WHAT IS OWASP DEPENDENCY TRACK
Dependency Track is a free, open-source continuous component analysis platform that helps businesses discover and mitigate supply chain risk. In addition, the software keeps track of the vulnerabilities associated with the libraries in the portfolio, as well as their versions, to decide whether the library is outdated, deprecated, or current. Currently, the OWASP Dependency-Check supports five programming languages. Java and.NET are fully supported, with Ruby, Node.js, and Python receiving experimental support.
The OWASP Dependency-Track compiles a list of Common Platform Enumeration (CPE) entries using several analysers. CPE is a structured naming strategy with a way of comparing names to a database. In the Maven Project Object Model file, the analyser looks for a combination of groupId, artifactId, and version (POM.XML file).
When it comes to vulnerability management, reporting is critical since it delivers actionable insights to all security and development teams, as well as providing stakeholders with the data they require. These requirements can be met by the OWASP Dependency-Check, which can provide reports and exports in a variety of forms, including XML, CSV, JSON, and HTML.
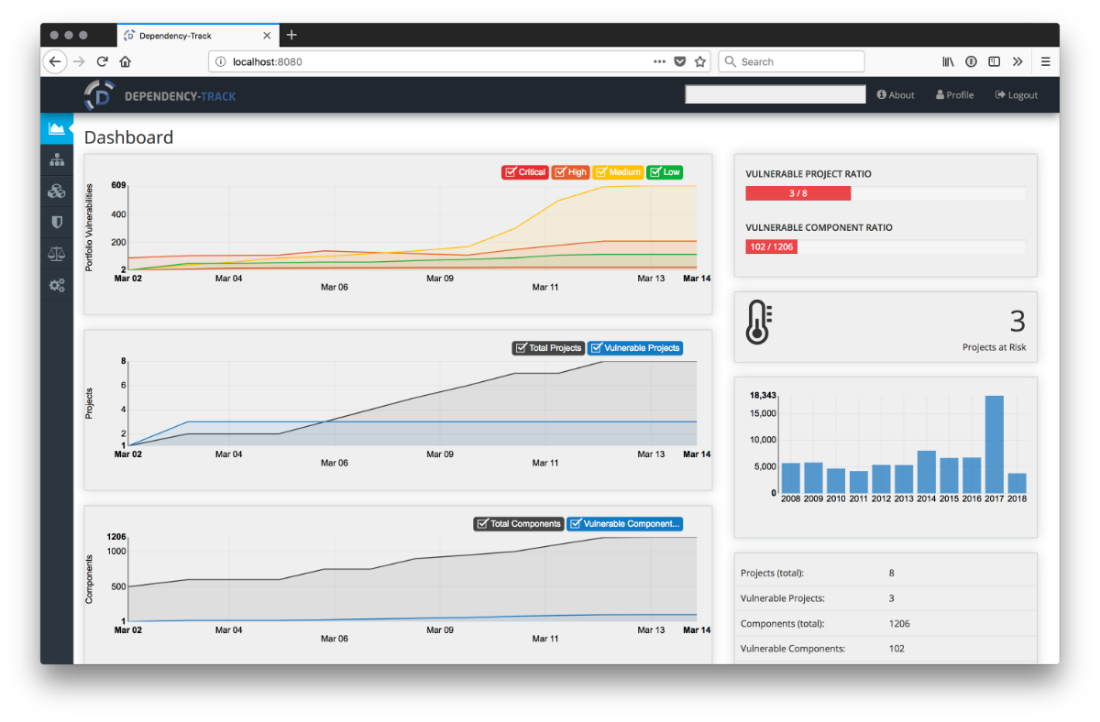
INSTALLATION
Dependency-Track has four distribution variants. They are:
- API Server
The API Server includes an embedded Jetty server as well as all server-side functions, but not the user interface. As of Dependency-Track v4.0, this variation is brand new.
- Frontend
The user interface that can be accessed using a web browser is known as the frontend. The frontend is a single-page application (SPA) that may be installed separately from the Dependency-Track API Server. As of Dependency-Track v3.8, this variation is brand new.
- Bundled
The API Server and the Frontend user interface are combined in the Bundled variant. From Dependency-Track v3.0 through v3.8, this variant was known as the executable war and was the preferred distribution. This variation is supported, although it is deprecated and will be phased out in the future.
- Traditional
The API Server and Frontend user interface are combined in the Traditional form, which must be deployed to a Servlet container. This variation is no longer supported, has been deprecated, and will be phased out shortly.
Deploying with Docker is the easiest and fastest method of getting started. No prerequisites are required other than a modern version of Docker. The installation can be followed using two methods, which are explained below:
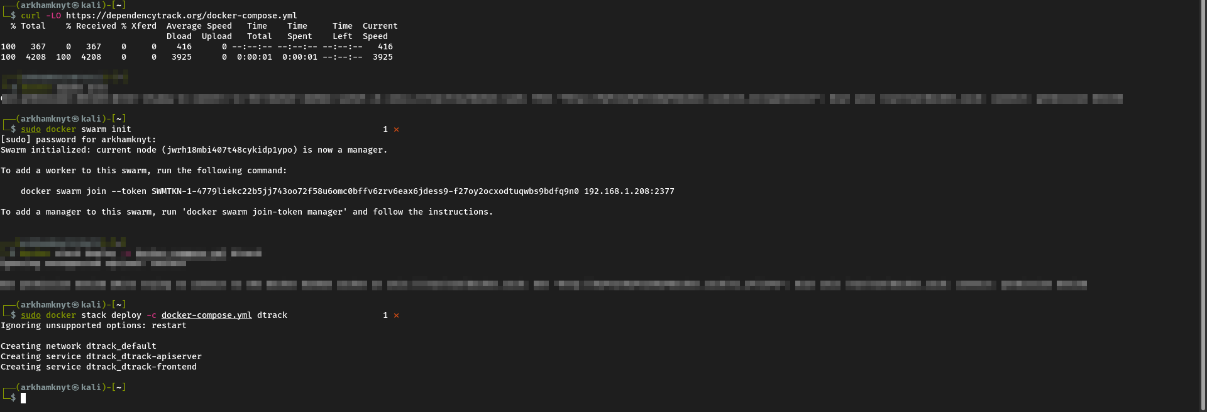
- Using Docker Swarm
# Downloads the latest Docker Compose file
curl -LO https://dependencytrack.org/docker-compose.yml
# Initializes Docker Swarm (if not previously initialized)
docker swarm init
# Starts the stack using Docker Swarm
docker stack deploy -c docker-compose.yml dtrack
Alternatively, the OWASP Dependancy Track can be installed using manual execution.
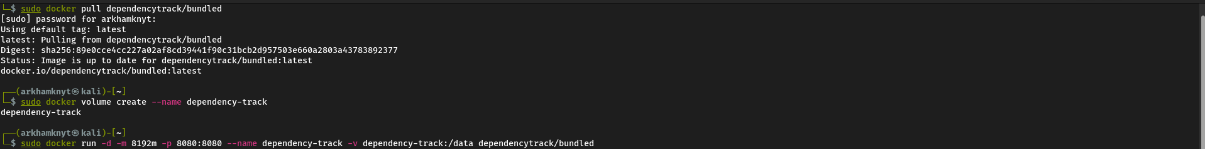
- Manual Execution
# Pull the image from the Docker Hub OWASP repo
docker pull dependencytrack/bundled
# Creates a dedicated volume where data can be stored outside the container
docker volume create --name dependency-track
# Run the bundled container with 8GB RAM on port 8080
docker run -d -m 8192m -p 8080:8080 --name dependency-track -v dependency-track:/data dependencytrack/bundled
Upon starting Dependency-Track for the first time, multiple tasks occur including:
- Generation of default objects such as users, teams, and permissions
- Generation of the secret key used for JWT token creation and validation
- The population of CWE and SPDX license data
- Initial mirroring of all supported vulnerability data sources (National Vulnerability Database, NPM Advisories, etc)
Note: The initial mirroring may take between 10 - 30 minutes or more. Do not interrupt this process. Wait for the completion of all mirroring tasks before shutting down the system. These tasks can be monitored by watching dependency-track.log or the Docker containers console. An administrative account is created on the initial start-up with the following credentials: username: admin and password: admin
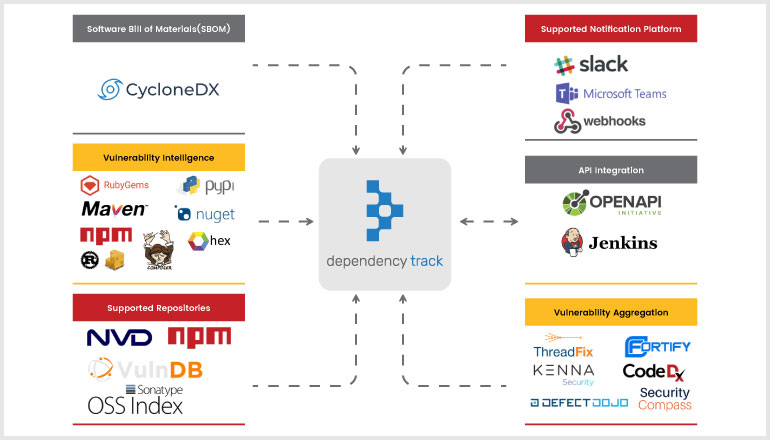
DEPENDENCY-TRACK INTEGRATIONS
Dependency Track is built to fit seamlessly into our Continuous Integration and Continuous Deployment workflows. It includes a robust API and a Jenkins plugin that allows us to incorporate this procedure into our pipelines to accomplish all of this.
DevOps teams can utilise Dependency-Track to speed up operations and development while maintaining control over the use of external components and the dangers they may provide. However, Dependency Track combined with Dependency-Check enables developers to stay on top of their open-source components early in the development process with support for command-line integration. This allows seamless integration with other tools, build systems and APIs, helping developers to detect security vulnerabilities as early on in the CI/CD process as possible, without interfering with development time. This product also includes an integrated alert system that can be accessed by email or through connections with messaging services like Slack or Microsoft Teams. All of them can be customised using templates.
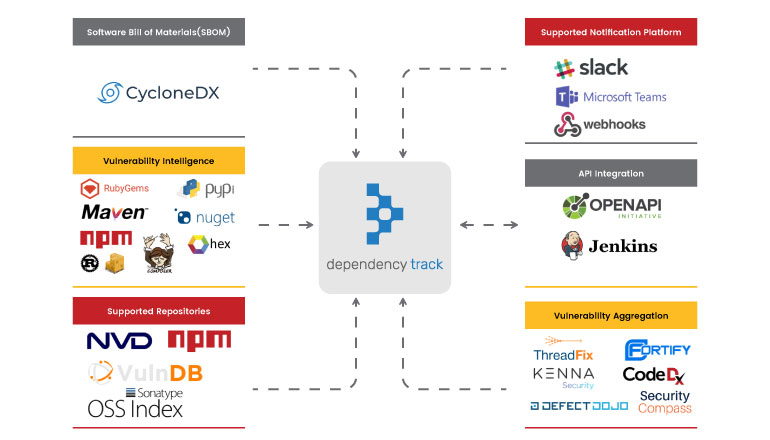
WHY IT IS SO GOOD
OWASP Dependency Track assesses the security of third-party libraries, making it a unique tool in the security sector.
The OWASP Dependency Track offers the following features:
- Policy Evaluation
Individual projects or the full portfolio can be measured and enforced for security, operational, and licence policy compliance. - Impact Analysis
Respond quickly to detected vulnerabilities in projects impacted by susceptible components. - Time Series Metrics
For all projects and components in the portfolio, it provides trending data of inherited risk and policy violations. - Bill of Materials (BOM)
Consumes, analyses, and generates industry-standard Software Bill of Materials formats, such as CycloneDX and SPDX. - Vulnerability Aggregation
Organizations get a consolidated picture of priority discoveries thanks to native interaction with several application risk platforms. - Enterprise Ready
Supports OpenID Connect (OIDC) for Single Sign-On (SSO), as well as Active Directory and LDAP authentication. - API and Integration
API-first design interfaces readily with other systems, opening up a world of possibilities.
The major advantage of implementing Dependency Track into a company is that it is open source. Even though the software is free, there are still fees associated with hosting the programme in a production setting. Another advantage is that the application features a detailed user interface that gives it the appearance of a commercial product. Common open-source security programmes usually don't have a graphical user interface (GUI), or if they do, it's a crude one. Aside from those two benefits, Sonatype's OSS Index, which is one of the industry's most reliable open-source scanners, is a welcome addition.
CONCLUSION
Vulnerabilities in third-party components are becoming increasingly common. With the introduction of Open Source, software development has changed dramatically throughout the years. We don't have to build anything from the ground up anymore. Thousands of libraries are publicly available, considerably reducing the requirement to build features and services from the ground up. However, this poses a new risk to the company. These libraries were created by people, and people make mistakes. As a result, there are certain to be security flaws in these libraries. Some of these flaws are really dangerous.
As a result, it's critical to stay on top of things and make sure that these library vulnerabilities are identified and fixed as quickly as feasible. It's critical to have a central tool to manage these efforts, especially if you're protecting a big number of components and services, which OWASP Dependency Track excels at.