Ransomware has emerged as one of the most dangerous and persistent threats in the cybersecurity landscape. Unlike traditional malware, ransomware is constantly evolving, making it an increasingly challenging and devastating weapon in the hands of hackers. It has been likened to a "nuclear bomb" of the digital world, capable of crippling organizations, disrupting critical services, and even forcing some companies out of business.
Debunking Ransomware Myths
Myth 1: Ransomware Attacks are Immediately Obvious
Ransomware attacks are not always immediately evident. Hackers often infiltrate networks weeks or months before launching the encryption attack, quietly exfiltrating data and establishing a foothold.
Myth 2: Ransomware Only Affects Windows Systems
Modern ransomware targets a wide range of operating systems, including macOS, Linux, and virtualization platforms. Attackers leverage vulnerabilities in cloud environments and IoT devices, making ransomware a platform-agnostic threat.
Myth 3: Ransomware is Just About Getting Ransom Payments
Financial gain is a primary motive behind ransomware attacks, but it's not the only one. Ransomware can also be aimed at disrupting operations, stealing information, or harming the reputation of the targeted entity. The consequences of an attack can be far-reaching, affecting not just the financial bottom line but also the trust and confidence of stakeholders.
Ransomware as a Service (RaaS)
The concept of Ransomware as a Service (RaaS) has revolutionized the cybercrime landscape. RaaS allows even those with limited technical knowledge to launch ransomware attacks by renting ransomware tools and services from skilled developers. This business model has led to the proliferation of ransomware attacks, as it lowers the barrier to entry for aspiring cybercriminals.
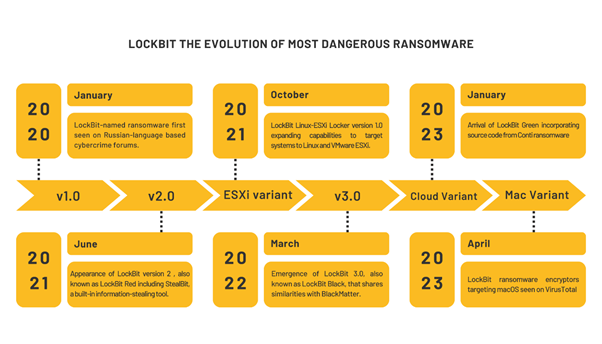
LockBit: The Evolution of a Dangerous Ransomware
LockBit has emerged as one of the most dangerous ransomware variants, evolving over the years to become more sophisticated and potent.
- January 2020: LockBit first appeared on Russian-language cybercrime forums.
- October 2020: LockBit Linux-ESXi Locker version 1.0 was released, expanding its capabilities to target Linux and VMware ESXi systems.
- June 2021: LockBit 2.0, also known as LockBit Red, was introduced, featuring StealBit, a built-in information-stealing tool.
- March 2022: LockBit 3.0, also known as LockBit Black, emerged, sharing similarities with BlackMatter.
- April 2023: LockBit ransomware encryptors targeting macOS were detected on VirusTotal.
Notably, in September 2022, non-LockBit affiliates were able to use LockBit 3.0 after its builder was leaked, further spreading its reach and impact.
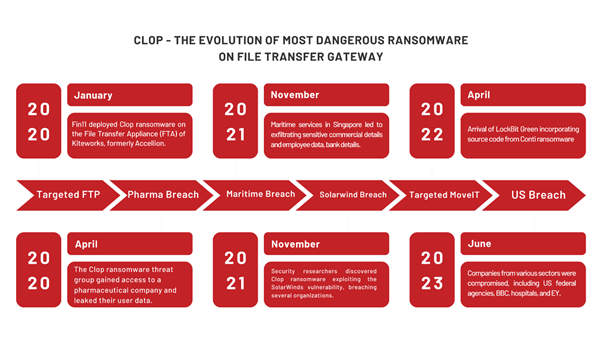
Clop: Targeting File Transfer Gateways
Another notorious ransomware variant is Clop, known for its high-profile attacks on file transfer gateways.
- January 2020: Clop ransomware was deployed on the File Transfer Appliance (FTA) of Kiteworks, formerly Accellion, by the Fin11 group.
- April 2020: The Clop ransomware group gained access to a pharmaceutical company and leaked their user data.
- November 2020: Security researchers discovered Clop exploiting the SolarWinds vulnerability, breaching several organizations.
- June 2023: Companies from various sectors, including US federal agencies, BBC, hospitals, and EY, were compromised by Clop.
Clop has been particularly notorious for exploiting zero-day vulnerabilities in key platforms like GoAnywhere MFT, PaperCut, MOVEit, and SysAid, showcasing its ability to adapt and target critical infrastructure.
Lifecycle of a Ransomware Incident
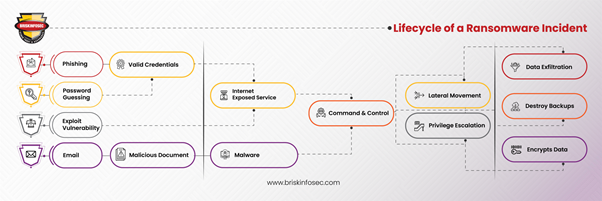
Understanding the lifecycle of a ransomware incident is crucial for effective defense and mitigation. Here’s a brief overview of the typical stages involved:
- Initial Compromise: Attackers gain access to the target system through phishing emails, exploiting vulnerabilities, or other means.
- Establishing Foothold: Once inside, attackers establish a foothold by deploying additional malware or tools to maintain access.
- Escalation and Lateral Movement: Attackers escalate privileges and move laterally across the network to identify valuable assets.
- Data Exfiltration: Sensitive data is exfiltrated from the network, often to be used as leverage or sold on the dark web.
- Encryption: Files and systems are encrypted, rendering them inaccessible to the victim.
- Ransom Demand: A ransom demand is made, often with threats of data leaks or extended downtime if payment is not made.
- Extortion and Follow-up Attacks: Even after a ransom is paid, attackers may extort additional payments or leave backdoors for future attacks.
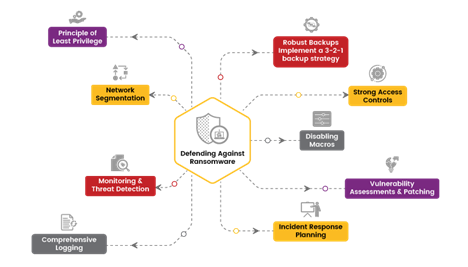
Defending Against Ransomware
Effective ransomware defense requires a multilayered approach combining technical controls, organizational policies, and user awareness. Key measures include:
- Robust Backups - Implement a 3-2-1 backup strategy: keep three copies of data on two different media, with one copy stored offsite. Regularly test backups to ensure they can be restored quickly.
- Strong Access Controls: Use multi-factor authentication (MFA), enforce the principle of least privilege, and regularly review and update access permissions.
- Disabling Macros: Disable macros by default and allow only digitally signed macros from trusted sources. Educate employees on the risks of enabling macros.
- Vulnerability Assessments and Patching: Conduct regular vulnerability assessments and timely patching to reduce the attack surface. Prioritize patching critical systems and applications.
- Incident Response Planning: Develop a well-defined incident response plan outlining steps for containment, eradication, recovery, and communication. Regular drills and tabletop exercises ensure the team is prepared to act swiftly.
- Comprehensive Logging: Capture detailed records of all activities within the network, including user logins, file accesses, and system changes. Store logs in a secure, centralized location.
- Monitoring and Threat Detection: Use automated tools and techniques to analyze log data and identify anomalies. Security Information and Event Management (SIEM) systems can provide real-time visibility into network activities.
- Network Segmentation: Divide the network into smaller, isolated segments to limit the spread of ransomware. Implement strict access controls and use firewalls and intrusion detection systems.
Principle of Least Privilege: Grant users and systems only the minimum level of access necessary. Regularly review and update access permissions.
Conclusion
Ransomware remains a formidable threat in the cybersecurity landscape, constantly evolving and adapting to exploit new vulnerabilities and targets. Understanding the anatomy of ransomware, dispelling common myths, and adopting a comprehensive defense strategy are critical steps in mitigating the risks associated with ransomware attacks. Businesses must remain vigilant, continuously updating their security measures and educating their employees to stay ahead of this ever-present danger.
For expert assistance in defending against ransomware and other cyber threats, Briskinfosec offers comprehensive cybersecurity solutions tailored to your needs. Feel free to reach out to us. Stay safe and secure in the digital world.

