What Is CIS BenchMark
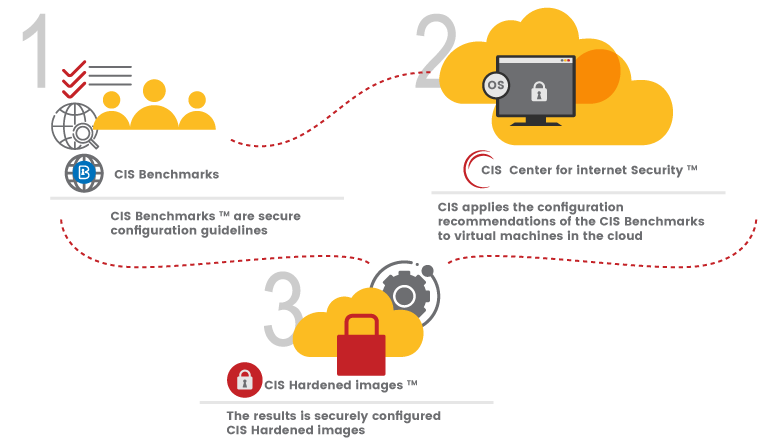
CIS Benchmarks are frameworks for calibrating a range of IT services and products to ensure the highest standards of cybersecurity. They’re developed through a collaborative process with input from experts within the cybersecurity community. More than 100 different benchmarks are covering a range of well-known vendors and systems. CIS Benchmarks guide all areas of an IT network, including operating systems, server systems, office software and network devices.
What parts of an organization can CIS Benchmarks help?
CIS Benchmarks provide standards for the proper configuration of a range of IT technologies and systems. Covering everything from desktop software to mobile devices, these systems are an integral part of any modern organization. CIS Benchmarks provide clear best practice guidance created by a community of experts, so are an important tool for any IT governance strategy.
Organizations can use CIS Benchmarks to make focused improvements to specific areas of their IT systems. Properly embedding IT systems will strengthen vulnerabilities in an organization’s IT network, improving cybersecurity defence.
CIS Benchmarks can be grouped into seven main areas:
Server Software
CIS Benchmarks guide the proper configuration of different server software from a range of vendors. This includes commonly used server software such as VMware or Microsoft Windows Server. The aim is to strengthen cybersecurity through best practice configurations across different areas of the IT server system. There are CIS Benchmarks for database servers, web servers, DNS servers and authentication servers. Recommendations cover topics such as storage settings and restrictions, admin controls, and server settings.
Multi-function Print Devices
This is a best practice benchmark for setting up printer devices across an organization’s office space. These devices have become targets for cyber threats as a gateway into an organization’s network. Recommendations cover topics like file sharing, server configurations, and secure access to wireless networks.
Cloud Providers
Best practice cybersecurity configurations for setting up the most well-known cloud services and infrastructure. There are benchmarks for cloud services and infrastructure from Amazon Web Services, Microsoft Azure, Oracle Cloud Infrastructure, and Google Cloud Computing Platform.
Recommendations cover topics such as network settings, safeguards to ensure compliance with regulations, and IT governance and management.
Mobile Devices
These benchmarks focus on Apple iOS and Google Android mobile operating systems and devices. Benchmarks guide configuring both Apple iOS and iPadOS, as well Google Android operating systems. Recommendations cover topics such as browser and developer settings, app permissions and privacy, and mobile operating system settings.
Desktop Software
CIS Benchmarks provide best practice configuration for desktop software commonly used within modern organizations. This includes benchmarks for the Microsoft Office suite of software, an integral part of the modern office. CIS Benchmarks are also provided for the top web browsers including Google Chrome, Mozilla Firefox, Safari, and Microsoft web browser. Recommendations cover areas like browser settings, management of third-party software, server settings, and device management.
Network Devices
These CIS Benchmarks help with the configuration of network devices and hardware used within an organization’s IT system. These cover network devices and products from a variety of vendors, including Cisco, Juniper, Check Point Firewall, and Palo Alto Networks. Recommendations help to ensure cybersecurity standards across all network devices and hardware within an organization to enhance and strengthen the overall IT Governance strategy.
Operating Systems
CIS Benchmarks help to ensure proper cybersecurity configurations for a range of the top operating systems widely used by organizations. This includes Linux, Microsoft Windows and servers, and Apple macOS. Benchmarks are mapped to different iterations of these operating systems, with best practice guidance for both enterprise and personal versions.
Operating systems form a core part of any organization’s IT systems. CIS Benchmarks help organizations configure them securely, closing vulnerabilities and lowering the risk from cyber threats. Best practice recommendations cover protocols for drivers installation, user profile management, and remote access restrictions.
Why CIS Harden images are necessary
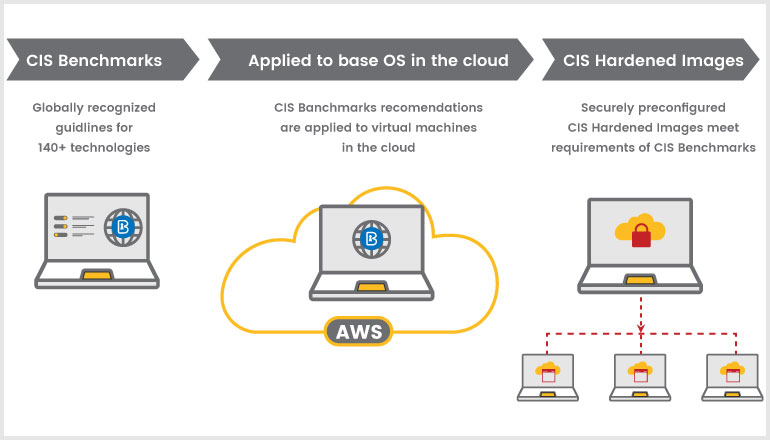
CIS Hardened Images bring the globally recognized security configuration recommendations of the CIS Benchmarks to the cloud. Securely preconfigured virtual machine images are available to spin up immediately from the major cloud provider marketplaces
A hardened virtual image is much more secure than a standard image. Hardened images help mitigate common threats such as denial of service, insucient authorization, and overlapping trust boundaries threats.
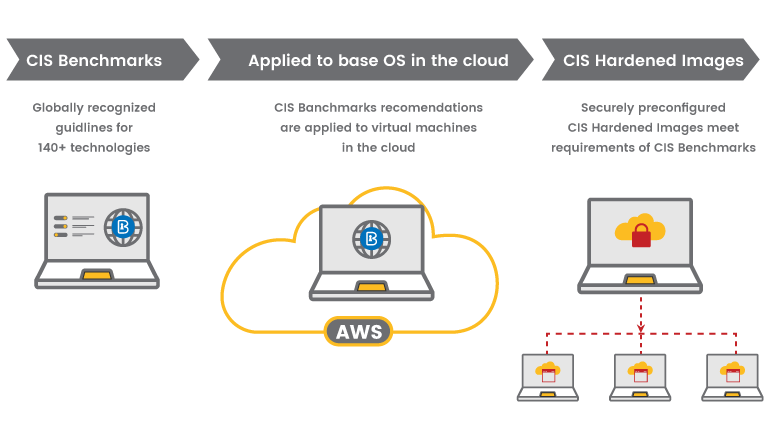
CIS Hardened Images
A single operating system can have over 200 configuration settings, which means hardening an image manually can be a tedious process.CIS Hardened Images are preconfigured to meet the robust security recommendations of the CIS Benchmarks. For the most serious security needs, CIS takes hardening a step further by providing Level 1 and Level 2 CIS Benchmark profiles. Here’s the difference:
-
A Level 1 profile is intended to be practical and prudent, provide a clear security benefit, and not inhibit the utility of the technology beyond acceptable means.
- A Level 2 profile is intended for environments or use cases where security is paramount, acts as a defence in depth measure, and may negatively inhibit the utility or performance of the technology.
The following CIS Hardened Images are available on the Marketplace, as of January 2021:
- CIS CentOS Linux 6 Benchmark-Level 1
- CIS CentOS Linux 7 Benchmark-Level 1
- CIS Microsoft Windows Server 2012R2 Benchmark-Level 1
- CIS Microsoft Windows Server 2012R2 Benchmark-Level 2
- CIS Microsoft Windows Server 2016 Benchmark-Level
- CIS Microsoft Windows Server 2016 Benchmark-Level 2
- CIS Microsoft Windows Server 2016 Benchmark-STIG
- CIS Microsoft Windows Server 2019 Benchmark-Level 1
- CIS Microsoft Windows Server 2019 Benchmark-Level 2
- CIS Oracle Linux 6 Benchmark-Level 1
- CIS Oracle Linux 7 Benchmark-Level 1
- CIS Oracle Linux 8 Benchmark-Level 1
- CIS Ubuntu Linux 16.04 LTS Benchmark-Level 1
- CIS Ubuntu Linux 18.04 LTS Benchmark-Level 1
- CIS Ubuntu Linux 20.04 LTS Benchmark-Level 1
The CIS Benchmarks provide prescriptive guidance for securely configuring Microsoft Windows. Ubuntu, CentOS, and Oracle Linux. The Benchmarks includes over 350 configuration recommendations specific to the operating systems. CIS updates the CIS Benchmarks as threats evolve. Updates can vary depending on the community and the major release schedule of the technology the CIS Benchmark supports. CIS Hardened Images are patched monthly for vulnerabilities and any changes from the CIS Benchmark.
Using CIS Hardened Images for virtual machines (VMs) is a great way to meet certain aspects of compliance frameworks, like PCI DSS or FedRAMP, that require organizations to establish and manage a secure configuration of IT assets deployed in the cloud.
How do I use a CIS Hardened Image?
We can use CIS hardened images in AWS, AZURE, GOOGLE and ORACLE.
For example, In ORACLE cloud platform use these steps to select the CIS hardened images.
- From the menu in the top-left corner, select Marketplace, then Applications.
- On the right side, select Center for Internet Security in the Publisher list.
- Select your favourite CIS Marketplace listing. I chose CIS Ubuntu Linux 18.04 LTS Benchmark 1-Level 1.
- Select the compartment you want to deploy, the image, accept the terms of use and partner terms and conditions and click Launch Instance.
- You can now launch the VM as you usually do, but with the security of a CIS Hardened Image.
Benefits of CIS Hardened Images
- Deploy pre-configured images across networks. Administrators can feel confident knowing that the images conform to recommended cybersecurity best practices of the CIS Benchmarks.
- Eliminate upfront investments. Avoid hardware purchasing, software licensing, and maintenance by working securely in the cloud.
- Scalable computing environment.Work in an environment that can handle increased growth with ease.
- Trusted conformance.CIS Hardened Images include reports showing conformance to the applicable CIS Benchmarks.
- The collective expertise of a global community of IT and cybersecurity professionals.
- Regularly updated, step-by-step guidance for securing every area of the IT infrastructure.
- Compliance management consistency.
- A flexible template for securely adopting new cloud services and for executing digital transformation strategies.
- Easy-to-deploy configurations for improved operational efficiency and sustainability.