Introduction:
Nowadays, Artificial Intelligence (AI) plays a pivotal role in daily activities to increased data volumes, advanced algorithms, and improvements in computing power and storage.
Topics covered:
- Types of technologies that are built with AI
- What AI can do for security?
- How companies are using AI in various sectors
- Is it possible to prevent cyberattacks before they happen?
- Conclusion
- Curious to read our case studies
- Last but not the least
- You may be interested in
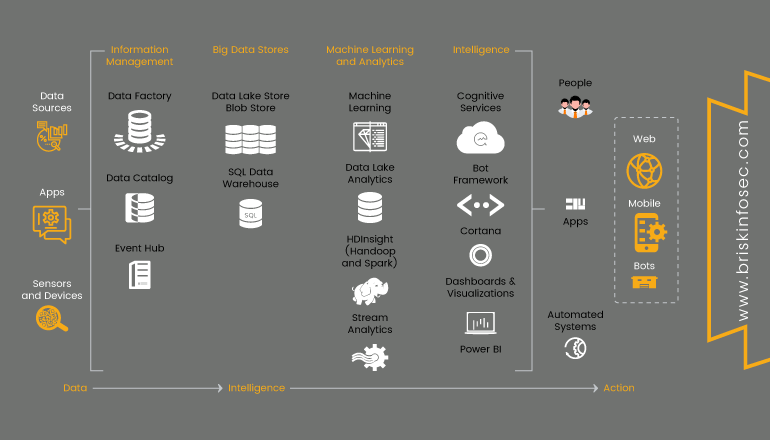
Types of technologies that are built with core AI?
So, AI is not new to this decade. In 1950-1970’s, it was called as “neural networks”; 1980-2010’s it was called as “machine learning” and now at present, it is called as “Deep learning”.
- Neural networks is a biological programming pattern which enables a computer to learn observance data.
- Machine learning is an application which focuses on teaching machines to learn and apply the algorithms to data.
- Deep learning is a major breakthrough, it can change the dynamic development from the ‘program’ computers to ‘teaching’ them.
- Natural-language processing is the technology whether the text to talk feature has been available for a certain time. It increases the accuracy of technology for users, inbound and outbound.
How companies are using AI in these sectors:
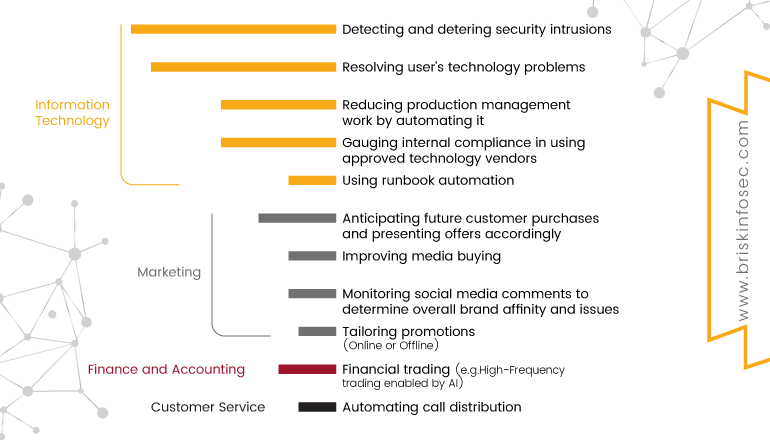
The given chart shows how companies are using Artificial intelligence (AI).
AI is a vast amount of living data with more faster processing efficiency than humans. However, a neural network has the capability to analyze everything that is normal. Nowadays, many companies are using AI and big data. It’s believed that these kind of technologies will help them with digital transformation. Using this, AI (Artificial Intelligence) capabilities are based on automatic learning or in taking decision making based on these data. Nearly 40% of digital transformation projects will be based on Artificial Intelligence by 2019. In addition, 75% of these business tools will use this technology by 2021.
CYBER QUOTE ON AI:
Uses of AI in various business sectors:
There are lot of sectors using AI. Some of them are explained below.
- Banking and finance
- Retail
- Manufacturing
- Healthcare
- Energy
- Logistics and transport sectors
- Insurance
- Education and tourism
Banking and finance
These sectors are currently using forefront of investment in AI. Here they are expected to replace the retail sector throughout the year. This sector will spend around $3.3 billion this year alone on fraud investigation projects, credit risk calculations, and threat prevention systems.
In many organizations, the automation bots, automatic learning and adaptive intelligence are becoming part of the financial team at a high speed. This banking and finance sector will be using them greatly in the upcoming years.
Healthcare
This sector will be investing $1.7 billion this financial year. This sector mainly works under various categories like tele-diagnosis, intelligence emergency triage. Even, surgery can be performed by robots.
Logistics and Transport
Nowadays, Artificial Intelligence (AI) is the most important in transport sector. Self-driven cars are using AI. There are companies which are using self-driven cars like Tesla, Google, Toyota, Uber and etc., while some companies are still developing the AI automated cars. It’s expected that these solutions will move around $10 billion into the market, by 2050.
Is it possible to prevent cyberattacks before they happen?
For a cyberattack to be successful, there are some steps to be followed successfully. These steps are called “Cyber Kill Chain”. Attackers might leave some traces in some of these steps or they can access information about the targeted company that was leaked before, in information acquisition phase. We can see similar situations like this. Preventing these kind of situations is only possible if you observe your company constantly with the eyes of an attacker. In addition to that, knowing what the attackers can find when they do their research about your company beforehand, and as a result, take precautions to prevent these situations.
Some of the information that can be accessed about your company are:
- Hacktivist posts that target your company in dark forums or social media.
- Leaked information about your company’s customers and employees. (E-mail, passwords, credit card information etc.)
- Phishing website, mobile, and desktop applications about your company.
Conclusion:
Hence, the various techniques needed to secure your AI products have been discussed.
Curious to read our Case studies?
People learn about security assessments from both online and offline modes. But to know the strategy used in a security assessment, case studies are the best sources. To know our unique techniques used during different assessments, check our case studies.
Last but not the least:
Don’t miss our Threatsploit Adversary Report which has the monthly collection of globally happening cyber breaches and the companies affected by them.

