We come across the word “smart” in our daily life which directly relates to many aspects in technology. In this context, we would be covering IoT devices and its vulnerabilities. IoTs are more vulnerable as it deals more with the sensor and wireless connectivity mediums.
- Introduction
- Types Of Layers
- Physical Layer Attacks
- Software Layer Attacks
- Network Layer Attacks
- Cloud- IoT
- Privacy Concern
- Conclusion
- Last But Not The Least
- References
- You May Also Be Interested In
Introduction
We find IoT in a wide range of applications, including smart cities, control actuation and maintenance of complex systems in industry, health, transport and much more. Needless to say, IoT touches every facet of our daily lives. Security and privacy are two of the most crucial challenges that IoT is facing. Since sensor networks are highly vulnerable to cyberattacks, it is very important to have some mechanisms that can protect the network, devices and users from all kinds of attacks.
Layers
Based on the vulnerabilities in layers, we can categorize them into 3 types:
- Physical layer attacks
- Network layer attacks
- Application layer attacks
Physical Layer Attacks:
Physical layer in IoT consists of basic electronics and the communication medium connecting to the Rx. Wireless air interfaces involved in the IoT include IEEE 802.15.4 (Zigbee), Bluetooth Low Energy (BLE), IEEE 802.11 Wi-Fi, LoRaWAN, cellular connections, ultra-wide band, near field communication (NFC), radio frequency identification (RFID), to name but a few.
Here, the intruder should be in close contact with the device or needs to physically access the hardware. Example: Exploiting a router or performing an cold boot attack. As said, IoT devices behaves and works according to the data collected on its sensors, and hence they are prone to cyberattacks. Commonly used sensors in IoT from the smart home, industrial and medical point of view are tabulated.
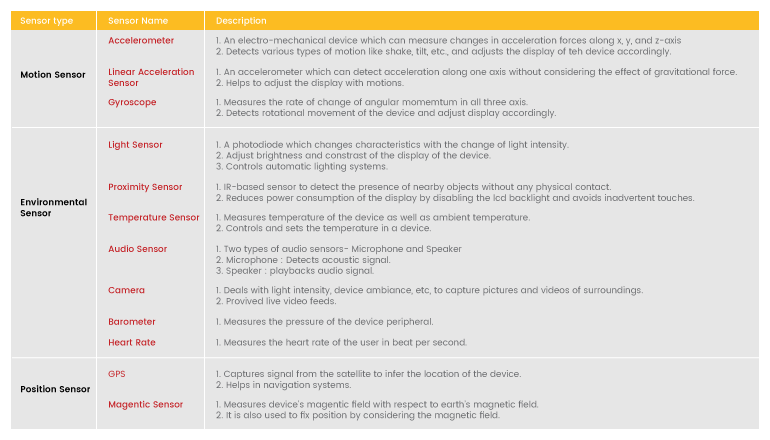
Attack on sensors
As existing sensor management systems and security schemes cannot provide adequate security to the sensors, attackers can exploit them in various ways. In general, sensor-based threats refer to passive or active malicious actions which try to accomplish its malicious intents by exploiting the sensors. Further, sensor-based threats in IoT devices can be categorized into four broad categories based on the purpose and nature of the threats.
- 1. Information Leakage
- 2. Malicious sensor patterns or commands
- 3. False sensor Data injection
- 4. DoS
1. Information Leakage
Information leakage is the most common sensor-based threat in the context of IoT devices and applications. Sensors on IoT devices can reveal sensitive data like passwords, secret keys of a cryptographic system, credit card information, etc. This information can be used directly to violate user privacy or to build a database for future attacks. Only one sensor can be enough for information leakage (e.g., eavesdropping using microphone) or multiple sensors can be exploited to create a detailed information gathering for more complex attacks. This attack leads the intruder to perform Keystroke interference, location interference and eavesdrop.
2. Malicious Sensor Patterns or commands
Sensors available in the IoT devices can be used to transmit malicious sensor patterns or triggering commands to activate malware that may have been implanted in a victim’s device. Sensors may be employed to create unexpected communication channels between device peripherals. Such channels can be used to change critical sensor parameters. This leads to transmitting malicious information via light intensity, magnetic field, e.t.c.
3. False Sensor Data Injection
False sensor data injection refers to an attack where the sensor data used in the IoT applications is forged or forcefully changed to perform malicious activities. The false sensor data can be injected in the devices by accessing the device physically or by using various communication medium(Bluetooth, Wi-Fi, cellular network, etc.) covertly. Moreover, the sensors of IoT devices can also be used to alter data type that are stored on the devices.
4.Dos
Denial-of-Service (DoS), by definition, is a type of attack where the normal operation of a device or application is denied maliciously. DoS attacks can be active attacks where an application or task is refused forcefully or passive attacks where attacking one application can stop another on-going task on the device. Attacks on Accelerometer and MEMS sensor can be a useful resource.
Prevention Techniques:
- The usage of a wide range of sensors in IoT devices and applications has made it hard to secure all the sensors by one effective framework.
- Furthermore, the lack of knowledge of the existing sensor-based threats and differences in sensor characteristics make it hard to establish a complete and comprehensive security measure to secure all the sensors of IoT devices against the sensor-based threats.
- One approach toward securing the sensors in IoT devices is to enhance existing sensor management systems of IoTOses.
- Also, with semadroid, users can specify policies to control whether and with what level of precision third party apps can access to sensed data.
- Moreover, Semadroid creates mock data to verify how applications, from unknown vendors, use sensed data and thus, prevents malicious behaviors.
Software Attacks:
Software attacks are usually performed by the intruder by injecting malware content either through the website access or by adware. These malware can also be botnet which can be used to damage the application at the admin level.
IoT malware refers to the class of malware that targets IoT devices, mainly embedded devices built upon a variety of CPU architectures, including MIPS, ARM, and Power PC. This class of malware relies on the nature of IoT devices that come with limited system resources and where security mechanisms usually are neglected.
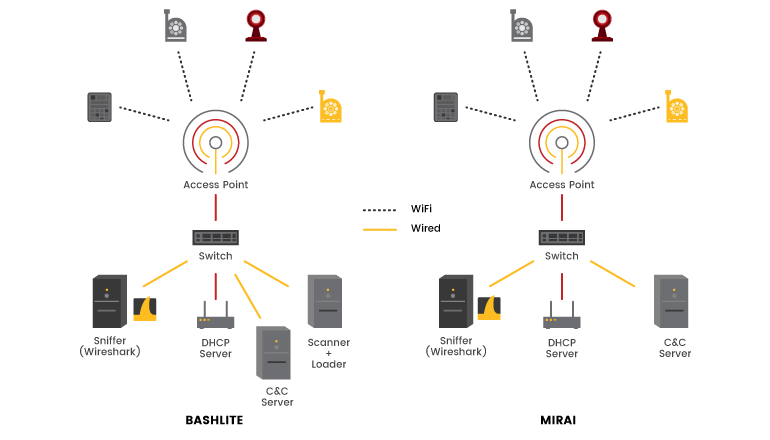
Despite dealing with constrained devices, IoT malware can be sophisticated. More recently, few malware families have implemented anti-analysis techniques, code obfuscation, and system conditional behavior. Mirai, for example, observes the system aspects before contacting the botnet C&C. If the requirements are not satisfied, the malware pretends to connect to a fake C&C, preventing the real one from being disclosed. Multiple variants monitor the system running processes looking for a set of process names associated with well-known malware in order to neutralize a potential rival and save the limited shared resources.
Mirai and Bashlite are developed particularly to create large-scale botnets designed to launch different types of volumetric attacks. Most of the IoT devices are connected using Upnp configurations which makes an added advantage to the botnets. In fact, those malware functionalities are common in diverse malware families, including the most notorious Mirai and Bashlite. In the next section, we underline the functionalities of those families that were used in our case study.
How To Prevent It?
The security of IoT devices poses a significant threat to the Internet, since most of these devices do not implement the best security mechanisms to protect them from abuses. An increasing number of malware has explored the vulnerabilities of these devices to perform powerful attacks. Hence, to protect systems from such malware and improve the mechanisms of defense, it is essential to characterize the malware behaviors. Visit our case study on how we approach to the problem.
Network Layer Attacks:
These types of attacks occur in the network layers whenever the devices are connected to the network. This makes much easier for the intruder to access the device information, if we fail to provide proper authentication. Hence to understand this clearly, we can use the concept of RFID (Radio-Frequency Identification) card mostly in case of access.
In most of the cases, RFID intrusion is done by the following methods:
- RFID SPOOFING
- RFID CLONING
- RFID UNAUTHOURIZED ACCESS
RFID Spoofing:
It captures the transmitted information from the RFID tag using NFC (Near-Field Communication). Now, the intruder gains access to the unauthorized area which is restricted for the intruder/3rd party sources. Here, the major drawback is, it even accepts the wrong data.

RFID Cloning:
This part is entirely different from the spoofing part. In this, the intruder needs an RFID card in hand so that he can reverse the hardware from that card and can clone a similar type to that. Once done, it could be used to add this as a user to the network in which the original card is connected. Finally, by using the cloned card, the intruder can gain the entire access.
RFID Unauthorized Access:
This is the final stage of attack. This occurs only when the device connected to this is either authorized freely (without credentials) or weakly authorized (default passwords) by the user. If the intruder gains access to this device via network, adding and removing the users from the node can be done. This results in adversity for the employees. Also, many confidential data can be leaked over the network which would add fuel to the fame.
Cloud- IoT
We are moving into the digital era and people hesitate to spend time for upgrading the hardware which also even if they have enough money for it. This not only saves time but also some space they occupy. Smart cities which are deployed in the world are working on the cloud concepts in which they use to replace the physical sensor into virtual one. From this user can control the real devices from his phone using minimum hardware constraints for accessing the device. Recommendations for the secure built up of cloud IoT systems,
- Access control of IoT using trusted platform module for device identification and configuration access control.
- In-cloud data protection.
- Apply TLS certificates at the infrastructure level.
- Use industry-specific protocol filters.
Privacy Concern
As we all know IoT devices are always connected which opens the door for the hackers to exploit the devices all time. These devices always used to collect information’s from the user and showcase it back to them on the go. Smart wearable devices like watch, headsets, and wireless earphones collects information from the user which they won’t care about. Case study of the wearable IoT devices paper states that NEST thermometer and NIKE band collects information's like Temperature, Humidity, Ambient light data, infrared processed data, and the last manually modified data by the user. This same information is passed through mobile phones, which also leads to exposure of data if compromised.
Manufactures in IoT domain test the devices on a ultra basics level as there are no common standards present. Some key points to the manufactures that are suggested by Bint labs are
- U-Boot should be followed.
- Manufacture should not disclose any debug ports.
- Microcontrollers should be pre-programmed at the initial stage.
- Collection of users data should be minimized.
- Use open-sourced and proprietary techniques to safeguard your customer data.
- Proper cryptographic implementations should be followed at each layers of IoT.
- Use several in-build checks for the Microcontroller.
Conclusion:
There are certain things that you cannot take it for granted. To be more upfront, you can never take them for granted. One such thing is cybersecurity. You sleep with the complacency of having absolutely secured data today, you will wake up as a hacking victim tomorrow. Further, securing and maintaining privacy for your IoT devices environment consistently with the right practices is mandatory. Hence, a proper and complete security assessment on all these layers should be regularly done.
Resources
You May Also Be Interested On
- Beware your unused modem/hardware can leak your critical data
- Security challenges in react and interact