Introduction
Protecting your domain against DNS hijacking attempts is essential in the modern digital world. When hostile actors take over a domain's DNS settings, traffic is redirected to websites, and possible security problems including phishing, malware spread, and data theft may result. To safeguard your online presence, it is crucial to comprehend the different types of DNS hijacking and put preventive measures in place.
Who are the vendors of DNS services?
- Google Cloud DNS
- Cloudflare DNS
- Amazon Route 53
- Microsoft Azure DNS
- Quad9
- Godaddy
How many DNS assaults are still occurring?
According to the IDC Global DNS Threat Report 2022, 88% of organizations experienced one or more DNS attacks. Of those organizations, 70% suffered application downtime, either in the cloud or on-premises. The average cost of a DNS attack was $942,000.
Protecting Your Domain: Keeping Your Online Presence Safe
- Strengthen with DNSSEC: Consider enabling DNSSEC to ensure the integrity of your domain's DNS data.
- Beware of phishing: Exercise caution and avoid sharing sensitive information in response to phishing attempts targeting your domain.
- Stay informed: Keep up to date with the latest security practices and follow recommendations from your domain registrar.
- Act fast: Immediately contact your domain registrar to report the issue and seek guidance.
- Secure your account: Change your domain registrar account password to a strong and unique one.
- Double up on security: Enable two-factor authentication (2FA) is available for an extra layer of protection.
- Check for changes: Review your domain settings for any unauthorized modifications and restore them if necessary.
- Stay vigilant: Regularly monitor your domain activity and be alert for any suspicious behaviour.
DNS Hijacking Prevention
In a hostile assault known as DNS hijacking, the attacker seizes control of a domain's DNS settings and directs traffic meant for a trustworthy website to a malicious one. This can result in a number of security problems, including phishing, the spread of malware, and data theft. Different varieties of DNS hijacking exist, each with a unique attack strategy and set of potential repercussions. The following are some typical forms of DNS hijacking.
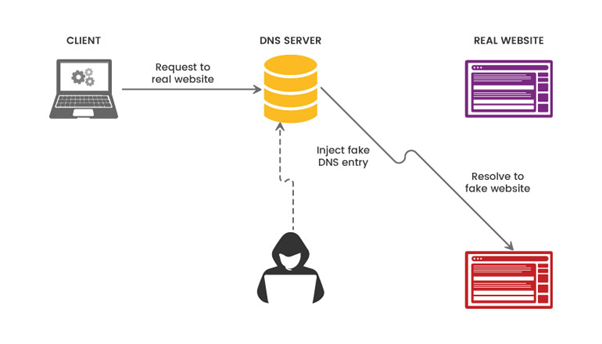
Cache Poisoning
Cache poisoning entails feeding a DNS resolver's cache with erroneous DNS data. Attackers use flaws in the DNS system to alter or spoof DNS replies, which causes traffic to be redirected to malicious websites. Users may end up being routed to phishing websites or pages that contain malware as a result.
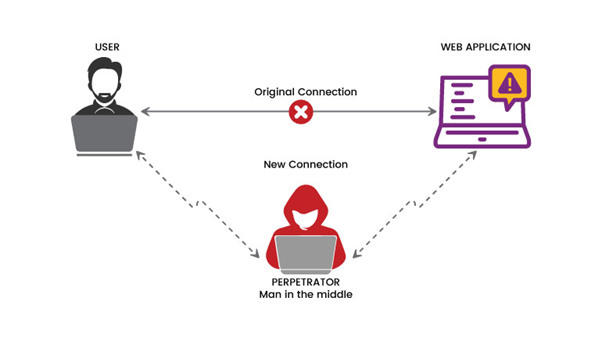
Attacks by a Man-in-the-Middle (MitM)
A MitM attack involves the interception and modification of DNS traffic between a user and a trustworthy DNS server. By altering the DNS replies, the attacker can then send the victim to a malicious website. This kind of hijacking can be done either by compromising network infrastructure or via methods like ARP spoofing and DNS spoofing.
DNS server breach
This happens when an attacker accesses a DNS server without authorization and changes its settings or DNS records. The attacker can gain unauthorized access, steal data, or carry out other malicious operations by compromising the DNS server and rerouting traffic to their intended target.
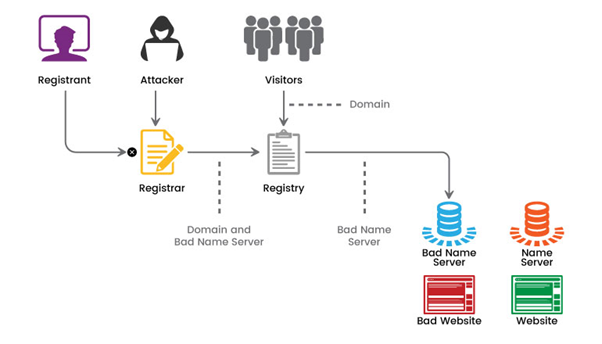
Registrar Hijacking
In registrar hijacking, attackers enter the domain registrar's account without authorization and change the DNS settings for the domain. They have the ability to alter DNS records, reroute traffic to malicious servers, or commandeer email services connected to the domain. Through phishing or other social engineering techniques, this kind of account hijacking frequently targets the domain registrar's account credentials.
DNS capture in routers
Attackers hack routers or other networking hardware to change DNS configuration in this attack. By changing the DNS settings in the router, all DNS traffic passing through the compromised device can be routed to malicious DNS servers, and all connected devices can be routed to malicious websites
Domain Transfer
An attacker can hijack a site and rename it to his own after gaining unauthorized access to the area registrar’s account. By gaining control of the area, they can change DNS settings, divert site visitors, or even hold a website hostage.
These are just a few examples of not-unusual DNS hijackings. As already cited, imposing strong security measures and following exceptional practices can reduce the probability of such attacks. Regularly monitoring, continuously figuring out new threats, and directly responding to any suspicious conduct is critical to maintaining the security of your area.
Consider the following strategies to defend your domain from DNS hijacking attempts
1. Strong and unique password: Ensure that every account related to your area registrar, DNS provider, and website hosting provider has strong and precise passwords. Avoid using the same password repeatedly, and recall the use of a trusted password supervisor to create robust passwords and preserve them securely.
2. Two-aspect authentication (2FA): Enable element authentication where feasible, especially for touchy money owed to your area registrar and DNS provider. 2FA adds extra security with a second step that calls for authentication, generally in the form of a temporary code sent to your cell phone or generated by means of an authentication utility.
3. Registrar Lock: Enable the registrar lock feature by using your area registrar. This prevents unauthorized transfers or changes to your area configuration and adds an extra layer of protection from DNS hijacking attempts.
4. DNSSEC (DNS Security Extension): Use DNSSEC for your domain. DNSSEC adds cryptographic signatures to DNS statistics, ensuring the integrity and validity of DNS records. It facilitates DNS hijacking and different DNS-based total attacks by validating DNS responses.
5. Choose a steady DNS issuer: Choose a good and well-managed DNS company that implements a strong security policy. Look for companies that have a great track record of coping with DNS assaults and offer features like a DNS firewall, anomaly detection, and chance intelligence.
6. Monitor DNS settings: Check your area’s DNS settings often to check for any unauthorized changes. Configure indicators or reports to get on-the-spot notifications of any adjustments to your DNS settings.
7. Update software: Make certain the software and firmware of your domain registrar, DNS company, and other associated systems are up-to-date. Ensure everyday security patches and updates are available and follow them right away to deal with acknowledged vulnerabilities.
8. Educate users: Educate your personnel or team contributors about DNS hijacking and different cyber threats. Train them to identify phishing attempts, suspicious emails, and websites. Promote high-quality security practices to avoid clicking on unfamiliar links or presenting touchy statistics without verifying the legitimacy of the request.
9. Regular backups: Perform regular backups of your website and check other important data. Having an up-to-date backup in case of a DNS hijacking attack or other security incident can help restore your services faster and minimize the impact.
10. Incident Response Plan: Develop an incident response plan outlining the steps to be taken in case of a DNS capture or other security breach. This policy should include procedures for notifying affected individuals, restoring services, and implementing necessary security measures to prevent future attacks.
By implementing these preventive measures, you can significantly reduce the risk of DNS hijacking and increase the security of your domain. It’s important to be vigilant and proactive in protecting your online assets to stay ahead of evolving threats and regularly review the best security practices.
For example, if you registered your domain with GoDaddy, you can take the following steps:
- Activate domain transfer lock: In the domain management interface, locate the option called "Domain Locking" or "Transfer Lock." Enable this feature to prevent unauthorized transfers of your domain to other registrars.
- Confirm the domain lock: After enabling the transfer lock, make sure it's active. Look for any indications or messages that confirm the domain transfer lock is in place.
- Enhance security: GoDaddy offers additional security features. Consider enabling two-factor authentication (2FA) for your account to add an extra layer of protection against unauthorized access.
- Regularly review domain settings: It's important to periodically check your domain settings. Make sure the transfer lock is still active and keep an eye out for any unfamiliar or suspicious changes that could compromise your domain's security.
"Secure your domain name with GoDaddy! Use the domain transfer lock feature to keep it safe. You can prevent unauthorized transfers and protect against domain hijackers with a simple click. Log in to your GoDaddy account, enable the transfer lock, and rest easy knowing your domain is secure. Don't forget to review your settings regularly and consider adding two-factor authentication for added protection. Keep your domain name locked down with GoDaddy!"
Conclusion
Maintaining the security of your online presence necessitates protecting your domain from DNS hijacking. Activate registrar locks, set strong passwords, enable two-factor authentication, consider DNSSEC, and stay current on security best practices. Develop an incident response plan, backup your data on a regular basis, and educate your employees. By taking these preventative measures, you can limit the chance of DNS hijacking and secure your domain. Maintain attention and prioritize the security of your internet assets.


