Thief plots heist at home. It takes him some time to figure out how to get into the house without being noticed. What we're doing here is called Vulnerability assessment
The thief could have used a glass door as a weak point to get into the home.
When he realizes that tossing a stone can break the glass, he grabs one and launches it towards the surface of the glass. Penetration Testing refers to the act of breaking a piece of glass with a stone.
Vulnerability Assessment Versus Penetration Testing (VA/PT)
Do you know what is the price of a single medical data on dark web?
In 2022, 2 lakh records from a major hospital in Kochi were exposed. Hackers are more interested in these medical records than they are in stolen credit card information. For identity theft, it contains information including names, birthdates, SSNs, and billing information. The website of the hospital was the source of data breach because it did not follow required VA/PT procedures. The cost of single medical data is close to USD 200. This is true.
VA and PT are both security services targeted at discovering security holes in network, server, and system infrastructure (VA/PT), respectively. Despite the fact that they each serve a distinct purpose, they are sometimes misconstrued as two separate examinations.
The initial stage of security testing, known as vulnerability assessment, aims to identify flaws throughout the whole network or piece of software.
It is a quick automated assessment of servers, systems, and network devices to find configuration problems and major vulnerabilities that an attacker may exploit. Vulnerability Assessment is the answer to question "What is the potential weakness on my network?"
So, what is a Penetration test (PT)
Penetration testing (pen-testing) is a methodical way to find security flaws in an application. It does this by testing a system or network in harmful ways. It is clearly the right thing to do to get into a network or website to find problems and try to fix them. Penetration testing is the answer to the question
"What can be a possible path an attacker can use to exploit the vulnerability?"
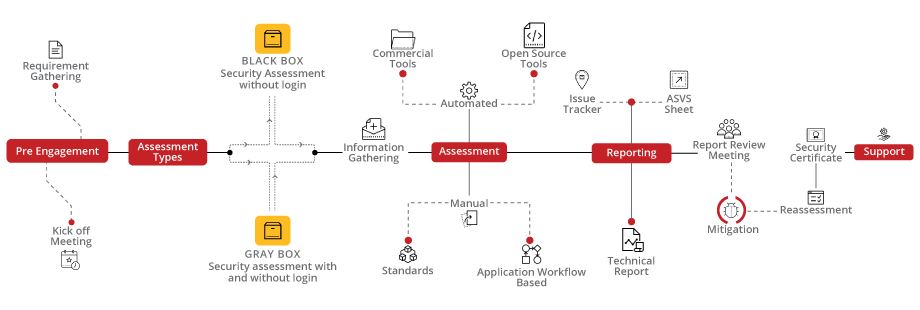
So how does this look like?
Other Terms for Penetration Testing
Different types of penetration test
- Web application Security Assessment
- Mobile application Security Assessment
- Network Security Assessment
- Website security Assessment
- API Security Assessment
- Cloud Security Assessment
- Host Level Security Assessment
- Cyber Intelligence Assesment
- Thick Client security Assesment
- Threat Vulnerability Assesment
- Source Code Review
- Database Security Assesment
- IOT Security Assesmet
- Wireless Security Assesment
Different Modes of Penetration test
- Blackbox
- White Box
- Grey Box
Black Box Testing
In a black box penetration test, the tester gets no information at all about what is being tested. In this case, the pen tester acts out the plan of an attacker with no special permissions, from the first access and execution to exploitation.
White Box Testing
"White box testing" is a way of testing where the tester has access to all of the system's internal code. He is just like an insider.
In this kind of testing, the tester knows what the code is supposed to do.It is a way to test the security of a system by seeing how well it can handle real-time attacks of different kinds.
Gray Box Testing
During a grey box penetration test, which is sometimes called a transparent box test, the tester is only given a small amount of information. This is usually done with login information. Grey box testing can help you figure out how much access a privileged person could have and how much damage they could do.
About VA/PT Standards
- Application Security Validation Standard (ASVS) for (web) applications;
- OWASP publications such as the Top 10 and the ASVS, which are backed by the OWASP Application Security Testing Guide;
- SANS-top 25: the most prevalent and harmful faults in software development;
- CIS-baselines for assessing infrastructure and configuration;
- NIST rules on password and key management, for example;
- NCSC ICT security standards for online applications and Transport Layer Security (TLS);
- Basic Information Security Administration (BIO);
- The OWASP Testing Guide versions 3 and 4, as well as the OWASP Web Service Security Cheat Sheet, when applicable;
- M-ASVS (Mobile ASVS) for mobile applications
- Logius criteria for DigiD evaluations;
- OWASP Mobile Top 10; STRIDE technique in Threat Modeling
Current information from (software) vendors such as Google, Apple, Amazon, Microsoft, and others
Why someone should do VA/PT services?
- To find out who could be our CYBER ATTRIBUTOR
- To find out what makes CYBER CRIME happen.
- To keep your network safe and get more money into your business, which will make you money.
- To make you feel better about data hacking.
- It helps to find weak spots that pose a bigger risk.
- A relook at the security policies of a company are also looked at.
- Since cybercrime costs money, makes customers less loyal, and makes our company look bad, you should use ethical hacking, which is done by certified ethical hackers, if you think your data has been stolen or sent somewhere else.
- Gets help from the White-hat hackers, who work to keep your network safe, are nice people.
To sum up the whole, The adoption of VAPT testing by corporations might be very beneficial. It increases security to safeguard against hacker attacks and illegal conduct. As a result, achieving meaningful security benefits is something that the majority of enterprises take very seriously. Contact us for a quick chat on how to secure your cyber space.