What is the Java Spring Framework?
Spring is a popular lightweight Java platform application framework that enables developers to easily create Java applications with enterprise-level features and then deploy them as an application on servers such as Apache Tomcat or as stand-alone packages with all the required dependencies.Spring Framework is used by millions of developers to produce high-performing, easily testable code.
Spring Cloud Function is a Spring Boot-based function computing framework.It enables developers to concentrate on implementing business logic and increasing development efficiency.Many tech titans, including AWS Lambda, Azure, Google Cloud Functions, Apache OpenWhisk, and other serverless service providers, use Spring Cloud Function.
What is Spring4Shell?
Spring4Shell is a remote code execution (RCE, code injection) vulnerability in Spring Core that is exploited via data binding.The attacker can simply execute code from a remote source on the attacked victim by exploiting it.Spring4Shell affects all Spring Core versions, and the flaw can be exploited on any JDK9 or newer.
Spring Cloud Function (CVE-2022-22963) versions 3.1.7 and 3.2.3 contain a Remote Code Execution vulnerability. Unauthenticated attackers can exploit the flaw by inserting malicious SpEL (Spring Expression Language) expressions into specially crafted HTTP request headers, resulting in arbitrary remote code execution on the target system.
Spring has also confirmed the zero-day vulnerability known as Spring4Shell (CVE-2022-22965) in Spring Framework versions less than 5.3.18 and 5.2.20, which an attacker could exploit to gain arbitrary code execution.To address the vulnerability,Spring Framework versions 5.3.18 and 5.2.20 have been released.Spring WebFlux and SpringMVC applications running on JDK 9+ are vulnerable.
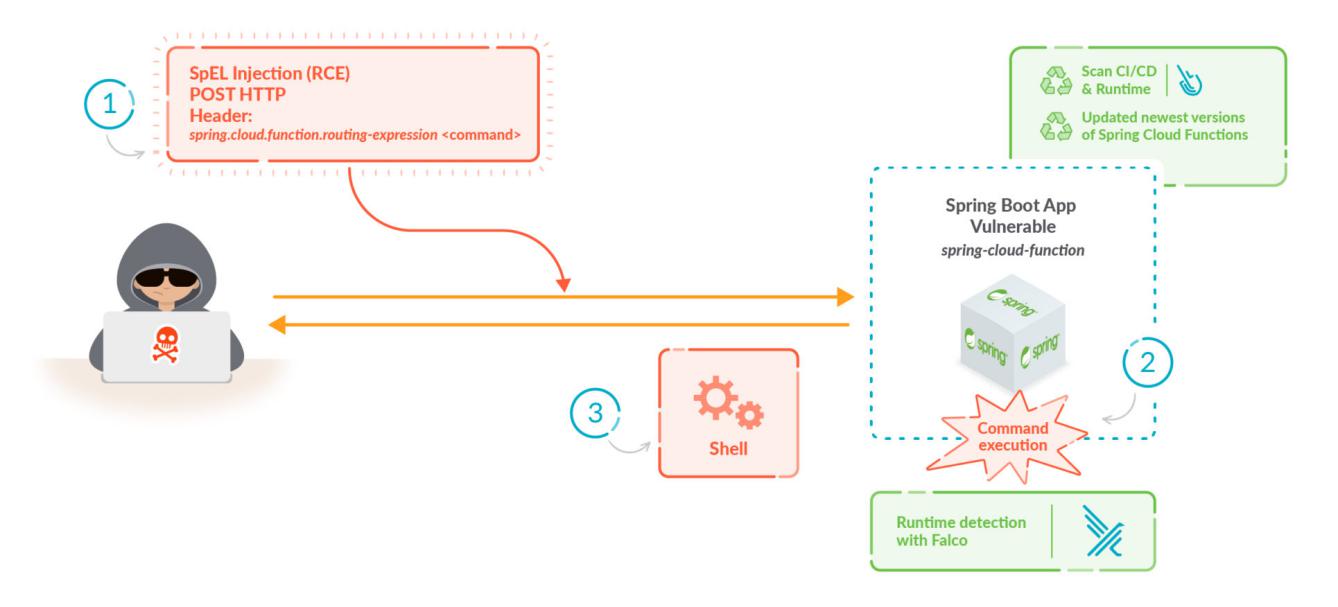
Impact of Spring4Shell
Spring Cloud Function (CVE-2022-22963) versions 3.1.7 and 3.2.3 contain a Remote Code Execution vulnerability.Unauthenticated attackers can exploit the flaw by inserting malicious SpEL (Spring Expression Language) expressions into specially crafted HTTP request headers, resulting in arbitrary remote code execution on the target system.
How to identify whether your organization is vulnerable to Spring4Shell ?
Malicious attackers can exploit the Spring vulnerability if an application operates under the following conditions, according to the Spring Framework RCE early announcement. :
- Runs on JDK 9 or higher
- Uses Apache Tomcat as the servlet container
- Packaged as a standard WAR and deployed in a separate Tomcat instance.Spring boot deployments with an embedded Servlet container or reactive web server are unaffected. .
- Depends on
spring-webmvcorspring-webflux - Spring Framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, and older versions are supported.
How to detect Spring4Shell Vulnerability?
There are several methods and tools available to determine whether or not an application is affected here we investigate the following possibilities: :
1.Dependency Check open source tool
Dependency Check is an open source tool that can be used to discover flaws in other open source libraries.It can be used as a command-line tool, with a Maven or Gradle plugin, or integrated with third-party tools, among other things.
Run the CLI and refer it to a folder to scan for vulnerable libraries, for example: dependency-check —scan webapps.
When run, the tool generates an html report with a list of vulnerabilities.The Spring4Shell vulnerability (CVE-2022-22695) is illustrated in the following example:
.png)
2. The Apache Maven Dependency plugin
Apache Maven Dependency plugin is used to identify whether your projects use affected libraries. To find out if your application exposes the vulnerability, navigate to the directory of your Maven project and run the following three commands:
Spring Core RCE
mvn dependency:tree-Dincludes=org.springframework:spring-beans
Below we can see that the application uses spring-beans version 5.3.13 and therefore has the vulnerability.
.png)
How to mitigate Spring4Shell attacks?
To mitigate Spring4Shell:
- Upgrade your Spring installation immediately to version 5.3.18 or higher, or 5.2.20 or higher.
- If you are unable to upgrade to 5.3.18/5.2.20 or higher, use one of the following workarounds:
- Using a @ControllerAdvice, set disallowedFields on WebDataBinder.
- However, when applied centrally, this may result in loopholes, such as when a controller sets disallowedFields locally via its own @InitBinder method, which overrides the global setting.
- Extend the RequestMappingHandlerAdapter to update the WebDataBinder after all other initialization is complete.
- In your Spring Boot application, declare a WebMvcRegistrations bean (Spring MVC) or a WebFluxRegistrations bean (Spring WebFlux).
- In the absence of Spring Boot, you can switch from @EnableWebMvc to directly extending DelegatingWebMvcConfiguration and overriding the createRequestMappingHandlerAdapter method.