Introduction:
Secure Code Review service is the process that comes into the development phase. It is used to detect all types of inconsistencies and flaws in various areas of authentication, authorization, security configuration, session management, logging, data validation, error handling, and encryption. It also states about the application logic and business codes. Reviews done by code reviewers should be done in both manual and automated ways and they must be dexterous in the language of application they’re testing in secure code practices, and also must be well acquainted with the various incumbent security controls.
Contents
- Types of Code Review
- Secure coding best practices
- Software Technologies and Methodologies
- Conclusion
- How Briskinfosec helps you
- Curious to read our case study?
- Last but not the least
- You may be interested on
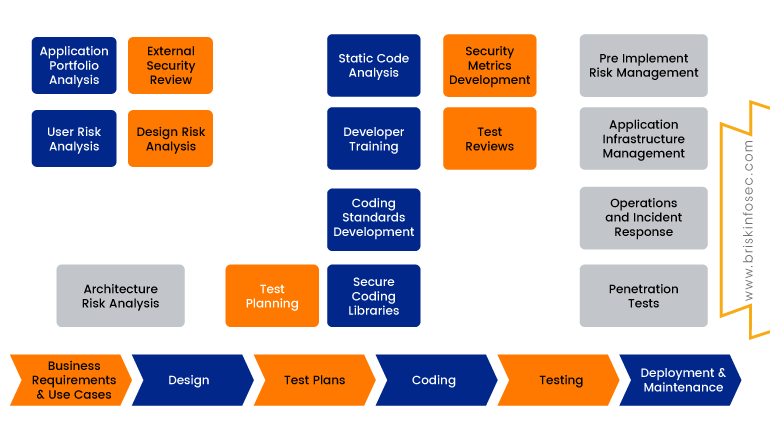
The above pictorial representation depicts the overall architecture of SSDLC (Secure Software Development Life Cycle). Here, the step by step procedure needed to implement secured code level methodologies, starting from gathering the requirements till the process of creating an overall design is displayed. This is done in-order to cover each and every module followed by testing plans for deciding whether the testing can be done in security level, in functionality level, or in the code level. If it is determined to be done in code level, then 4 different processes must be followed. They are:
-
Static Code analysis
-
Developer training
-
Coding standards
-
Secure Coding Libraries
Finally, overall testing results are crosschecked and required changes are made and deployed according to the organisation requirements.
TYPES OF CODE REVIEWS
Before choosing the tools and checklist to conduct a Secure Code Review, you need to take upon questions like
-
Which tools should be used?
-
Which produces better results - Automated tools or Human analysis?
-
Ultimately, which would generate the best result?
As with other areas of your SDLC, the best approach is a mixed approach, combining both manual review as well as inspection using strong static code analysis tool. The approaches are being further classified into different types as cited below:
-
Static Code Analysis
-
Manual Code Review
-
Dynamic Code Analysis
-
Giving Raw Scanner Data to Dev (developers)
Static Code Analysis:
Static code analysis is the process of computer program debugging that is done by examining the code without executing it, and you can find the security and functional level issues prevalent in the code level.
STATIC SOURCE CODE ANALYSIS ARCHITECTURE:
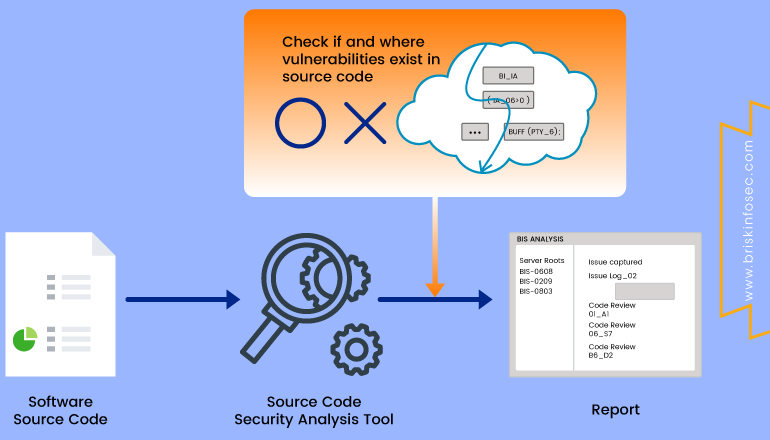
Overall, Static code analysis architecture describes about the scanning of source code in a step by step methodology, starting from importing the source code into the SAST (Static Application Security Testing) tools till categorizing the vulnerabilities into various severity levels, later cross checking the specified vulnerabilities in the code levels, and clearing out the false positives. After it’s done, the results are prepared as a report.
Manual Code Review:
Manual code review can be directly done by developers (self-code review) or by any other security engineers to analyse the vulnerabilities in code level and based on the requirements, they try to fix the issues in the code level.
Dynamic Code Analysis:
Dynamic code analysis can happen multiple times during each iteration and here it also looks for the unexpected application behaviour, within the interface. Dynamic analysis can offer 24/7 monitoring process and there are various open source and paid tools that are available for testing the code level dynamic analysis. Here, some tools have been listed for your reference:
-
IBM Security App Scan
-
Address Sanitizer
-
Daikon
Giving Raw Scanner Data to Dev:
Providing raw scanner report to developers leads them to face many problems because many scanners provide false positive information’s in the code level, hence we cannot trust the scanner reports blindly. If any codes get scanned by developers or security engineers, then the executed output should be crosschecked by the specific person who is responsible for it and by this, many false positive issues in the code level can be fixed. Here in the below link, you can check the false positive code samples:
https://github.com/slevomat/coding-standard/issues/543
Software technology methodologies:
-
It’s estimated that 90 percent of security incidents result from attackers exploiting known software bugs. Needless to say, infiltrating those bugs in the development phase of software and eliminating them could reduce the information security risks that is faced by many organizations today.
- To do that, a number of technologies are available to help developers catch flaws before they’re baked into a final software release. They include
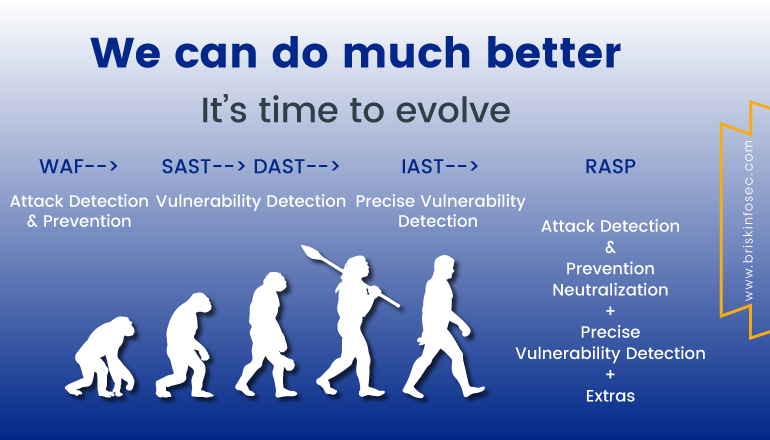
SAST (Static Application Security Testing):
Static Application Security Testing is a technique and class of solution that performs automated security testing and then analyses the overall program source code, to detect the presence of vulnerabilities and flaws that occur within the application. For example, because it does not rely on run time environments, it can be used to test code during development, catching vulnerabilities early on before deploying the application to live.
Advantages:
- Since SAST is processed in the development phase, they can expose the weakness before the software is deployed.
- SAST tools tests the source code, or the binaries in a line by line format. Here, they detect the flaws and give you the chance to fix them before they become a true vulnerability for your organization.
Disadvantages:
- Each SAST tools tend to focus on a subset of a potential weakness.
- It can't identify vulnerabilities outside the application’s code such as those defects that might be found in third-party interfaces.
SAST Tools: RIPS, Snappy-tick,IBM Appscan etc.
DAST (Dynamic Application Security Testing):
Dynamic Application Security Testing (DAST) tests the application from the “outside”, whether the application is in test or in the production environment. Black box penetration testing (or) an automated (or) managed vulnerability scanning can be classified as DAST.
Advantages:
- DAST offers a high level of flexibility and scalability.
- It can be integrated easily with the corporate security strategy.
- It can analyse on both client side and server side.
Disadvantages:
-
Cost Expensive.
-
Requires full compilation upon every code change.
-
It’s not fit for agile methodology.
-
It cannot detect non reflective attacks.
DAST Tools : Checkmarx, Remediate the flag and IBM Appscan etc.
IAST (Interactive Application Security Testing):
IAST (Interactive Application Security Testing) analyzes the overall code for finding out the security vulnerabilities, while the app is run by an automated state, human tester, or any activity “interacting” with the application functionality. This technology reports vulnerabilities in real-time, which means it does not add any extra time to your CI/CD pipeline.
IAST works inside the application and it works in the QA environment, when the automatic functional test is running.
Advantages:
- API testing: Many functional API tests are automated, making IAST a good fit for teams building in micro-services, etc.
- It also promotes the reuse of testing cases. IAST avoids the need to re-create the scripts for security testing.
Disadvantages:
- They can have a negative impact on application performance: Since they add instrumentation to the code, they also change the way in which the code performs.
-
It is a newer technology, so other issues or drawbacks may still arise.
IAST Tools: Contrast Security
RASP (Runtime Application Self Protection):
It detects both the attack and the vulnerabilities from both, outside and inside. Also, it provides less number of false positive issues when compared to SAST and DAST. It also injects the security in the code level environment during run time. They are further classified into various types as follows:
-
Pattern Matching with blacklist
-
Dynamic Tainting
-
Virtualization and compartmentalization
-
Code Instrumentation and Dynamic white list
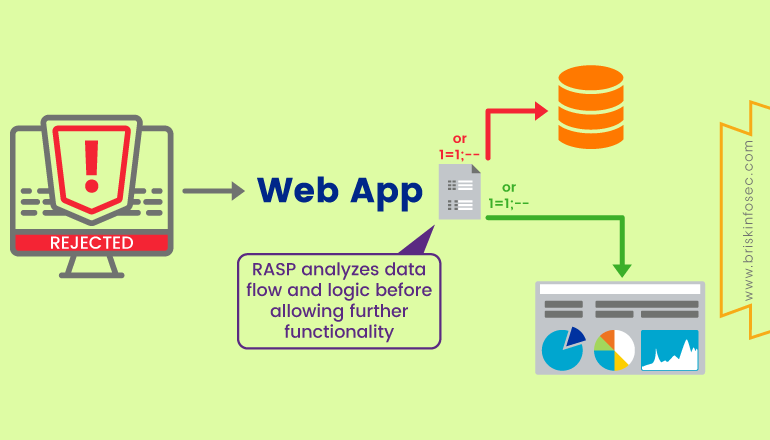
Advantages:
-
Injects security at Run time.
-
Fewer false positives.
-
No use of Blacklist.
-
Detects both attacks and vulnerabilities.
-
Applies Defence inside the application.
Disadvantages:
-
New vulnerabilities occurred in the applications are yet to be updated.
-
Cost Expensive.
-
If the enterprises are using the third party apps, the flaws cannot be mitigated using RASP.
RASP Tools: Immunio
Conclusion:
You now know how important it is to do a secure code review as well as the various tips and techniques needed to be adopted, before doing a secure code review. Adversities arising due to insecure codes and its catastrophic repercussions have proven to be a nefarious challenge to cyber security professionals in the past and in the present. To prevent these kind of attacks from striking your organization and annulling the dignity of your reputation in the both far and near future, it is an alarming indication to approach a right cyber security vendor for ensuring safety.
How Briskinfosec helps you:
In order to incorporate best secure code services, Briskinfosec emphasises organizations to practice the following:
- Implement SSDLC (Secure Software Development Life Cycle) during the development phase itself.
- Providing proper and piquant secure code training to the developers.
- Follow prudent and legitimate secure coding standards.
Briskinfosec has eliminated bugs persisting in the codes of various applications to many organisations. Our efficient Secure Coding Services swiftly finds the code level issues and eliminates them. Further, we have an expert development team whom have a vast experience in developing proper coding and in identifying vulnerable codes.
Curious to read our case study?
Our stakeholder, one of the leading content service provider wanted us to perform a secure code review service. We immediately assessed the entire codes and identified the vulnerable ones. We also patched those bugs completely and gained appreciation from our stakeholder for our unflinching perseverance. Check our case study to know the way we accomplished.
Last but not the least:
Searching internet about the companies affected by attacks, the type of loss experienced, and all these to be searched one by one in one’s busy life schedule, indeed is time-consuming and patience-exhausting. Doesn’t this sound tedious?
Don’t panic!
Briskinfosec prepares Threatsploit Adversary Report on a monthly basis, by encompassing various cyberattacks and its impacts on the respective company. In spite, of searching aimlessly in search engines, just a single click on our Threatsploit report is more than enough. You’ll be amazed, as what you’ve bought is a billion could’ve never got.


