Introduction
Zero-day vulnerabilities are a major threat to the security of computer systems and networks. These vulnerabilities are unknown to software vendors and their users, which makes them very difficult to defend against.
In recent years, there has been a growing trend of cyber-attacks using zero-day vulnerabilities. This is due in part to the fact that it is becoming increasingly difficult for attackers to find and exploit known vulnerabilities. As a result, attackers are turning to zero-day vulnerabilities as a way to gain access to systems and networks.
Cyber forensic audits can help find zero-day vulnerabilities in their early stages. By analyzing the system's logs and memory, forensic investigators can look for evidence of malicious activity, such as the use of a zero-day exploit. This evidence can then be used to identify the vulnerability and patch it before it is exploited by attackers.
“Cyber forensic audits should be conducted before releasing any product, which helps in understanding the intricacies of digital evidence. Conducting thorough forensic examinations can unveil hidden vulnerabilities, strengthen security, and ensure the integrity of the product. By embracing cyber forensic audits, organizations demonstrate a commitment to robust cybersecurity practices and proactive risk mitigation.”
How Cyber Forensic Audits Can Help To Find Zero-Day Vulnerabilities
Log Analysis
Log analysis is the process of collecting, processing, and analyzing log data. Log data can be used to identify malicious activity, such as the use of zero-day exploits.
Several open-source tools can be used for log analysis, including Logstash, Elasticsearch, Kibana, and Splunk. These tools can be used to collect log data from a variety of sources, including web servers, application servers, and operating systems.
Memory Analysis
Memory analysis is the process of extracting and analyzing data from the memory of a live system or a memory dump. Memory data can be used to identify malicious activity, such as the presence of malware or the execution of a zero-day exploit.
Many open-source tools can be used for memory analysis, including Volatility, WinHex, and FTK Imager. These tools can be used to extract and analyze memory data from a variety of systems, including Windows, macOS, and Linux.
Malware Analysis
Malware analysis is the process of analyzing malware to understand its behavior and how it infects systems. Malware analysis can be used to identify zero-day exploits that are used by malware.
Several open-source tools can be used for malware analysis, including Cuckoo Sandbox, VirusTotal, and MalwareBytes. These tools can be used to analyze malware in a sandbox environment or to scan files and URLs for malware.
The Importance Of Cyber Forensic Audits
Cyber forensic audits are an essential tool for organizations that want to protect themselves from zero-day attacks. By regularly conducting cyber forensic audits, organizations can identify and patch vulnerabilities before they are exploited by attackers.
In addition to finding zero-day vulnerabilities, cyber forensic audits can also help organizations to:
Identify other types of malicious activity:
Cyber forensic audits can help organizations identify other types of malicious activity, such as data breaches and denial-of-service attacks.
Gather evidence for legal proceedings:
If an organization is the victim of a cyber-attack, cyber forensic audits can be used to gather evidence that can be used in legal proceedings.
Improve the security posture of the organization:
Cyber forensic audits can help organizations to improve their security posture by identifying and addressing vulnerabilities.
Real-world case study
In January 2023, a zero-day vulnerability was discovered in the MOVEit Transfer software. The MOVEit Transfer software is a managed file transfer (MFT) solution that is used by organizations to securely transfer files between different systems. This vulnerability allowed attackers to execute arbitrary code on the affected systems. In July 2023, the Clop ransomware gang began exploiting the MOVEit Transfer vulnerability to gain access to organizations systems. Once the Clop ransomware gang gained access to an organization's system, they could install ransomware or steal data. The Clop ransomware gang has claimed to have infected hundreds of organizations with their ransomware. The Forensic Experts have examined the Affected system logs to uncover potential signs of suspicious activity. Specifically, they have focused on identifying any indications of unauthorized access or modifications made to the MOVEit Transfer software on July 8. Additionally, they have reviewed the WAF (Web Application Firewall) logs to determine if any malicious traffic was intercepted and blocked on the same day. As a conclusion, they found that the July 8 MOVEit zero-day attack was delivered via a phishing email.
Most common cyber forensics frameworks
The SANS Investigative Framework:
The SANS Investigative Framework is a comprehensive framework that covers all aspects of cyber forensics investigations. It includes some tools and procedures that can be used to collect, analyze, and preserve digital evidence.
The NIST Computer Forensics Framework:
The NIST Computer Forensics Framework is a framework developed by the National Institute of Standards and Technology (NIST). It provides a high-level overview of the cyber forensics process and includes some tools and procedures that can be used to collect, analyze, and preserve digital evidence.
The ENFSI Digital Evidence Guidelines:
The ENFSI Digital Evidence Guidelines are a set of guidelines developed by the European Network of Forensic Science Institutes (ENFSI). They provide a detailed overview of the cyber forensics process and include some tools and procedures that can be used to collect, analyze, and preserve digital evidence.
These are just a few of the many cyber forensics frameworks that are available. By using a cyber forensics framework, organizations can ensure that their cyber forensics investigations are conducted consistently and systematically.
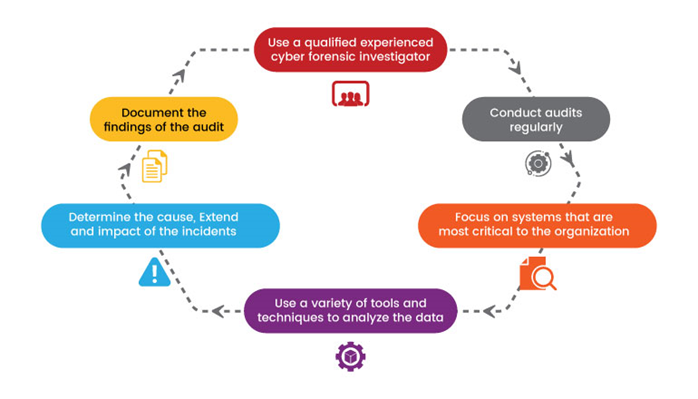
Tips for Conducting Cyber Forensic Audits
Here are some tips for conducting cyber forensic audits:
Key Components of a Cyber Forensics Framework
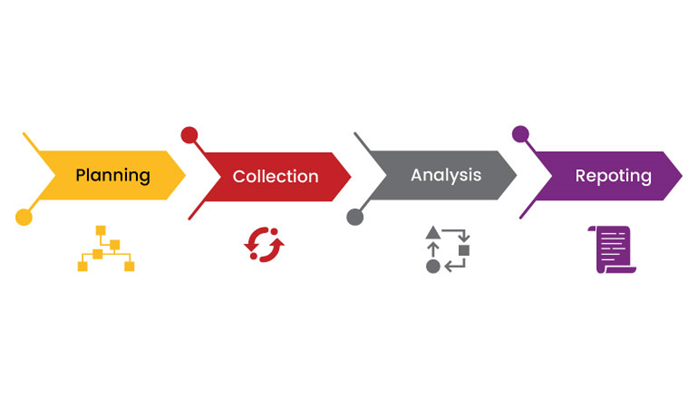
Planning:
The planning phase of a cyber forensics’ investigation involves identifying the goals of the investigation, determining the scope of the investigation, and developing a plan for collecting and analyzing the evidence.
Collection:
The collection phase of a cyber forensics investigation involves collecting digital evidence from the affected systems and devices. This evidence can include log data, memory data, and malware.
Analysis:
The analysis phase of a cyber forensics’ investigation involves analyzing the digital evidence to identify the evidence that is relevant to the investigation. This evidence can be analyzed using a variety of tools and techniques, including log analysis, memory analysis, and malware analysis.
Reporting:
The reporting phase of a cyber forensics’ investigation involves reporting the findings of the investigation to the appropriate stakeholders. This report should include a description of the evidence that was collected, an analysis of the evidence, and the conclusions of the investigation.
Conclusion
Cyber forensic audits are an essential tool for organizations that want to protect themselves from zero-day attacks. By regularly conducting cyber forensic audits, organizations can identify and patch vulnerabilities before they are exploited by attackers.


