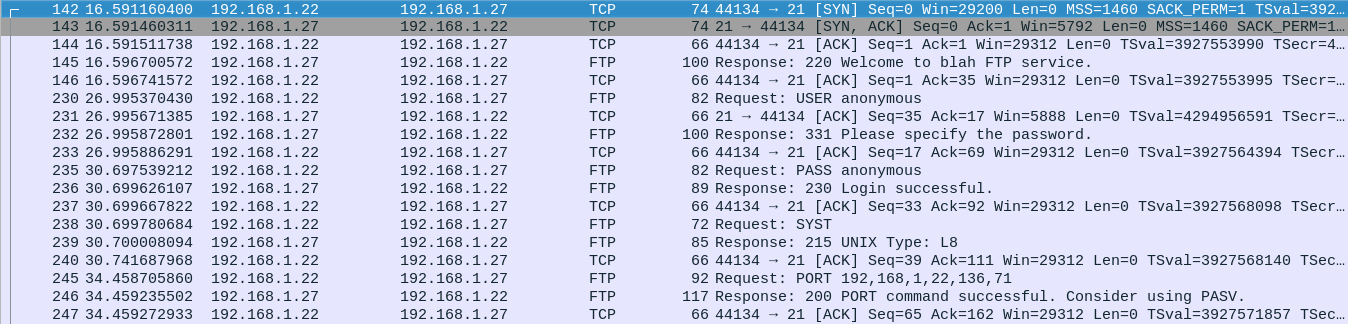
How to fix this?
Implement SSL on the FTP to make the traffic secure. Another way is to switch to other FTP based protocols like SFTP or FTPS. These protocols provide secure transmission by default because it is created for this purpose.
4. Anonymous Login: Anonymous login is a feature of the FTP service, which allows the users to connect to FTP, without valid or official credentials. Instead, the user will login using a string called “anonymous”, as user name and password.
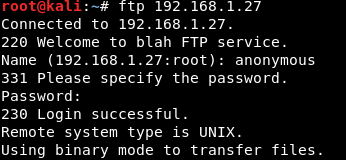
How to Fix this?
Anonymous login is enabled in most of the FTP servers by default. Anonymous login with the directory access was the most critical security issue. The reason is, anyone can login to the FTP server and can view the files available. So, disabling the anonymous login would restrict the unauthorized user to connect to the server. Further, the directory access must be limited, so that even if unauthorized user gets connected to the FTP server, he/she cannot view the confidential files.
5. Banner Grabbing: Banner grabbing is the process of identifying the service version and service name through the banner of the FTP service. By exposing these information’s via banner, attacker may search for the related exploits for compromising the service.
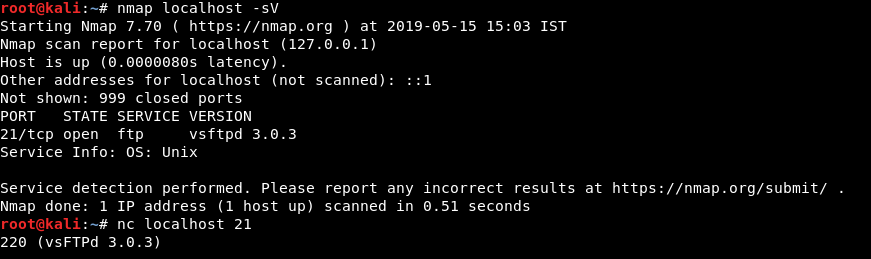
How to fix this?
For hardening the FTP server, first step is to hide the server banner, because it would disclose the version of the server so that an attacker can look for the exploits related to that or he/she can download the same version of FTP to analyze the configuration, finding other ways to exploit it.
Conclusion:
Never ever assume nor believe that your FTP server is secure. Each and every minute, from some part in this globe, there’s an attempt to seize/compromise your FTP server. Apart from all these basic measures cited above, to secure your FTP server, a complete and a proper security assessment from a competent cybersecurity company is mandatory.
How Briskinfosec helps you?
As the name suggests, FTP is primarily used for File Transferring. Just imagine a scenario during file transmission, the file which was supposed to be received by the intended client, gets captured by a middle-man (MITM) and gets corrupted. What will you do and what must be done?
To prevent so, Briskinfosec provides complete network security assessment on your entire networks (including FTP’s) and identifies all the vulnerabilities. We eliminate the identified vulnerabilities, secure your Network loopholes, and strengthen your security environment, to the best. Apropos of that, we also provide practical awareness on such issues.
Curious to read our case studies?
Success speaks louder than the attempts. Similarly, our case studies will speak about our successful security strategies executed during security assessments in a bid to eliminate various cyber threats that were existing stealthily in our client applications. Read out our case studies to know the way we won the battle against cyber threats.
Last but not the least:
Many times, silence speaks louder than words. Accomplishments speak louder than persuasions. Similarly, our Threatsploit Adversary report speaks louder and shines brighter when compared with the humongous time taken to know about cyberattacks and its impacts on various search engines and websites. This report of us just takes a single click to be read. It is exclusively prepared with the noble intention of cautioning people about the fate of this ‘ever-growing and never-stopping’ cyber threats/breaches, the organizations affected by these, the assets lost, and much more. Most importantly, we also provide the best possible measures to stay protected from those. Just read it and you’ll never regret it!



