Larger organization have built lots of inefficiencies that impact their ability in managing huge amount of data created as part of their business. In most cases, the internal security team fail to identify and protect the business data. Let us explore more.
Contents
- Introduction
- what is Cyber-Attack
- passive Attacks
- Recent attack on WHO
- Active Attacks
- IoT Based
- Conclusion
Introduction
With ever changing need to access data from anywhere, we tend to prefer cloud services. When travelling, due to perceived emergencies, we mistakenly connect our official devices to public Wi-Fi or on unsecured networks? This invariably leads to organization getting to be affected.
We will discuss in detail how large organizations are frequently attacked by hackers.
What is Cyber-Attack?
An attack is employed to steal, destroy or gain an unauthorized access to the computer, network, and infrastructure. These are performed by an individual or by a group of experts targeting the organisation information with the intention to publicly expose or privately exploit. There are two major kinds of cyber-attacks used by attackers.
- Passive attacks
- Active attacks
Passive attacks
These attacks are performed by the intruder whose intention is to gain entire system/network access without leaving any footprints. These attacks are often carried without any changes being observed by the users. There are various kinds of attacks which can take place over a network by just scanning their open ports and by using older versions of vulnerable software. These attacks are mostly common in wireless interface as they could be identified or detected. In the development of IoT where all organizations moving towards digital have a major thread occurring towards their organization. They can broadly be classified into sniffing and tapping into their wireless network interface.
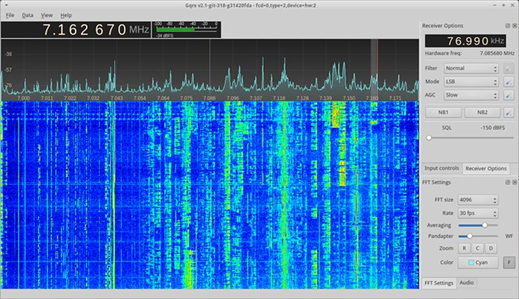
Sniffing
For simpler and better understanding let us consider a remote car. The main objective of the Intruder is to sniff the data packets transmitting and to identify the type of modulation scheme used between the devices, i.e., the remote and the car. We should identify the operating frequency of the device and build some blocks by using the GNU platform where python is used in its backend. Then by just plugging in the SDR we used to sniff the data and display it in FFT where we can see the data moving whenever user accesses the remote and moreover this attack can be performed even at a distance of upto 30 meters with less or no distortion.
Tapping
Before performing this process the intruder should sniff the target and confirm whether the device is active or not. Once done he can just modify the data without the help of the user to perform this attack like the qualpwn vulnerability.
Recent Attacks on WHO (World Health Organization)
World Health Organisation has reported some suspicious activities in their networks. Also hackers around the world use WHO as their name and target individuals to gather username passwords of their accounts. To get frequent updates subscribe to our newsletter.
Preventing Passive attacks
- Use better encryption algorithm.
- Use better entropy with rolling code scheme for pairing the devices.
- Disconnect the device when not in use.
- Limit the range of frequency to a certain distance or operate whenever necessary.
- Turn off the device when it is not active more than 2 minutes.
Want to secure your Digital Assets please contact Us
Active attacks
In these types of attack, the user could be identified after a certain period of time or when finishing the attack. The most common such attacks are ransom-ware, malware and DDoS. Let us understand how these attacks are further classified and the impact on the victims.
Product based attacks
Before digging into the types of attacks, let us dive into the virtual world. We have two organizations doing business with the same motto where one is an established company and the other is just a start up.

To be easier let’s assume the established as X and the other as Y. X produces more products per year and they sell it across by just doing a basic functional level testing and they don’t tend to care about their cyber-risk factor in their product after a small change. They simply perform the basic functional level and cyber-security audit and they sell their product. As Y has to portray their product in a different way they tend to perform basic cyber security test to their product and they follow the procedures after each and every updates of the product. Intruders can also attack the small companies but they won’t find large volumes of data.
Infrastructure based
X usually has more no of Internet service provider and data centers. They also have to perform periodic audits not only to their products but also to their data centers. On the other hand, Y is a small team with less number of units and if any breach occurs, Y can detect quickly than in the case of X. Here X plays a major role as it has more number of devices, they should be organized in an proper manner for example if X has 100 routers and 5 data centers, at least three person will be required to maintain all these and they should have been assigned with equal responsibilities to all the infrastructure related services.
Click here to know more about Infrastructure security testing
IoT Based
Now let us come to the hardware part of security in X and Y. Both the firm consists of attendance machine for their employees, network firewall settings; Where X additionally consists of automatic coffee machine, smart speaker and other appliances. These smart devices are more vulnerable from the intruder perspective. You would have heard that the IoT has no standard till date, have you ever thought about this?? As these smart devices are publicly exposed over the internet there are various ways for an intruder to enter into your premises without any physical intervention. They don’t need to come to access it physically. It is enough if they compromise any one of the employees system by providing an attachment in mail or sending a notification in the mobile device. When the user clicks on it the employee comprises the mobile devices and once it gets connected to his office network the intruder has full access to view the each nook and corner of the network and thereby performs an attack. The surveillance cameras are also easily accessed by the intruder if he knows the manufacturer’s name and the model number. Statistics says that most attacks are initiated from the cameras.
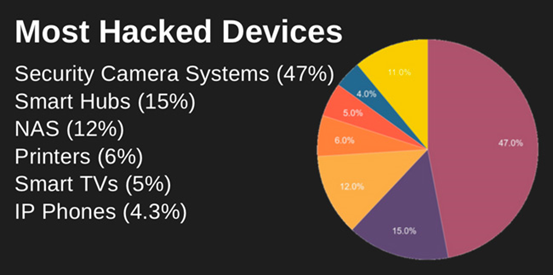
Recently attacked MUKASHI botent compromised the NAS system of the zyxel system which is used by most of the corporates. These systems should be connected to a separate network isolated form the others. I would suggest the X companies to follow the below guidelines to be away from cyber-attacks .
Click here to know more about IOT security testing
Preventing active attacks
- Desktops/laptops should be provided for the employees.
- Employees should not connect their desktops to their personal networks using mobile data or any other publicly available networks.
- Signals strength should be limited within their premises.
- While using wireless connectivity we suggest you to update your firmware and applications.
- Isolate the connected devices to a separate network as guided by FBI, which minimizes the data loss when attacked.
- Replace the devices if the support gets terminated.
- Don’t use default passwords in any of your networks, instead create a strong password with a combination of uppercase lowercase and special characters.
- Try to segregate the routers with respective of the departments.
Conclusion
Since the larger organization consists of more number of devices it is difficult for the organization to manage. Hackers will not care regarding the company’s size it may be a small or big sized company all they need is to comprise the entire system to gain access. Hence following the above provided guidelines organizations would be safe and will stay away from cyber-attacks.




