Sparta is a Python based GUI application. It is a network infrastructure pentesting tool which helps the pen-testers in performing scanning and enumeration phase. It saves time for every security professionals by having a tool point and displays all the output in a convenient way.
Contents
- Features
- Requirements
- Sparta tool
- Host scan
- Nmap scan on Sparta
- Screenshot
- Conclusion
- How Briskinfosec helps you
- Curious to read our case studies
- Last but not the least
- You may be interested on
Features:
- Can run Nmap from Sparta and can even import Nmap XML output.
- Gets the results quickly as it is automated.
- It has also various options like Netcat, Telnet and Dirbuster which does the scanning completely.
- Brute Force option is one of the inbuilt feature available in Sparta through which we can crack for every file (or) folder password.
- We can scan many hosts at the same time.
- Defines automated tasks for services (e.g runs Nikto on every HTTP service and SSL scan on every SSL service).
- Default credentials checks for most common services and it can also configure to run automatically.
- Website screen shot taker is also available here, saving time rather than downloading tools for such purposes.
Requirements:
Kali Linux has lots of in-built tools to perform various operations
Here, Sparta can be installed on Debian-based systems by following the below guidelines:
- First, install Python elixir by the following commands:
root@dd: apt-get install python-elixir
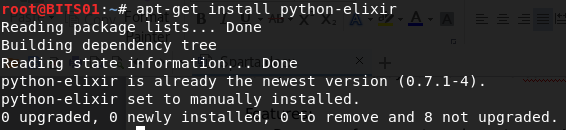
-
Install python-elixir along with Python-qt4:
root@dd: apt-get install python-elixir python-qt4
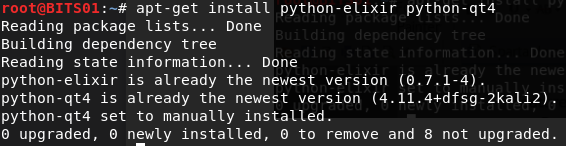
- Now, install Sparta tool in kali Linux:
root@dd: apt-get install Sparta
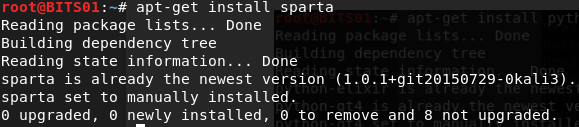
- Now, you have the Sparta tool and is ready for usage:
root@dd: Sparta
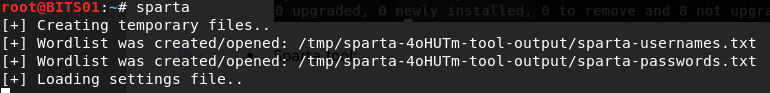
The above commands are used to configure and install the Sparta tool in Kali Linux and screenshots of each Sparta installation processes are attached, for your reference and to understand with better clarity.
Sparta Tool:
Here in Sparta tool, you can see the various options listed for performing scanning and other functions. Most significantly, separate options are available for every service, which makes easier for you to look on every action that takes place as well in understanding their nuances.
Host Scan
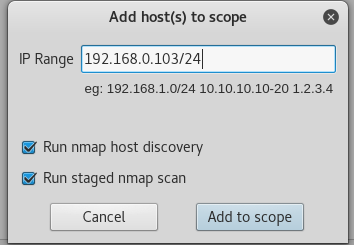
Here, we add for a specific host to perform scanning and they can be selected from the options cited below:
File --> Add to Scope
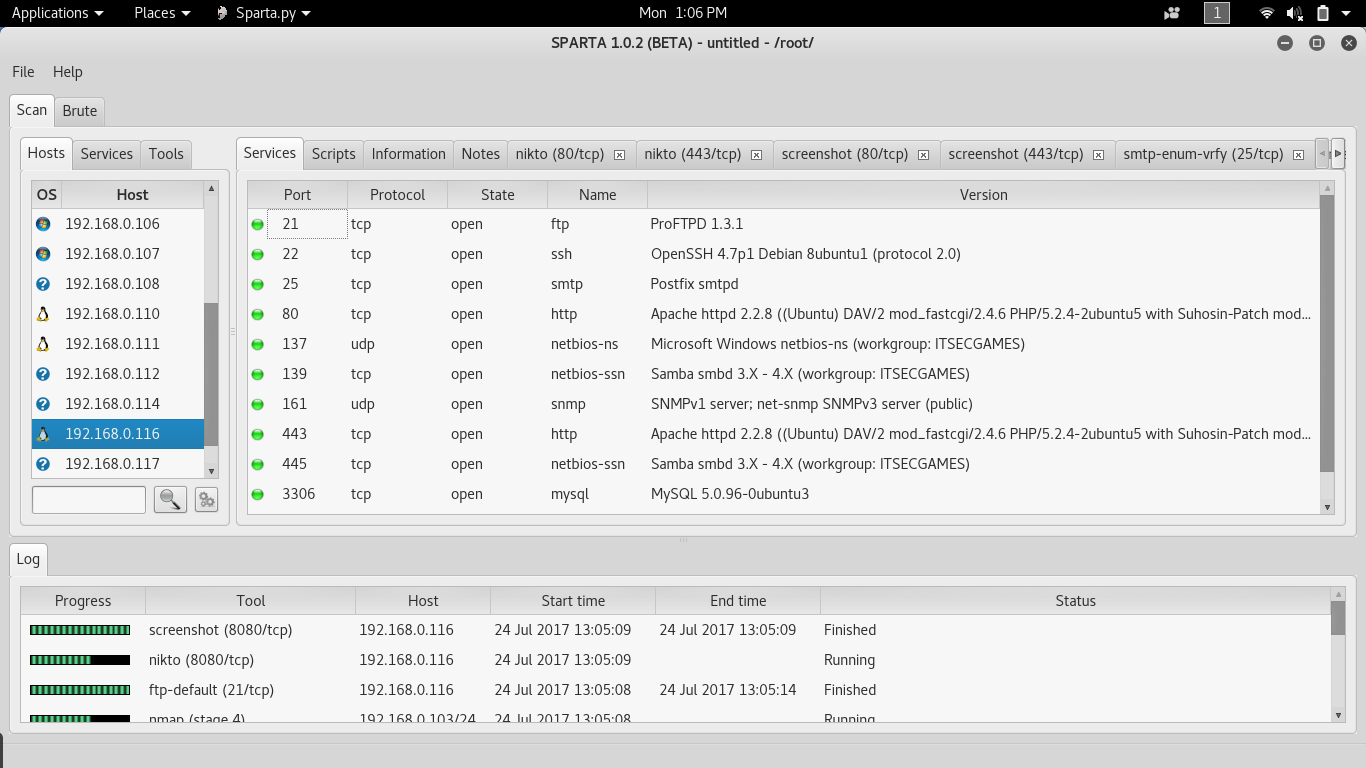
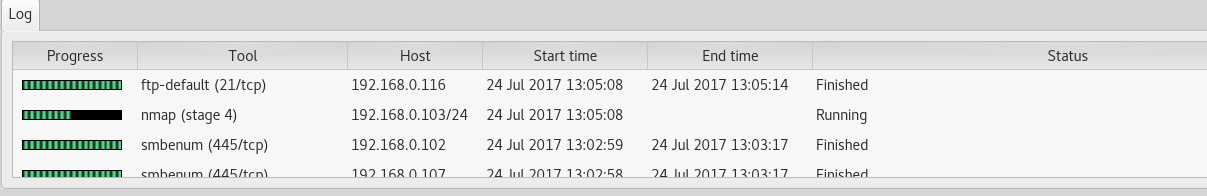
Here, I had scanned for a host on 192.168.0.103/24 and it scans for every host connected to this particular host. Now you can see the various host lists connected to this host at left corner, at the top, and you can see the services as follows.
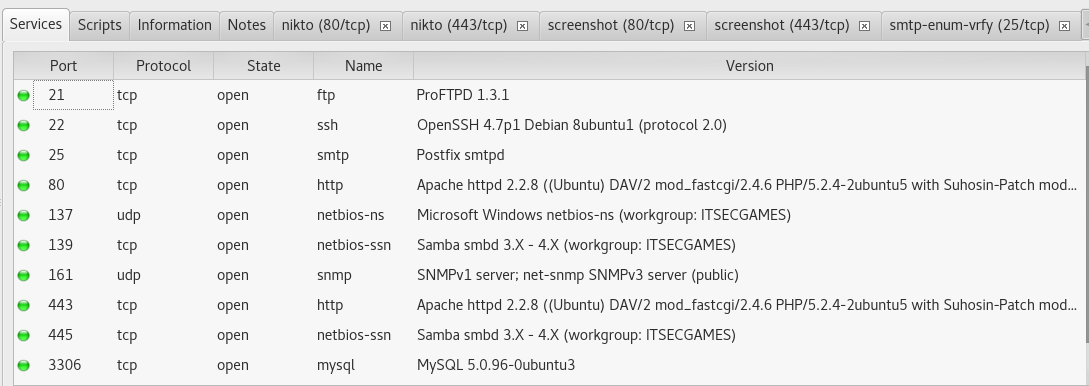
The various services that has taken place on each host has been listed in the above screenshot.
Nmap Scan on Sparta:
Nmap scan takes place over here and it scans for every port inside a host which checks for the vulnerabilities and if it finds any suspicious files, it kills them. This is also a major advantage in Sparta.
Brute Force
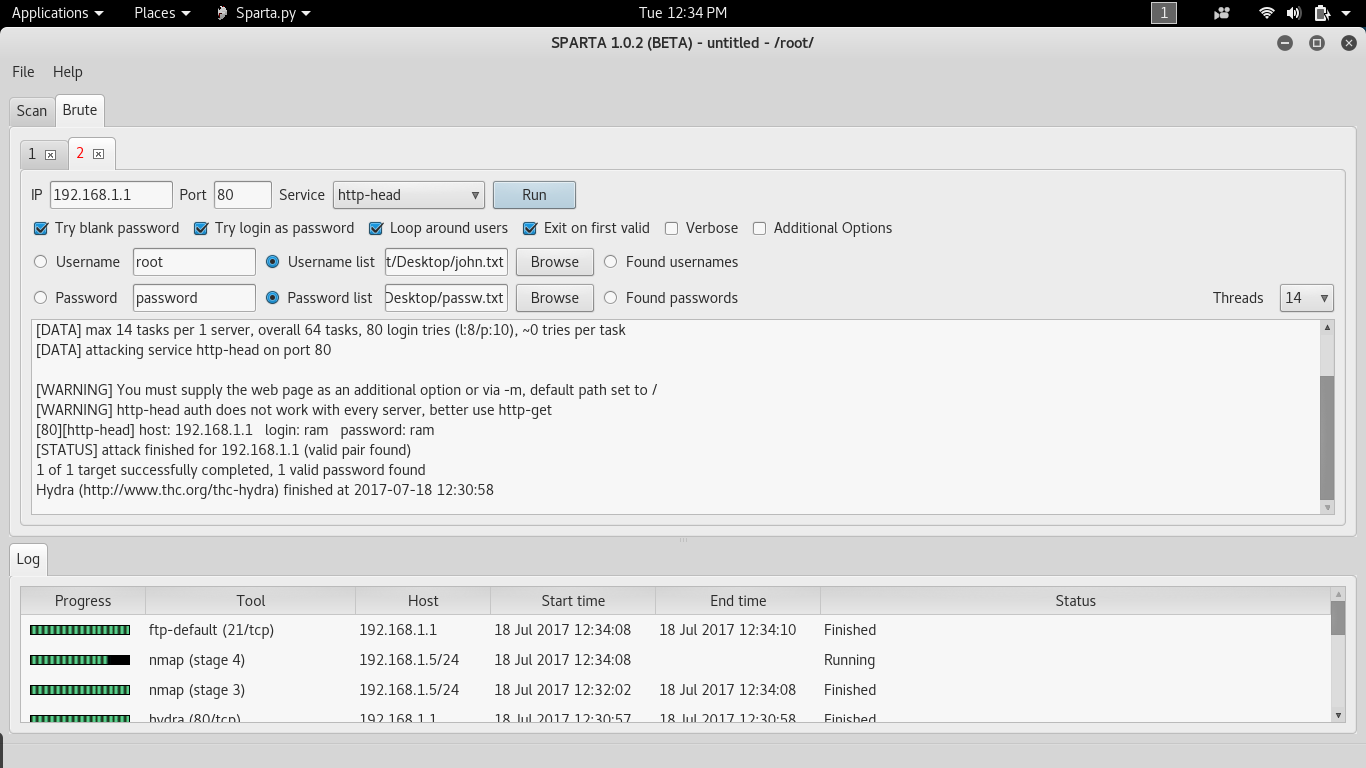
I had performed brute force on a particular host at port 80. Here we should select the username list and password list from your system, and later by running the process you can fetch the required username and password using the Hydra tool.
Screenshot:

This is the screenshot of the person who’s connected to the host and the screenshot is used to provide us the information for confirming whether the ports are opened on a required host or not.
Thus, there are various techniques and functions involved in scanning and enumerating a particular host. We can also perform scanning and enumeration process using tools like telnet, netcat and dirbuster using this tool, called Sparta.
The alternate output that appears on Kali-Linux terminal is as follows.
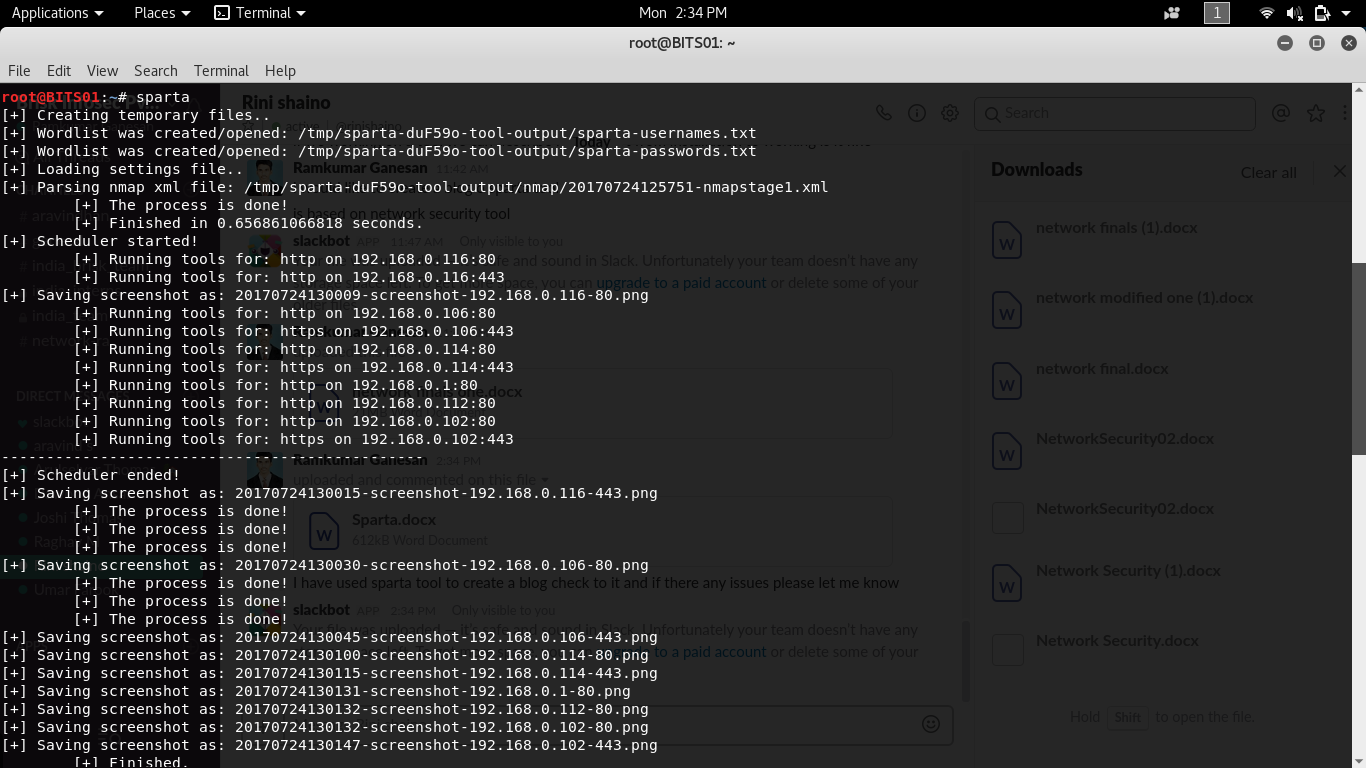
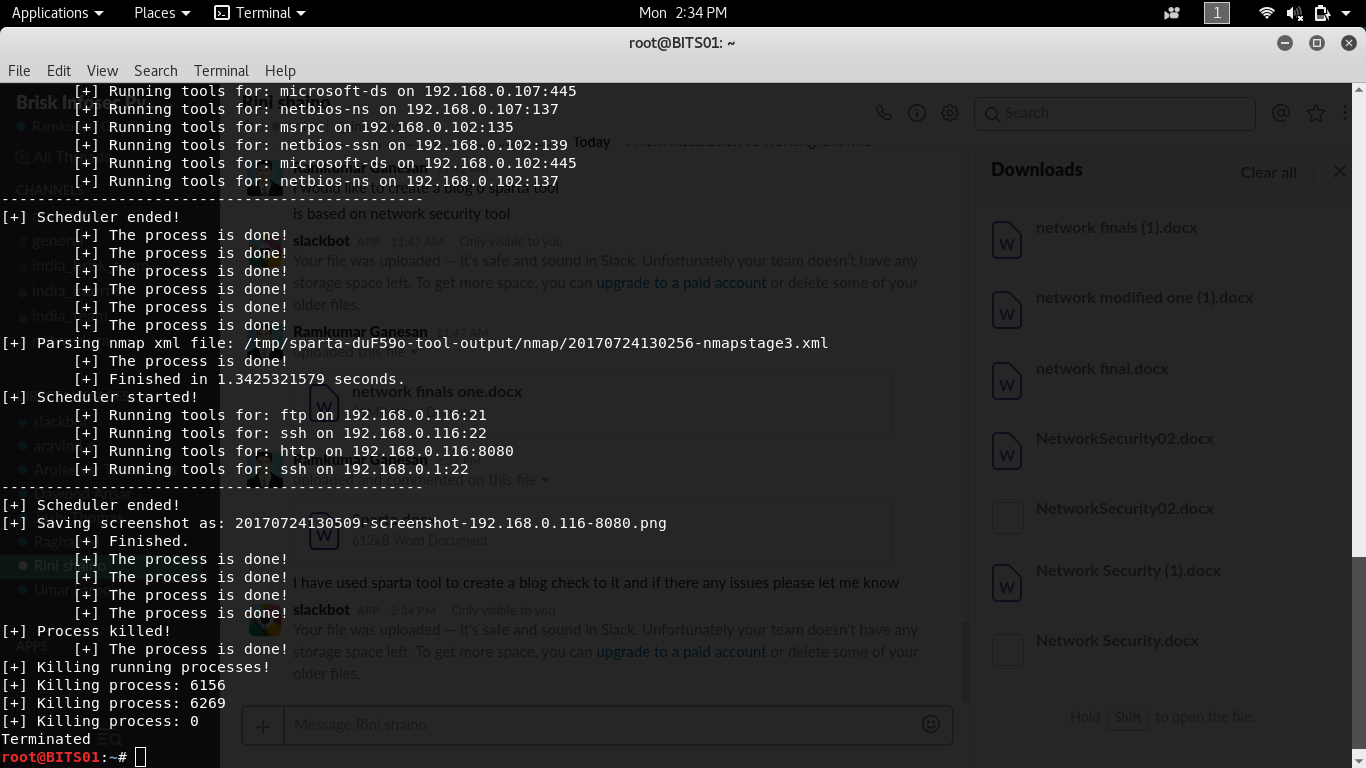
The above screenshot is the final result fetched on Kali Linux terminal, using Sparta tool.
CONCLUSION:-
Sparta is one among the best scanning and enumeration tools available in the security market. For those who are looking for single scanning and enumeration, Sparta is the perfect tool for reconnaissance and password cracking.
How Briskinfosec helps you:
Sparta is a good automated scanner. But, we are living in 21st century where cyber breaches strike organizations easily, in-spite the company’s data being scanned with both automated and manual scanners. Now, do you believe just a scan with Sparta tool alone, ensures your data safety to the fullest? The truthful answer is No. Sparta serves as a helping tool in doing scanning but not as the complete saving grace against cyber threats.
CYBER AWARENESS ON AUTOMATED TOOLS:

Briskinfosec provides complete security assessment and secures the entire attack surfaces. Apart from traditional scanners, we also use contemporary security tools which increases the efficiency of testing. Further, we have an ANSI (Advanced Nmap Scripting Engine) tool which is developed by the security professionals of Briskinfosec. Apart from this, we have our NCDRC-MAST framework, which was officially released by (National Cyber Defense and Research Centre). Through these, we emerge as someone above many cybersecurity firms and not as someone among other cybersecurity firms.
Curious to read our Case studies:
Our Case studies showcases you our honest approach in performing security assessments and in eradicating vulnerabilities in many of our client’s applications. Security assessments are done to our esteemed client’s based on their requirements. To know the manner we do, check out our case studies.
Last but not the least:
Our clients once were randomly checking internet about a notion fulfilment. They looked worried and restless. This truly disturbed us as our client’s happiness is always our best desire and first preference. We immediately asked them, for what they were searching. Seeming exhausted, they replied that they wanted to know about the recent cyberattacks and companies affected because of them. They also said that the task is time-consuming and patience-defying. Understanding their need, we politely showcased our Threatsploit Adversary Report. It’s a single report which Briskinfosec prepares by collecting various cyber breaches and its impacts on companies, from various parts of the earth on a monthly basis. Seeing this, our clients were filled with joy, as they got their needs filled in one report. What else? Check our Threatsploit report. Even you’ll be satisfied, for sure.


