Contents:
- Introduction – Internet of Things
- IoT Architecture
- Thinking of privacy and security
- IoT Security and Privacy Threats
- Building a secure foundation for IoT
- Recommendations for securing IoT
- Conclusion: Building way for a smart and securely connected world
- How Briskinfosec helps you?
- Curious to read our case study?
- Last but not the least
- You may be interested on
Introduction - Internet of Things:
In todays world, each and every device is metamorphosing into digital and all these devices are being connected with other devices for aiding mankind. This automatically denotes the Internet Of Things (IOT) which is the centre of storm in today’s technology and for sure, also the future that is broadening the horizons of technology. Internet of Things is an ability of daily objects to connect to internet and exchange information with one another. To be said in a more trivial way, it’s the “Digitalization of the physical world”. For example, a person can open their home doors for their beloved ones after seeing them on a smart video camera itself through the internet. The following features cited below will be covered in this blog:
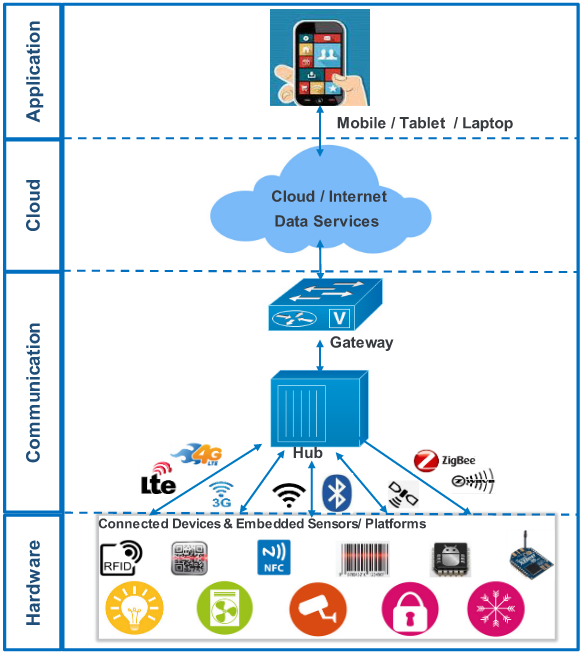
IoT Architecture:
IoT architecture can be classfied into four categories:
- Hardware
- Communication
- Cloud
- Application.
There are some models, which are used to connect devices in different scenarios.
Device to Device:
This model is commonly used in simple solutions such as home automation, where it uses small data packets of information with less data rate within the devices. Those devices are light bulbs, light switches, door locks and so on.
Device to Cloud:
In this model, the devices are connected directly to the internet cloud service. Example: An application service provider to exchange data.
Device to Gateway:
In this model, the device will act as an intermediary between two devices.
Thinking of privacy and security:
In today’s world, technology has become universal and integrated into our daily lives, expanding the security consideration to personal consideration, financial transaction, and cyber thefts such as identity theft, hacking, phishing, data theft, keylogging, denial of service, operating system attack, etc. If any of the mentioned risks are present, the IoT devices and services will notify the potential vulnerability point to an attacker which leads to user data theft. But nowadays, cyber criminals are targeting the organizations and particular individuals through techniques such as Denial-of-Service (DoS) attacks, Distributed-Denial-of-Service (DDOS) attacks, Industry Control System attacks (ICS), Cross-Platform Malware (CPM) attacks etc. These attacks have become highly sophisticated, hence are more difficult to control.
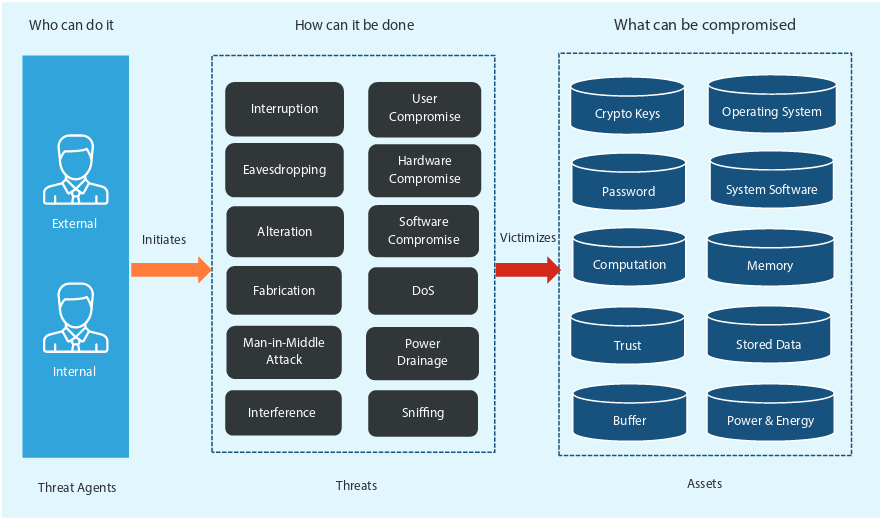
IoT Security and Privacy Threats:
Device & Hardware:
- Insecured external ports and network access.
- Unauthorized access.
- Lack of security configuration.
- Malicious software updates.
- Outdated devices.
Cloud:
- Attacks on unsecured Cloud interface.
- In-cloud data leaks.
- SQL-injection.
- SSL/TLS configuration.
- Outdated devices.
Communication:
- Vulnerable server over an unsecured network.
- Low-level transport encryption.
- DDoS.
- Open ports via UPnP (Universal Plug ‘n’ Play).
Application:
- Low-level security configuration.
- Unsecured password recovery.
- Attacks on unsecured mobile or PC and application.
- Lack of role-based access.
- No applications or password lockouts.
- Collection of unwanted personal data and sharing over the network.
Common problems in IoT:
The maturity of IoT technology is interconnected with today's devices such as laptops, smart watches, mobile WiFi-enabled cameras and so on. In 2018, several IoT developments have been implemented, such as the network design IoT malicious pattern recognition and embedded artificial intelligence algorithm design.
The fundamental common problems of the Internet of Things are, it increases the number of devices behind our network firewalls. Ten years ago, we were worried about how to protect our computers. Five years ago, we were concerned about how to protect our mobile phones. But now, we need to worry about how to protect our cars, home appliances, wearable and many more devices. The reason is, there are so many number of devices that are vulnerable to hacking. You would’ve heard about hackers exploiting the cars remotely, and then accelerating or decelerating them after gaining access. Hackers also focus on some trivial devices such as baby monitors or thermostat for gaining your private information. Here, the major point is that, we need to think what an attacker can do to ruin our lives with a device if he/she can break through it’s security features.
Penetration Testing:
Assessing the organization's IoT implementations requires testing of hardware and software, and must include regularly scheduled penetration testing activities as well as independent tests that occur throughout the cycle of operation.
Conducting a IoT penetration testing isn’t too different from a traditional one. The ultimate goal is to find and report the vulnerabilities that will eventually be exploited. Penetration testing is done, either as a white box or black box testing. However, both these types of tests are recommended. While black box testing is used to simulate an outside attacker, white box test provides a more thorough evaluation that allows the testing team to engage the technology in finding weaknesses completely.
IoT system testers should always look for low-hanging items that are left exposed. These include the following:
- Default passwords used in IoT devices or the gateways, servers, other Hosts, and networking equipments that support them.
- Default cryptographic keys used in IoT devices, the gateways, or services that supports them.
- Well known default configurations that would open a system up to enumeration if not modified (for example, default ports).
- Insecure pairing processes implemented on IoT devices.
- Uncertain firmware update processes on devices and within the infrastructure.
- Unencrypted data streams from IoT devices to gateways.
- Non-secure RF (Bluetooth, ZigBee, Z-Wave, and so on) configurations.
Building a secure foundation for IoT:
Networks in IoT are very complicated, so securing every element bridging from IoT devices that are connected to the cloud layer is very important. All the elements present have to work together to provide end-to-end atmosphere. Otherwise, the attacker could easily find the weakness and then exploit it.
Based on the security and privacy threats mentioned in the previous section, we can conclude that the IoT has a different and unique needs of security when compared to traditional systems.
Recommendations for securing IoT:
Here are the recommendations for securing IoT which are discussed below:
Device & Hardware:
- Secure device booting.
- Securing sensors.
- Role-based access control.
- Granular permission model.
- Next-generation firewall.
- Gateway Security.
- Encrypted on time updates and patches.
- Securing outdated devices.
Cloud:
- Access control of IoT using trusted platform module for device identification and configuration access control.
- In-cloud data protection.
- Apply TLS certificates at the infrastructure level.
- Use industry-specific protocol filters.
Communication:
- Secure services.
- Incorporate IPS and traffic inspection services in Firewalls.
- Transport encryption for data at rest in motion using SSH, SSL, FIPS, and ISO 27001 standards.
- Monitoring security logs.
- Rate based Intrusion Prevention Systems (IPS) can help in prevention against attacks.
Application:
- Secure application development by using testing techniques and safe coding practices.
- Use scanning tools like ZAP (Zed Attack Proxy).
- Secure application.
- Device Lockout for unauthorized access.
Conclusion: Building way for a smart and securely connected world:
To notice the real usage and potential of this technology, security and privacy concerns must be addressed effectively. All the self-regulation policies, structured and well-defined cybersecurity policies as well as the privacy policies must be developed and implemented swiftly with active collaboration between government and enterprises. This will pave the gateway for entering into a smart and securely connected digital world!
How Briskinfosec helps you?
Instead of sparkling in the scarlet sky as a cyber victim, it is best to always have a proactive approach before the cyber attacks strike. Hence, the need for a proper cyber security provider arises. Briskinfosec provides top notch IoT security assessment on all your IoT devices/ services, and eliminates the vulnerabilities lurking in them. We have an expert team of security professionals whom possess vast experience in doing successful IoT security assessments. Feel free to approach us anytime and experience the ecstasy of working with Briskinfosec, the company that won the India Book of Records, as well, listed as one among the top 20 most promising cyber security providers.
Curious to read our case study?
Our stakeholder, one of the leading IoT device manufacturer, wanted us to provide a complete security assessment on all their IoT devices and applications. As per their request, we performed a complete security assessment, identified the security flaws and eliminated them. Read our case study to perceive a complete sight on the way we did it.
Last but not the least:
What makes a mall so unique when compared with individual shops? Well, everything we need with various varieties can be obtained from a single place unlike small shops, where we’ve got to roam here and there. Similarly, we prepare Threatsploit Adversary reports on a monthly basis. It’s a single report that contains significant accumulation of worldwide cyber attacks, the impacts they’ve caused on the organizations, the assests companies lost, and much more. Instead of wasting time by wandering spotlessly to know about the globally occurred cyberattacks, just a single click on our report is immeasurably better.
You may be interested on:


