Content
- Introduction
- Watering hole
- Ransomware Phishing
- Google Docs Phishing
- Whaling attack
- Dropbox Phishing
- Pretexting
- Baiting
- Quid Pro Quo attack
- Tailgating
- Whaling / CEO Fraud
- Vishing
- Email Spoof check
- What is SPF?
- What is DMARC?
- Conclusion
Introduction
An Organization can protect their digital assets, which are production systems, servers; several network devices and so on, by implementing firewalls, intrusion detection and prevention systems, honeypots, honeynet. All these IT defenses cannot protect your organization if a social engineering attack happens. Social engineering is used to exploit humans to gain access to un-authorized resources, login credential and personal information. By exploiting human curiosity, greed and kindness to gain access to restricted access buildings or making the users to install backdoor software. Social engineers use a number of techniques to fool the users into revealing sensitive information. We are going see a different way how a social engineering attack may happen.
Watering hole
Watering hole attack will be done by injecting malicious code into the Web page of a site where the targets used to visit. By compromising websites within a specific sector that are visited by specific individuals of interest for the attacks. When the victim visit the compromised website a backdoor Trojan is installed on his computer. Attackers would compromise a website months before they actually use it for an attack. Once compromised, the attackers periodically connect to the website to ensure that they still have access.
This way, the attackers can infect a number of websites in one stroke, thus preserving the value of their zero-day exploit. Attacker inspects the website logs to identify any potential victims of interest.
The efficiency of Watering Hole attacks increases with the use of zero-day exploits that affect victim’s software, victims have no way to protect their systems from the malware diffusion.

Ransomware Phishing
Phishing emails contain a link to download malware, sometimes in the form of ransomware. Ransomware phishing attacks hold the infected computer hostage until the victims pay.
Google Docs Phishing
Google Docs phishers spoof a legitimate-looking log in prompt to trick their victims into handing over their passwords. Attackers can then get into files, videos, documents, spreadsheet and whatever else is stored there
Whaling attack
Whaling is evolution of phishing attacks that uses sophisticated social engineering techniques to steal confidential information, personal data, access credentials to restricted services/resources, and specifically information with relevant value from an economic and commercial perspective. What distinguishes this category of phishing from others is the choice of targets: relevant executives of private business and government agencies. The word whaling is used, indicating that the target is a BIG FISH to capture. The scam email is designed to masquerade as a critical business email sent from a legitimate authority, typically from relevant executives of important organizations. The content of the message sent is designed for upper management and reports some kind of fake company-wide concern or high confidential information.
Dropbox Phishing
File-sharing platform is particularly interesting to scammers looking for personal information. Attacker uses an email that appears to be from the website and prompts the victim to log in and the attacker use it to log in to the victim’s Dropbox and access private files and photos, take the account hostage.
Pretexting
Pretexting is the practice of presenting oneself as someone else to obtain private information. Usually, attackers create a fake identity and use it to manipulate the receipt of information. The pretexting attack heavily pretends on the attacker’s ability in building trust. By manipulate the victims into performing an action that enables an attacker to discover and exploit a point of failure inside an organization. An attacker can impersonate an external IT services operator to ask internal staff for information that could allow accessing system within the organization.
Baiting
Exploiting the human’s curiosity the main characteristic is the promise of a good that hackers use to deceive the victims. Attackers use a malicious file disguised as software update or as generic software, disseminating infected USBs tokens in the parking lot of a target organization and wait for internal personnel insert them in the corporate PC. The malware installed on the USB tokens will compromise the PCs gaining the full control to the attacks.
Quid Pro Quo attack
A Quid Pro Quo attack (aka ‘something for something’ attack) promises a service or a benefit based on the execution of a specific action. Attacker offers a service or benefit in exchange for information or access. Attacker impersonates an IT staffer for a large organization. Attacker attempts to contact via phone to the employees of the target organization then offers them some kind of upgrade or software installation and request victims to facilitate the operation by disabling the AV software temporarily to install the malicious application.
Tailgating
Attacker seeking entry to a restricted area which lacks the proper authentication would walk in behind a person who is authorized to access the area. Attacker impersonates a delivery driver or a caretaker who is packed with parcels and waits when an employee opens their door. The attacker asks that the employee hold the door, bypassing the security measures.
Whaling / CEO Fraud
Attackers will target high-level employees and executives to gain access to their email accounts or spoof them. If they’re able to do that, it puts the entire business at risk. When the CEO or the head of a department asks for some files, most people wouldn’t question it. Attacker with access to a high-level account can also gain access to employees’ information, hold the network hostage, and cause financial loss.
Vishing
This is an attack done through Voice over IP (VoIP). Because a VoIP server can be used to appear as virtually anything, and the caller ID can be changed. It might appear that someone close to the corporation is calling or like an important outside entity like a bank or the IRS.
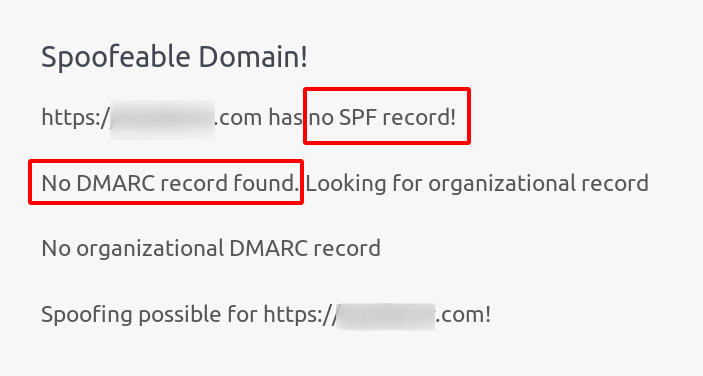
Email Spoof check
Email Server of domain should have SPF (Sender Policy Framework) record and DMARC (Domain-based Message Authentication, Reporting & Conformance) record, both of which are used to prevent fake emails (email spoofing or forgery) attack. Hence, it’s easily susceptible to email spoofing.
The below link is used send the email if the mail ID is spoofable.
https://emkei.cz/
What is SPF?
Sender Policy Framework (SPF) is an email authentication method designed to detect forging sender addresses during the delivery of the email. SPF alone, though, is limited only to detect a forged sender claimed in the envelope of the email which is used when the mail gets bounced
What is DMARC?
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication protocol. It is designed to give email domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. The purpose and primary outcome of implementing DMARC is to protect a domain from being used in business email compromise attacks, phishing emails, email scams and other cyber threat activities.
Conclusion
Now we have understood how to protect our organization completely. We should give awareness to the employees about social engineering attacks in our Organizations. The employees should get notifications frequently like how to handle suspicious e-mails, people, phone calls, messages. The employees should not discuss about their work outside the organization. With good common sense there is no need to fear about social engineering attacks.


