Table of content
- Train employee
- Access control over data
- Secure Network
- Are encrypting or not ?
- Logging and Monitoring
- IOT security
- Regular security Assessments
- Comply with patient privacy laws?
- Data backup plan
- Talk to an expert
The health care or medical industry is extremely important which has different components including hospitals, doctors, nursing, diagnostic laboratories, pharmacies, medical device manufacturers, and other components of the health care system. The health care is important to the people around the world and as-well as to the global economies it plays an important role as being one of the largest employers in the global economy as-well. At the same time, cyber attacks are an increasing threat across all critical sectors including health care. In this sector its more concerning because attacks like ransomware or any other security threats is not only impacting the infrastructural and systems but also the patients PII and medical records across the worlds.
In order to stay away from the data breaches and cyber attacks, healthcare organizations should implement security measures which should address all the attack surfaces. Here we have highlighted 10 most important things to secure your Healthcare applications.
Train employee
Humans are vulnerable, they are considered as the biggest threat in all the industries, when it becomes health care industry even small human mistake can lead to data breaches, cyber attacks and other consequences for healthcare organizations.
So educating your employee is very important and especially about security. Conduct awareness programs which would have these topics:
- How to avoid Phishing attacks, SE (Social Engineering) attacks
- Training about HIPAA violation
- What is Password management policy

Is Access control everywhere?
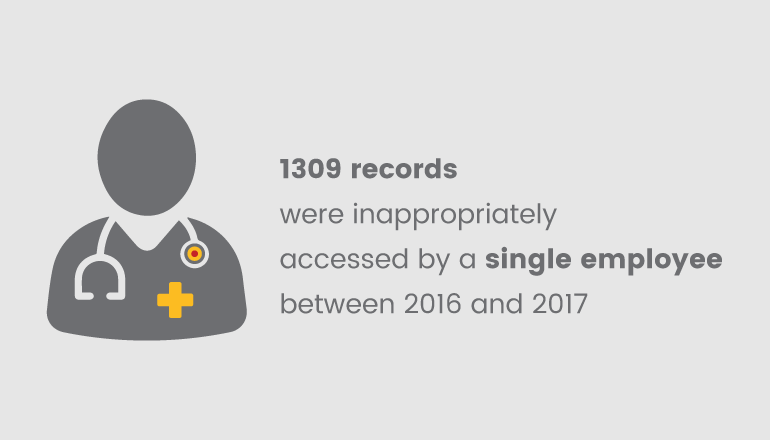
Implementing and managing access control in healthcare is important than giving physical access to the digital assets. For example, in hospital, there will be so many employees like Doctors, Nurses, physician, billing specialist, etc. Everyone should be configured with role-based access control for accessing the EHR (Electronic health record) and also should be given access to the log system in order to monitor the activities which would help in detecting and preventing the data breaches.
Healthcare industry should have authentication and access restrictions to block the unauthorized access to biometrics and PII details of patients. All the users should have Multi-factor authentication to block the brute force based attacks. Healthcare organizations should have controls to block actions like data, such as uploading/downloading internal files, unauthorized email communications, copying or printing files to external sources via USB, external drives.
Are encrypting or not?
Encryption is a must for Health care related applications whether it is an internal or external usage. Encryption is protecting the data in transit and at rest makes it difficult for the attackers to decrypt the sensitive information even if they have access to the data. Healthcare standards like HIPAA recommends that applications should be implemented with encryption measures such as applications should have Secure Sockets Layer (SSL) this encrypts information transmitted between the application and server.
Encrypting data in server side is also important and nowadays everything is moved to cloud only. Blockchain is a new technology for storing the data securely which gives more benefits like improved security, cost, speed etc., it also has downsides but if you are planning to improve the data security then blockchain has lot to offer.
Secure network
Hacker’s goals always are to get into your internal networks to do the damage and are you prepared enough to protect? When we talk about network and specifically perimeter device like Border routers, Firewalls, IDS/IPS, VPN devices and DMZs devices in your organization should be configured securely because these devices can reduce the attack surface. Doing external network assessments in periodic basics is highly recommended.
Logging and Monitoring
Logging and monitoring is crucial for all size of organization nowadays, especially for healthcare industry, it enables to detect and block attacks at real-time. Having Incident Response solutions like SIEM helps to monitor the users who access the data from where ever they are and gives data like their device information, locations and activities. This kind of information will be useful for auditing as well, and it helps organization to identify vectors like entry points, because of the attacks and risk behind that which helps to improve protective measure. Having Incident or breach response plan is really important when data breaches occur, because it guides the staff and stakeholders what to do.
IoT security
Internet of Things (IoT) is not new to medical industry but securing IOT devices and services is new to medical industry and risk associated with these in healthcare are high because from medical devices like cloud connected cardiac to blood pressure monitors, pacemakers, cameras used to monitor physical security are connected to a network. Make sure the below practices are in place for IOT devices:
- Maintain the device management policy
- Maintain IoT devices have their own network which is not connected directly to critical infras.
- Monitor the IoT devices network traffic with SIEM or other solutions to identify malicious activity.
- Disable the services or devices when it is not used.
- Patch management for up-to-date version.
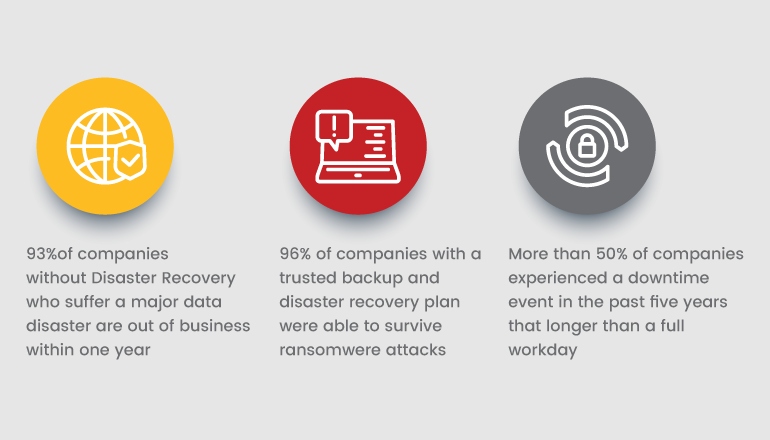
Data Backup Plan
Blocking cyber attack is a “Cat and mouse” game but we can back up the data in worst case scenarios like ransomware attacks, natural disaster, etc. In Infosec we have one magical triangle to make sure our security that is “CIA” in which “A” stands for Availability which means data should be available 24/7. A well managed and tester recovery plan can always reduce the impact, interruption in data availability and cost to repair. If you are a global company, then its a good idea to separate backups based on each region which would be helpful to stay away from chain of attacks. Doing these data backup and having recovery plan will help you to meet the HIPAA regulatory requirements.
Regular security Assessments
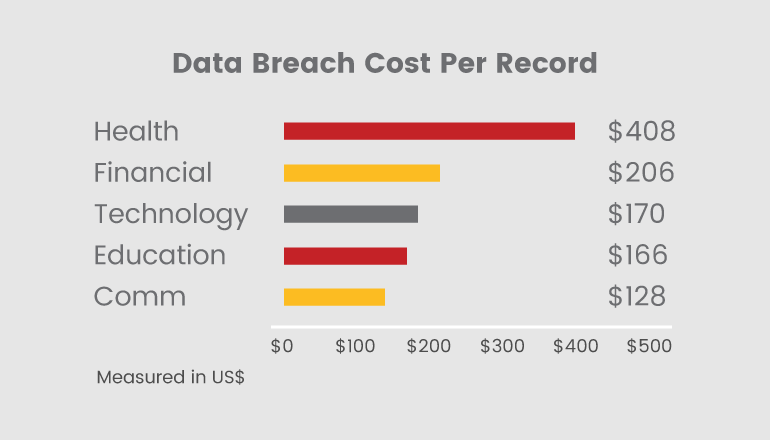
Even if you have done all the given steps there is still one left to do for securing your applications and data, doing Security Assessments or Penetration testing is important to identify the hidden vulnerabilities to remove the weak points. Doing assessments with ethical hackers will help you to “””mic”” the same way to identify the vulnerabilities like “black hat” hackers does. By doing security assessments periodically helps to identify and mitigate the risks because security experts will do the breaches and will advise how to fix the vulnerabilities also. These practices will be helpful to avoid loss of money from data breaches, reputation damage and penalties from regulatory agencies.
Comply with patient privacy laws?
There are several laws and regularities that offer the best solutions and practices to ensure compliant and secure applications. We have highlighted a few best guidelines and compliance standards that organizations should take a look while developing applications such as,
- HIPAA
- GDPR
- PIPEDA
- Electronic Data Interchange (WEDI)
- Integrating the Healthcare Enterprise (IHE)
Acquaint with these standards and policies to meet industry standards and compliance regulations.
Talk to the experts
“Effective cybersecurity is a shared responsibility”
The health care industry is not just a business; it is your responsibility to protect it and the individuals as well. If you’re planning to build/release applications for the usage of an internal hospital or for the public, you will need an expert team to take care of the security. If you are in need of any assistance, do contact us.

