Organizations face multiple cybersecurity dangers in the digital age, which could compromise confidential information, disrupt operations, and harm their brand. Strong security measures must be implemented to secure digital assets and ensure business continuity.
Although compliance the security standards and laws are critical, it is also critical to go beyond compliance and continuously identify and reduce security threats.
Vulnerability Assessment and Penetration Testing (VAPT) is an important component of a complete strategy for cybersecurity that assists organizations in accomplishing this goal.
On its counterpart hand, a penetration test takes things one stage higher by implementing actual attacks on the IT systems and infrastructure of an organization. Professional hackers try to use loopholes to get access without authorization and carry out destructive actions.
Organizations can find vulnerabilities through the use of controlled and authorized attacks that may not be picked up by automated scanning software.
Why do Businesses Need VAPT?
VAPT is used to identify security threats and risks that are present in the IT system of your business. These flaws provide attackers with accessibility to the computer software and technology tools used by your company, opening the door to security risks and information thefts.

Every organization that maintains its own network has to perform such VAPT evaluations to determine whether its systems are vulnerable. These configurations leave these businesses constantly vulnerable to cyberattacks since they are unable to recognize future threats.
The existence of these flaws in the networks they run devices, websites, Internet of Things devices, and Android applications must thus be measured and identified by these organizations.
How about businesses without a committed and efficient security measures team to deal with such vulnerabilities? Briskinfosec has the ideal answer for you for that. We collaborate with the greatest cybersecurity suppliers in the world and provide a wide range of services at unbelievable costs. Our experts will be pleased to assist you if you require more than just security services. Within set timelines.
Why VAPT is essential for a company's privacy
Uncover Hidden Vulnerabilities:
VAPT helps uncover vulnerabilities that may go undetected by standard security measures. It goes beyond surface-level security checks and provides a comprehensive assessment of potential weaknesses in your systems, networks, and applications.

Proactive Risk Management:
Organizations may effectively detect and reduce security threats with VAPT before attackers take advantage of them. Organizations may resolve bugs in their systems and dramatically reduce the risk of sustaining digital attacks by routinely identifying vulnerabilities and conducting penetration testing.
Keep Ahead of Emerging Threats:
In the always-changing cybersecurity environment, VAPT puts you in the lead. It enables you to put proactive safeguards into place and keep ahead of possible attackers by assisting you in identifying possible vulnerabilities and new attack methods.
Stages of Pen Testing
Pre-engagement phase
Establishing the full scope of the attack assures that both the intended victim and the tester are aware of the test's objectives. Specific assets are authorized to be tested by the security engineer; these are within the boundaries of the testing, while others are not.
Likewise, the goal company's defensive position is assessed against a predefined list of threats; anything outside of that group is not covered by the Security engineer. The depth of the testing has a significant impact on all future security assessment stages.
Discovery
The primary phase entails carrying out several kinds of reconnaissance on the chosen target. Naturally, technical details like IP addresses can be used to identify precise information regarding connectivity and firewalls.
Personal details like names, job titles, and email addresses, however, can also be quite important in this case.
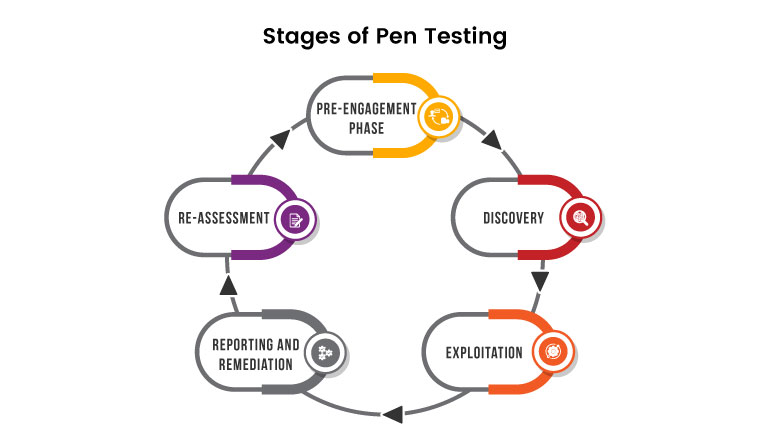
Exploitation
Once we have gathered sufficient data about the target, they will commence with the attack, which will allow them to breach the specified environment. It assists in exploiting security flaws by proving its ability to reach a specified depth of the network's infrastructure.
Reporting and Remediation
This Report describes how we began testing, how we discovered vulnerabilities, and how we exploited them. It also provides the extent of the security testing, the POC, the findings, and Their proper remediation.
Re-Assessment
Finally, retesting is the greatest way to ensure your company's safety as a whole. It assists in determining the amount and presence of security concerns that were overlooked during the procedure. In addition, retesting shows remaining vulnerabilities and allows the user to identify the new vulnerability earlier.
Conclusion
In conclusion, VAPT is essential to your company's security because it reveals concealed vulnerabilities, enables forward-thinking risk mitigation, offers real-world testing, ensures compliance, improves readiness for incident response, safeguards trust and reputation, and keeps up with new threats.
By doing this Organizations may dramatically improve their security posture, safeguard their priceless assets, and maintain a resilient cybersecurity posture in the face of emerging dangers by moving beyond the scope of compliance and using VAPT practices.


