Synopsis:
- Introduction
- What is cyber kill chain?
- Phases of cyber kill chain?
- How cyber kill chain will be beneficial for organizations?
- Conclusion
- How Briskinfosec can help you?
- Curious to read our case studies?
- Last but not the least
- You may be interested in
Introduction:
The Cyber Kill Chain framework is a part of the Intelligence driven defense model for identification and prevention of cyber intrusion activities (i.e. Hack or Breach). This model identifies the best exploiting strategies that hackers may execute for achieving their goal.
In this blog, we will look into the cyber kill chain stages, methodologies and what cyber kill chain is.
What is cyber kill chain?

Originally, the term “Kill Chain” is used in military to predict the steps which an enemy might use to attack a target. However, pertaining to cybersecurity, Lockheed Martin in 2011 proposed a concept called ‘Cyber Kill Chain’ that’s similar to the Kill Chain model in military. It defines the steps and strategies that an intruder would incorporate in order to gain access to a network for exploiting and compromising the data.
Cyber Kill Chain (also referred as Cyber-Attack Chain) is an industry-accepted methodology for understanding how intruders can attack an organization’s IT environment. This model gives a clear understanding and also assists the IT security teams to plan and build the defense strategies and technologies in order to kill or disrupt the attacks at various stages. It greatly benefits the security professionals in implementing the essential security controls and strong remediation measures to secure their organization. In more specific, it’s an intrusion specific and detection assisting method.
Phases of cyber kill chain:
Cyber Kill Chain gives an eagle view for one of the cleverest hacking strategies.
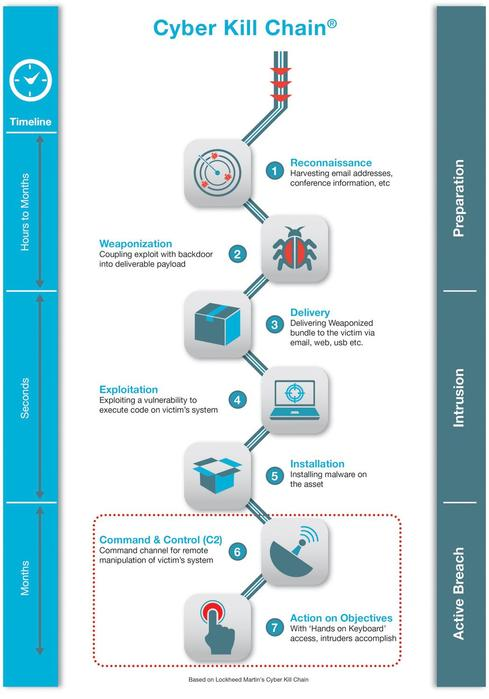
Every stages of the Kill Chain represents a specific and the next level goal of the attacker’s intention. Besides this, it also provides insights for the cyber security teams on how to counterfeit the intruder’s strike.
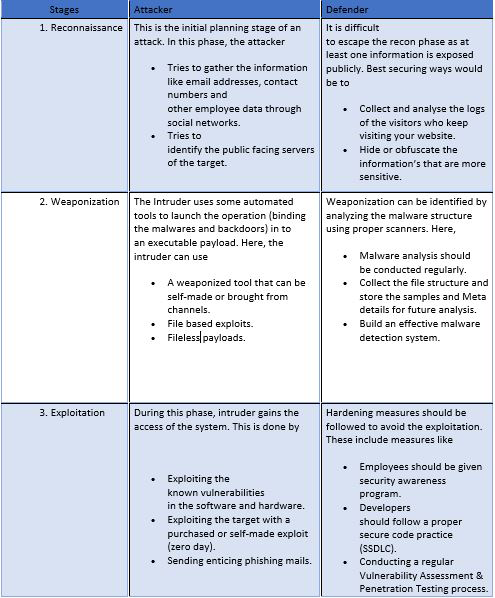
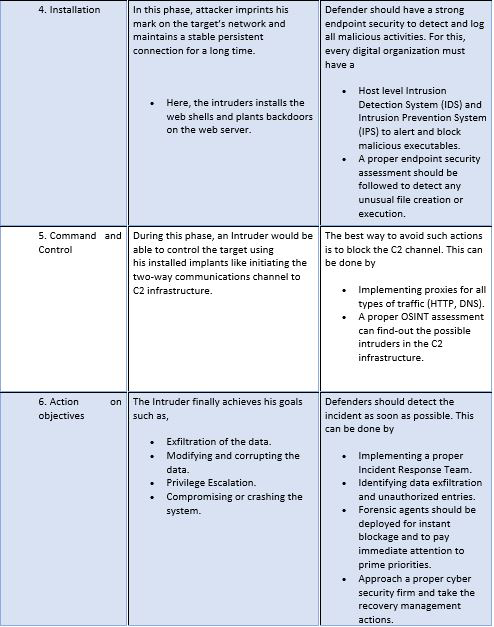
How cyber kill chain will be beneficial for organizations?
Cyber kill chain helps organizations to get a clear understanding about all the possible attack vectors and the security threats that may arise externally. This framework reduces the information exposure of an organization and makes your business secure. By implementing the following steps, cyber beneficiary could be attained. They are
- Implementing a layered security approach.
- Providing neat awareness about the global threats.
- Validating whether the security controls are implemented in the organization or not.
Conclusion:
Like all other security models, cyber kill chain also has its own merits and demerits. The main concept of this model is to disrupt the chain earlier, before any major damage or breach takes place. Implementing the right cybersecurity strategies on time will cut-down the possibility of facing cyber threats.

How Briskinfosec can help you?
- A proper OSINT assessment helps to know about the information exposure of organizations and its employees. We have an expert team to do it successfully.
- However, OSINT alone is obviously insufficient to know the complete security status. Hence, a proper penetration testing is mandatory. We have been listed as “one among the top 20 most promising cybersecurity providers in India.”
- We provide distinguished security trainings to create human awareness.
To know further, kindly reach us out.
Curious to read our case studies?
Providing a proper security to clients isn’t a deed that’s accomplished within a snap. There are certain strategies, thinking’s and implementations that should done depending on the client’s requirements. Only then, the process of eliminating the vulnerabilities would be done successfully. Well to know our security assessment strategies, kindly check out our case studies.
Last but not the least:
Gone are the days when phishing links looked suspicious, trojans and malware’s left a trace for forensic professionals to be discovered, and many cyberattacks showed the symptoms of their presence. Of late, cyberattacks have evolved menacingly alongside the evolution of technology, and cybercriminals are becoming harder to be trapped due to their improved anonymity. To know about these globally occurred month-based notable cyberattacks, the miscreants behind it, the impacts they’ve caused and much more, just read out our Threatsploit Adversary reports. It’s a single report where you can spot all these within a single click. Just check them out!
You may be interested in:
- Layer Wise Analysis of Security in IOT
- Host Header Attack
- Top Trending Web app security vulnerabilities
- Beware of Data War



