CONTENTS:
- What is WPA3?
- Secure transmission with WPA3
- Flaw in WPA3
- Dragonblood attacks – used to steal sensitive information
- Security patches already being deployed
- How Briskinfosec helps you?
- Curious to read our case studies?
- Last but not the least
- You may be interested on
What is WPA3?
Every generation of our technology assures new security promises but parallelly generates the room for new problems. The present world allows users to connect to powerful mainframes, but unfortunately also allows intruders to discover ways to gain access towards user information, tamper the passwords, and in manipulating the access rights. In this 21st century, computers and wireless networks undeniably occupy every aspect of life at schools, hospitals, businesses, libraries. Moreover, even the coffee shops and buses offer free Wi-Fi access. With all these and with hackers craving to ambush your systems, arises the inevitable need for Wi-Fi security. A person connecting via their laptop could be transmitting the passwords to their bank account over the air, and hackers could easily catch sight of it.
One of the biggest problem with allowing access to a local Wi-Fi network isn’t just about Wi-Fi encryption, but how to register devices onto the Wi-Fi network. If there’s a shared password, then anyone who shares that with another person or writes it down, could aid in unauthorized users gaining access to the network. It allows hackers to use the same technique when someone writes down the Wi-Fi password, helping to gain access into the network and start capturing packets.
So, that’s where the WPA3 comes in as a saving grace against those threats. Rather than trusting and relying on shared passwords, WPA3 signs up new devices through processes where it doesn’t require any usage of shared passwords. This new system is called as Wi-Fi Device Provisioning Protocol (DPP). Using DPP, users use QR code or NFC tags to let devices connect into the network. By snapping a picture or receiving a radio signal from the router, a device can be authenticated to the network without compromising security.
Secure transmission with WPA3:
Of course, WLAN network has flaws, but harmless. So, many people started to worry about the possibility of their data being read by others. Hence, Wi-Fi alliance has taken an initiative by introducing WPA3 encryption, promising that the user’s data will be transferred securely from the source to the destination.
But, what are the innovations taken by the WIFI Alliance? What are they?
- Normally, we all know what a secured password should look like. WPA's first improvement is a more robust protection for weak passwords, and this itself protects against brute force attacks. PSK mode is replaced by SAE (Simultaneous Authentication of Equals), which is resistant against active, passive, and dictionary attack. WPA3-SAE secures the protocol even when it is used with PSKs. The WPA2-PSK mode is generally considered to be too weak. With WPA3-SAE, users don’t need to learn new security procedures. The user interface for SAE is identical to a PSK network. Users do not notice anything in the foreground and can easily enter their password. However, in the background, they get a really secure connection.
- The second improvement is to simplify the configuration process and in providing security for devices with restricted display interfaces.This is becoming increasingly important, especially in terms of the IOT (Internet of Things). This innovation is ideal for sensors, intelligent sockets, and light bulbs. Device Provisioning Protocol (DPP) provides these devices with a certificate-like authorisation. It also allows a trusted device such as your smartphone to give another device access to the wireless network. How? By scanning a QR code, using a conventional code or using NFC. Wi-Fi Easy Connect - as the name suggests, isn’t only simple but also extremely secure.
- Open Wi-Fi hotspots in shops, cafes, and restaurants are still a big issue in terms of security. In an open WLAN like this, or in a network secured with a public key (PSK) (e.g. using a login code), the data traffic can be viewed by attackers in the network. WPA3 - or more precisely, Wi-Fi Enhanced Open - puts an end to open networks. The new "OWE" (Opportunistic Wireless Encryption) approach encrypts all the wireless data traffic in previously open networks. Thus, OWE sets a new benchmark for security and it protects against passive attacks.
- As a last innovation, the Wi-Fi Alliance is announcing that WPA3 will include a "192-bit minimum security protocol". This variant of WPA3 for business and government has the Enterprise addition and offers special, bespoke functionalities. This suite has been coordinated with the Commercial National Security Algorithm (CNSA) suite of the National Security Committee.
Above, I’ve briefed about its security, the cool features, how it works, and how it connects the users to the network, but not the cons. It’s explained below:
Flaw in WPA3:
Security researchers discovered new vulnerabilities in the WPA3-Personal protocol, which allows potential attackers to crack Wi-Fi network passwords and get access to the encrypted network traffic exchanged between the connected devices. According to a press release from the Wi-Fi Alliance, the devices impacted by these security vulnerabilities in the WPA3 Wi-Fi standard, "allows collection of side channel information on a device running an attacker’s software, doesn’t properly implement certain cryptographic operations, and use unsuitable cryptographic elements."
Dragonblood attacks - used to steal sensitive information:
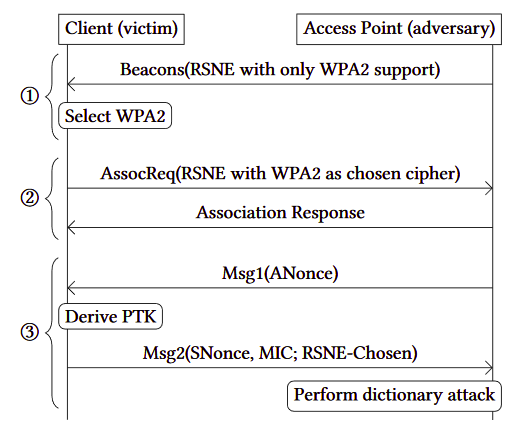
"These attacks resemble dictionary attacks and allow an adversary to recover the password by abusing timing or cache-based side-channel leaks. Our side-channel attacks target the protocol’s password encoding method" said Mathy Vanhoef (NYUAD) and Eyal Ronen (Tel Aviv University & KU Leuven) in their research paper. The researchers also mentioned on the website dedicated to the analysis of the attacks against WPA3's Dragonfly handshake that "This can be abused to steal sensitive transmitted information such as credit card numbers, passwords, chat messages, emails, and so on." The Dragonfly handshake is used by Wi-Fi networks which requires usernames and passwords for access control, as well used by the EAP-pwd protocol which makes all the Dragonblood attacks capable to impact WPA3-Personal ready to be used against EAP-pwd.
"Moreover, we also discovered serious bugs in most products that implement EAP-pwd. These allow an adversary to impersonate any user, and thereby aiding in accessing the Wi-Fi network without knowing the user's password," state the two researchers. "Although, we believe that EAP-pwd is used infrequently, this still poses serious risks for many users, and illustrates the risks of incorrectly implementing Dragonfly", they’ve concluded.
The two researchers have also created and shared open source scripts designed to test some of the vulnerabilities they’ve discovered in the WPA3-Personal protocol:
Dragonslayer: Implements attacks against EAP-pwd (to be released shortly).
Dragondrain: This tool can be used to test to which extent an Access Point is vulnerable to Denial-of-Service attacks against WPA3's SAE handshake.
Dragontime: This is an experimental tool to perform timing attacks against the SAE handshake if MODP group 22, 23, or 24 is used. Note that most WPA3 implementations by default, do not enable these groups.
Dragonforce: This is an experimental tool which makes the information recover from our timing or cache-based attacks, and performs a password partitioning attack. This is similar to a dictionary attack.
Security patches already being deployed:
The Wi-Fi Alliance press release says that "These issues can all be mitigated through software updates without any impact on devices, with the ability to work well together. There is no evidence that these vulnerabilities have been exploited and the device manufacturers who’ve been affected have already started deploying patches to resolve the issue."
Additionally, all impacted vendors were notified of the WPA3 vulnerabilities by the Wi-Fi Alliance, CERT/CC, and the researchers with backward-compatible countermeasures were implemented with the help of Vanhoef and Ronen.
How Briskinfosec helps you?
Briskinfosec has a team of security folks, well experienced in the domain of wireless and radio security assessments. Through our wireless security assessments, we completely assess your wireless and radio devices, in both the aspects of Black box and White box assessments, to completely identify and eliminate the security threats. Moreover, you’ll be collaborating with the organization who won the “India Book of Records” as well “listed as one among the top 20 most promising cyber security solutions provider”. Also, you’ll be working with the one, who is a CERT-In (Computer Emergency Response Team – India) empanelled cybersecurity auditing firm. Reach us out anytime and we’ll help you out surely!
Curious to read our case studies?
If you want to find something intriguing, then our case studies are the best ones. They contain distinct security assessment strategies executed by us during the process of identifying and eliminating various security vulnerabilities, that were troubling our clients. Take a look at them now!
Last but not the least:
If you want peace with security, you must be prepared for a war against cyber threats. To be prepared, you must have a proper knowledge on what are the various attacks (both old and new), how much pain they cause to organizations, and what are the best possible measures to thwart them from striking your security environment. To get a clear vision on all these through search engines and websites, is surely time-consuming and patience-defying. But, we got a precious gift for you. It is our Threatsploit Adversary Report which offers you all the above needs within just one click. Just read it and you’ll completely feel complacent with what you’ve read.
You may be interested on:
- Techniques to Secure your SOAP and REST API
- Cross Site Port Attack XSPA
- SSRF Server Side Request Forgery
- NIST - Cyber Security Framework


