Introduction
Imagine a bank with an API that allows you to check your account balance and make transactions from your favorite budgeting app. Imagine what could happen if that API were compromised. Your financial data could be exposed, leading to unauthorized transactions and a potential breach of sensitive information.
In a world where cyberattacks can happen at any moment, putting your company's reputation and finances at risk, Unfortunately, this is not just a nightmare vision of the future; it is a reality we face daily.
That's why API security assessment is more important than ever. By proactively identifying and addressing potential vulnerabilities, we can protect ourselves from cyberattacks and safeguard our sensitive data.
What is API Security Assessment?
API security assessment is the process of evaluating the security of an application programming interface. This involves identifying vulnerabilities and potential threats that could be exploited by attackers. By conducting regular security assessments, organizations can ensure that their APIs are secure and protected against cyberattacks.
The best type of API security assessment for an organization will depend on the specific needs of the organization.
If you are responsible for the security of APIs, then you should consider conducting regular API security assessments. This is an important part of protecting your organization from attack and ensuring the security of your APIs.
Here are some of the things to consider when conducting an API security assessment:
- Scope of the assessment: What APIs will be assessed?
- Methodology: What tools and techniques will be used?
- Resources: Who will conduct the assessment?
- Schedule: When will the assessment be conducted?
- Budget: How much will the assessment cost?
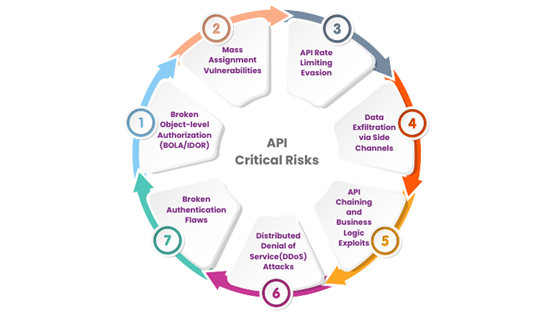
Common API security risks
API security risks are a serious concern for anyone dealing with sensitive data. Injection attacks, where malicious code is injected into an application’s input fields, can lead to data breaches and other security issues. Broken authentication and authorization can allow unauthorized access to sensitive data, while improper error handling can reveal sensitive information to attackers.
Twitter API leak (2021) is one of the most significant API breaches. Hackers took advantage of a flaw in the Twitter API to gain access to over 5.4 million Twitter users. Hackers could exploit the flaw by submitting email addresses or phone numbers to the Twitter API in order to retrieve the linked Twitter account.
The top 10 API vulnerabilities, according to OWASP, a nonprofit organization committed to improving the security of software and web applications, are
- Broken Object-Level Authorization
- Broken Authentication
- Broken Object Property Level Authorization
- Unrestricted resource consumption
- Broken Function Level Authorization
- Unrestricted access to sensitive business flows
- Server-Side Request Forgery
- Security Misconfiguration
- Improper inventory management
- Unsafe consumption of APIs
To mitigate these risks, it is important to conduct regular security assessments of your APIs. By identifying vulnerabilities before they can be exploited, you can prevent potentially harmful security incidents.
Benefits of Conducting API Security Assessments
- It can help to identify and mitigate vulnerabilities in APIs.
- It can help improve the security posture of APIs.
- It can help reduce the risk of data breaches and security incidents.
- It can help to protect the confidentiality, integrity, and availability of APIs.
- It can help to comply with industry regulations and standards.
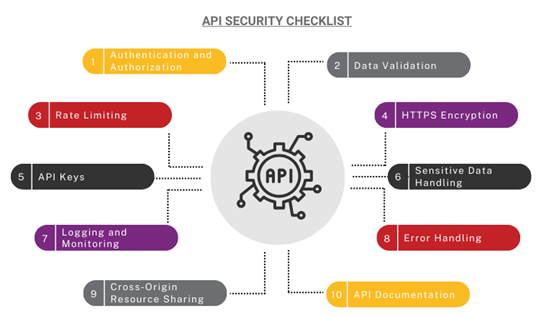
API Security Assessment Best Practices
Regular testing is essential for maintaining API security. It is important to test your APIs frequently to identify any vulnerabilities that may have been introduced since the last assessment.
This process can be done manually or with automated tools. Automated tools can save time and effort, but they should not replace manual testing entirely.
Using multiple tools is also important for a comprehensive API security assessment. Each tool has its own strengths and weaknesses, so it's best to use a combination of tools to ensure that all potential vulnerabilities are identified.
It is important to choose a qualified and experienced team to conduct your API security assessment. They should have the knowledge and expertise to identify and mitigate vulnerabilities in APIs
Here are some additional tips for conducting API security assessments:
- Use a variety of tools and techniques to get a comprehensive view of the security posture of your APIs.
- Involve developers in the assessment process to get their insights into the APIs.
- Encrypt and validate API requests and responses.
- Continuously monitor your APIs for vulnerabilities and misconfigurations.
- Keep up-to-date with the latest API security threats and trends.
By following these guidelines, you can assist to ensure that your APIs are secure and that your data is safe.
Conclusion
In conclusion, API security assessment is a crucial step in protecting against cyberattacks. By identifying and mitigating common API security risks such as injection attacks, broken authentication and authorization, and improper error handling, organizations can significantly reduce their risk of a breach.
It is important to regularly test APIs using multiple tools and involve stakeholders in the process to ensure comprehensive coverage.
By taking these steps, organizations can improve their own API security practices and reduce their risk of a cyberattack.



