Introduction
Imagine you're the owner of a SaaS product—a cloud-based software solution that serves numerous customers worldwide.
Your product is designed to handle sensitive customer data, ranging from personal information to financial records. Security is a top priority for you because you understand the critical importance of safeguarding this valuable data.
Conducting regular vulnerability assessments is like performing a health checkup for your product. It allows you to identify any security weaknesses or vulnerabilities that might be lurking within your software, infrastructure, or configurations.
By proactively discovering these vulnerabilities, you can act to address them before they are exploited by malicious actors.
But it's not just about compliance or meeting industry regulations—although that's undoubtedly essential. It's about something more profound. It's about customer trust.
You understand that security breaches can have devastating consequences, leading to a loss of customer trust and severe reputational damage. You value your customers and their trust in your product, and you want to go the extra mile to protect their data.
By prioritizing vulnerability assessments and penetration testing, you can demonstrate to your customers that you take their security seriously. It shows that you're committed to ensuring their data remains confidential and inaccessible to unauthorized individuals. When customers see your dedication to security, they develop confidence in your product and trust you with their valuable information.
Furthermore, vulnerability assessments and penetration testing enable you to identify and mitigate risks proactively. By simulating real-world attack scenarios, you can discover vulnerabilities that could potentially be exploited.
Armed with this knowledge, you can implement the necessary security controls and fortify your product against future threats. You're no longer playing catch-up with attackers; you're staying one step ahead.
How does it help your business?
Vulnerability Assessment and Penetration Testing (VAPT) is an effective way to identify and address any vulnerabilities in your system before they can be exploited by hackers.
It helps SaaS product owners proactively identify and address security vulnerabilities, protect customer data, meet compliance requirements, mitigate threats, and mitigate risks associated with third-party integrations.
Benefits of doing VAPT
SaaS product owners need vulnerability assessments and penetration testing for several important reasons:
- It helps uncover weaknesses and vulnerabilities within the SaaS product's infrastructure, applications, and systems.
- SaaS product owners can mitigate the risk of data breaches and theft.
- By conducting regular VAPT, SaaS product owners can identify security gaps and align their systems with the necessary compliance standards, such as GDPR, HIPAA, or ISO 27001.
- Customers value trust and reliability when choosing a service provider, and a breach can erode that trust.
- Security vulnerabilities can be exploited to disrupt SaaS services or cause system downtime.
- Regular VAPT allows product owners to stay informed about the latest threats and attack vectors.
- SaaS products often rely on third-party integrations, APIs, or libraries, which can introduce vulnerabilities that affect the overall security of the product.
Product owners can develop flexible and trusted products that fulfill the requirements of customers and regulatory frameworks through security testing.
What is VA&PT?
SaaS Vulnerability Assessment and Penetration Testing is a comprehensive assessment of all SaaS business components to identify & address any hidden security flaws.
Additionally, it assists SaaS owners in reviewing the current security of their product, closing any security holes, and identifying opportunities for development while there is still time.
SaaS vulnerability assessments are carried out to review the SaaS solution's security posture and find any vulnerabilities that might be exploited by bad actors.
Stages of SaaS VA&PT:
- Scoping: Determine the scope of the assessment.
- Gather information about the SaaS application.
- identifying vulnerabilities within the SaaS application. This may involve both automated scanning tools and manual analysis.
- Vulnerability Analysis: Evaluate the identified vulnerabilities to determine their severity and potential impact on the security of the SaaS solution.
- Prioritize the vulnerabilities based on their severity and the potential risks. Provide recommendations and actionable steps to mitigate or remediate other security measures.
- The finalized report will be sent to the SaaS Provider, and additional support will be provided to mitigate the vulnerabilities.
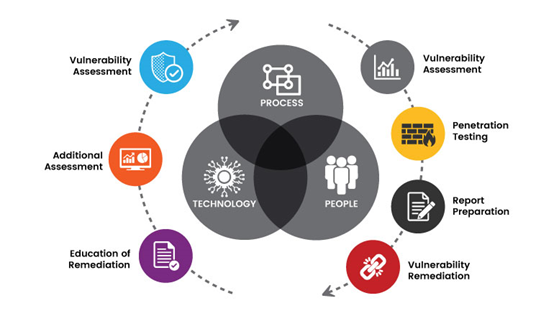
Vulnerability assessments focus on identifying weaknesses, while penetration testing goes a step further by attempting to exploit those vulnerabilities to simulate real-world attacks. Organizations often combine both approaches to enhance the security of their SaaS applications.
Our Service
BriskInfosec offers plenty of services to organisations to help them protect their SaaS applications from cybersecurity threats and attacks.
Conclusion
In the end, prioritizing vulnerability assessments and penetration testing is not just about ticking boxes or satisfying compliance requirements. It's about a commitment to protecting your customers, maintaining their trust, and providing a secure environment for their data. It's about being proactive, resilient, and continuously striving for excellence in security. By investing in these measures, you're not only protecting your customers but also securing the future of your SaaS product in a rapidly evolving digital landscape.


