Introduction
SQL injection is often referenced as the most common type of attack on websites. It is being used extensively by hackers and pen-testers on web applications. The OWASP Top Ten lists SQL Injection (or SQLi), along with other types of injections, as the first security risk facing web applications.
Metacharacters are characters in a system (command interpreter, file system, or database management system, for example) that have special meanings. Single and double quotes, for example, are used as string delimiters in SQL queries. They are used at both the start and end of a string. This is why injecting a single or double quote into a query causes it to break and throw an error. The query interpreter will either complain about invalid syntax or report that it can't find the quote's pair at the end of the string if a single quote is injected into the entry point.
When a single quote is left unpaired at the end of a query, the system will throw an error. The error returned by a single quote injection could indicate that the user's input was not filtered or sanitized in any way, and that the input contains characters with special meaning in the database.
SQL Injection
SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It generally allows an attacker to view data that they are not normally able to retrieve.
In many cases, an attacker can modify or delete this data, causing persistent changes to the application's content or behavior. In some situations, an attacker can escalate an SQL injection attack to compromise the underlying server or other back-end infrastructure, or perform a denial-of-service attack.
Examples of SQL queries
- Authentication (login window)
- Search boxes (retrieving relevant information from the database)
- URL (modifying the hyperlink)
Types of SQL Injection
There are two types of SQL injection
- Error Based SQL injection
- Blind Based SQL injection
Error Based SQL injection
The Error based technique, when an attacker tries to insert malicious query in input fields and get some error which is regarding SQL syntax or database.
Blind Based SQL injection
Blind SQLI is a type of SQLI technique that works on injecting SQLI query to the database blindly and identify the output based on the change in the behavior of response.
Types of blind SQL Injection
- Boolean based SQLI
- Time-based SQLI
Boolean based SQLI
Boolean-based SQL injection is a technique which relies on sending an SQL query to the database. The result allows an attacker to judge whether the payload used returns true or false, even though no data from the database are recovered.
.jpg)
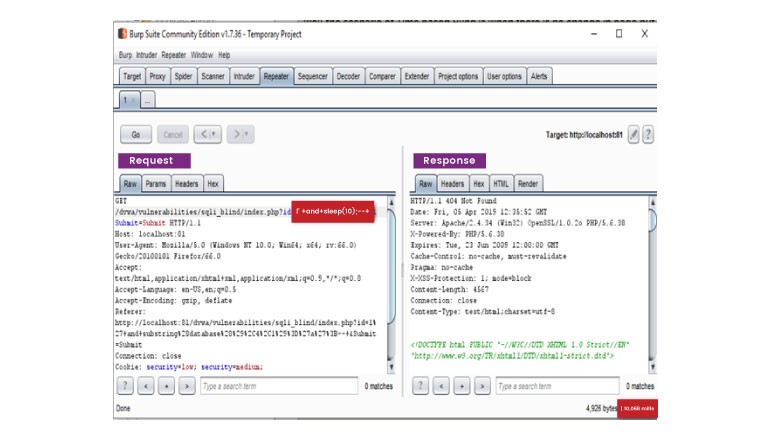
Time-based SQLI
Time-based SQL Injection is an inferential SQL Injection technique that relies on sending an SQL query to the database which forces the database to wait for a specified amount of time (in seconds) before responding. The response time will indicate to the attacker whether the result of the query is TRUE or FALSE.
Why single quotes over double quotes....?
Single quoted strings are the easiest way to specify string. This method in used when we want to the string to be exactly as it is written. When string is specified in single quotes PHP will not evaluate it or interpret escape characters except single quote with backslash (') and backslash(\) which has to be escaped .
The character (') is used because this is the character limiter in SQL. With (') you delimit strings and therefore you can test whether the strings are properly escaped in the targeted application or not. If they are not escaped directly you can end any string supplied to the application and add other SQL code after that.
In most cases the input is checked before being passing into SQL by a well written function, or a parameter is used. Therefore it is likely that if even the most basic type of SQL-injection is stopped, then all types of SQL-injection is stopped for the given form field.
So just putting a ‘ in each entry point is a quick and easy way to get a lot of benefit for the tester and the tester's employer.
Example:
Let’s imagine that you are using the search feature of an application, using the following keyword to search: apple
https://vulnerableURL.com/images?search=apple
The following SQL query is sent in the background:
SELECT * from fruits WHERE name=’apple’
You can add a single quote in your search like ?search=apple’ and the following query is sent. The query structure is broken:
Impact of SQL Injection
A successful SQL injection attack can result in unauthorized access to sensitive data, such as passwords, credit card details, or personal user information. Many high-profile data breaches in recent years have been the result of SQL injection attacks, leading to reputational damage and regulatory fines. In some cases, an attacker can obtain a persistent backdoor into an organization's systems, leading to a long-term compromise that can go unnoticed for an extended period.
Prevention for SQL Injection
To prevent SQL Injections, ensure that proper server-side input validation is performed on all sources of user input.
Errors: Ensure that SQL errors are turned off and not reflected back to a user when an error occurs as to not expose valuable information to an attacker.
Parameterize Queries: Ensure that when a users input is added to a backend SQL query, it is not string appended but placed into the specific SQL parameter. The method to perform this varies from language to language.
Server-Side Input Length: Limit the length of each field depending on its type. For example, a name should be less than 16 characters long, and an ID should be less than 5 characters long.
Whitelist: Create character ranges (ie. Numeric, alpha, alphanumeric, alphanumeric with specific characters) and ensure that each input is restricted to the minimum length whitelist necessary.
Blacklist: Disallow common injection characters such as “<>/?*()&, SQL and SCRIPT commands such as SELECT, INSERT, UPDATE, DROP, and SCRIPT, newlines %0A, carriage returns %0D, null characters %00 and unnecessary or bad encoding schemas (malformed ASCII, UTF-7, UTF-8, UTF-16, Unicode, etc.).
Conclusion
Web sites are static, dynamic and most of the time a combination of both. Web applications need protection in their database to ensure security. SQL injection attacks allow attackers to spoof identity, tamper with existing data, can cause repudiation issues such as voiding transactions or even changing balances, allow the complete disclosure of all data, destroy the data or make it. Otherwise, unavailable, and become administrators of the database server. If an application fails to properly construct SQL statements it is possible for an attacker to alter the statement structure and execute unplanned and potentially hostile commands. It has become a common issue with database-driven web sites as it can be detected and easily exploited, and as such, any site or software package with even a minimal user interaction is likely to be subject to an attempted attack of this kind. In this paper, a case study is provided with a clear distinction among all types of SQL injections these days. Also, attacks on various live websites will provide an understanding of programmers that what are the vulnerabilities which are still prevailing in the web applications. To prevent, detect and mitigate the effect of SQL injection attacks. The aim is to prevent SQLIAs from occurring and also to make it less severe for the future application’s accessed by users.


.png)
